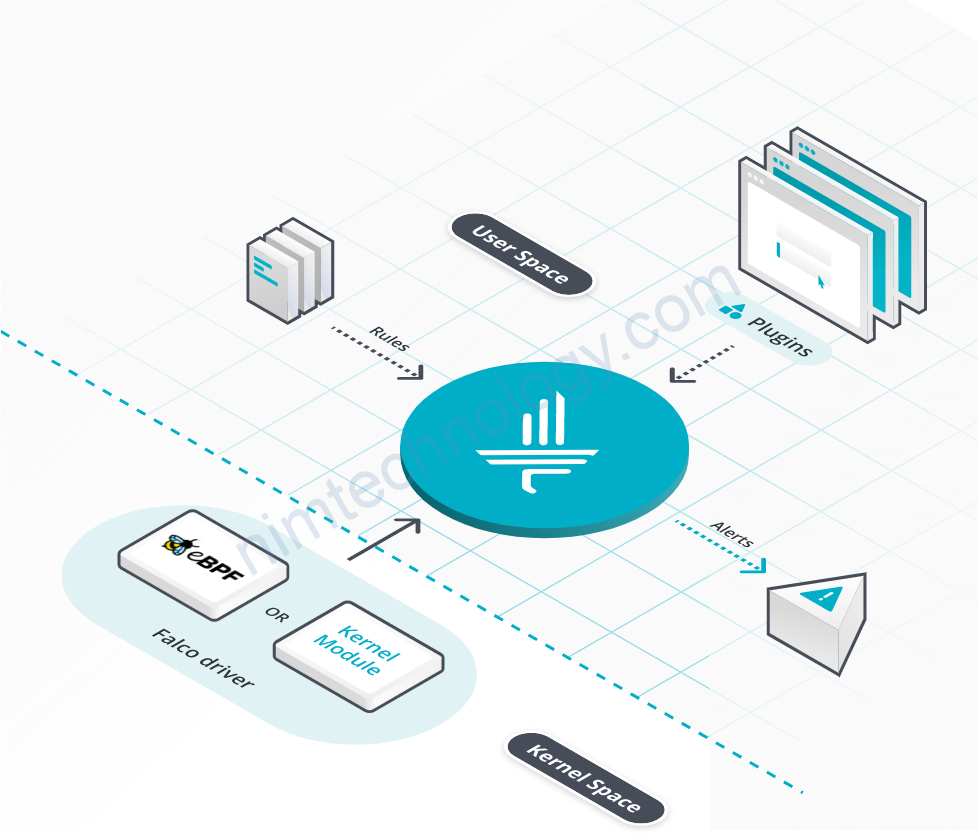
Falco, the open-source cloud-native runtime security project.
Falco detects unexpected application behavior and alerts on threats at runtime.
It has complete container visibility through a single sensor that allows us to gain insight into application and container behavior.
Falco is based on rules that will trigger alerts when conditions are met, for example Falco is by default able to detect when:
- A shell is run inside a container
- A server process spawns a child process of an unexpected type
- A sensitive file, like /etc/shadow, is unexpectedly read

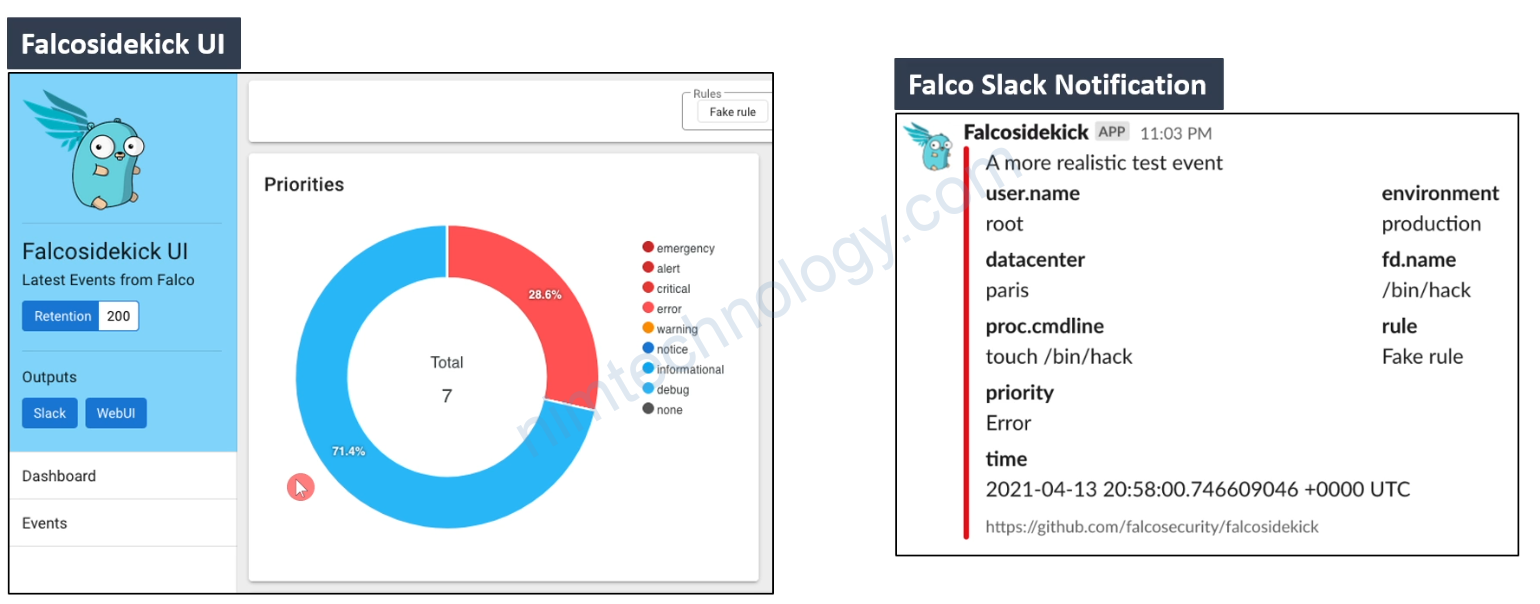
Extend Falco outputs with falcosidekick
By default, Falco has 5 outputs for its events: stdout, file, gRPC, shell and http.
These can be integrated with other components using falcosidekick, a daemon that extends that number of possible outputs.
Falco Installation
kubectl create namespace falco helm repo add falcosecurity https://falcosecurity.github.io/charts helm install falco falcosecurity/falco \ --set falcosidekick.enabled=true \ --set falcosidekick.webui.enabled=true \ --set falcosidekick.config.slack.webhookurl="https://hooks.slack.com/services/XXXX" \ -n falco
--set falcosidekick.enabled=trueenables deployment ofFalcosidekickasideFalcoand configuresFalcofor sending its events toFalcosidekick--set falcosidekick.webui.enabled=trueenables deployment ofFalcosidekick-UIand configureFalcosidekickfor using it as output--set falcosidekick.config.slack.webhookurl="https://hooks.slack.com/services/XXXX"enablesSlackas output forFalcosidekick
Bạn có thể tìm hiểu link này
https://falco.org/blog/extend-falco-outputs-with-falcosidekick/
Giờ mình thực hiện test bằng cách cách mình run command trong 1 container.

Và đây là event bắt được trên falco UI