Kubernetes Anonymous Users
Let’s uncover the details of Kubernetes 💥anonymous users and how 💥RBAC tooling works with anonymous access.
By default, every request to the Kubernetes API that isn’t otherwise associated with a specific user is treated as coming from an anonymous user. This can be startling at first glance, with some wondering if this is a security vulnerability. But fear not, it’s all by design, and it’s a fundamental part of Kubernetes’ role-based access control (RBAC) system.
By Default – Anonymous Users
These are the commands that can be used with anonymous access by default:
curl -k $SERVER/version curl -k $SERVER/healthz
🔱 The testing environment was a kubernetes 1.24 using kind, details Here →
curl -k $SERVER/version
{
"major": "1",
"minor": "24",
"gitVersion": "v1.24.15",
"gitCommit": "2c67202dc0bb96a7a837cbfb8d72e1f34dfc2808",
"gitTreeState": "clean",
"buildDate": "2023-06-15T01:09:03Z",
"goVersion": "go1.19.10",
"compiler": "gc",
"platform": "linux/amd64"
}
curl -k $SERVER/healthz
ok%
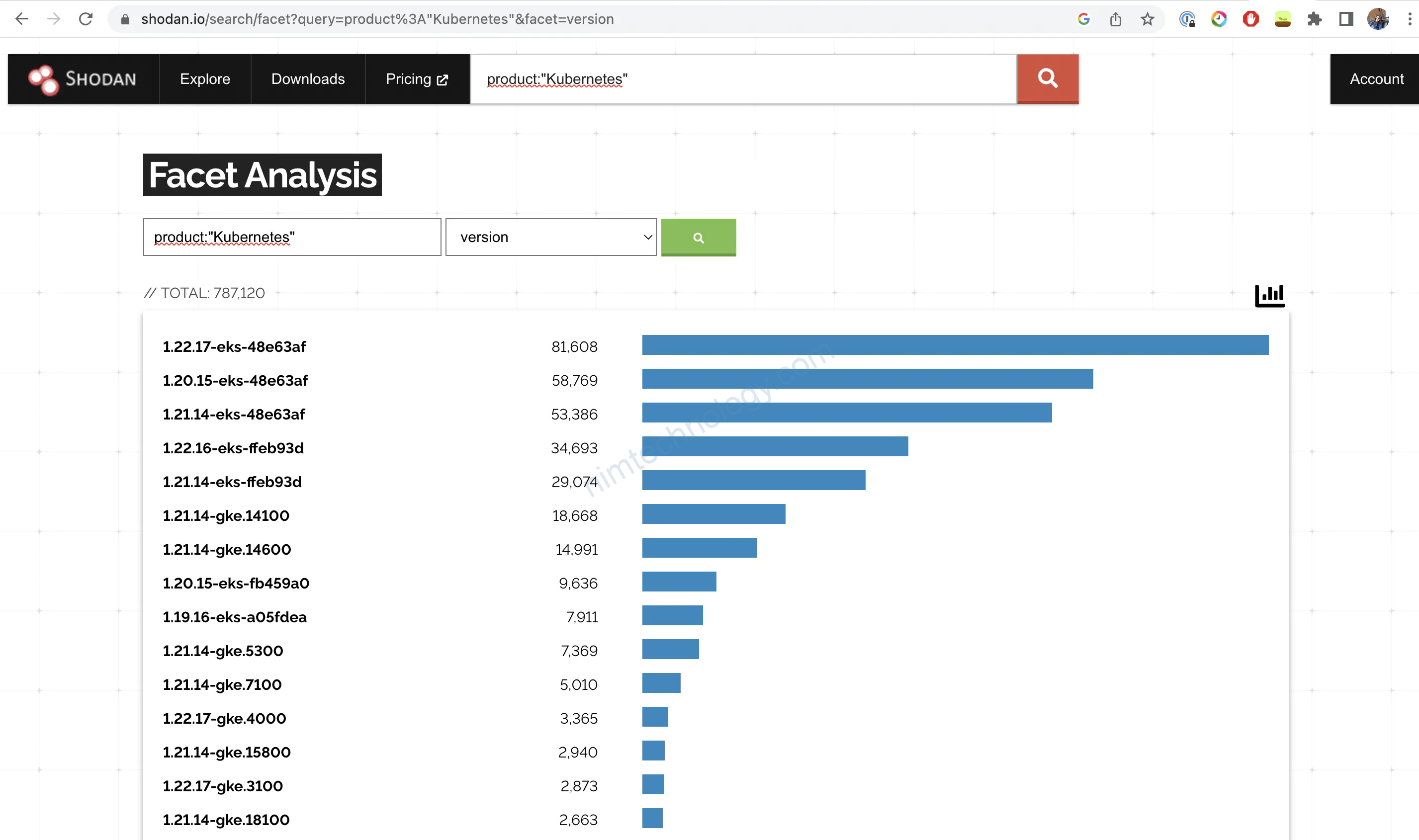
Let’s get some statistics about Kubernetes versions exposed on the internet
Using search engines, we can track all the kubernetes version:
Using Shodan.io
Using Censys.io
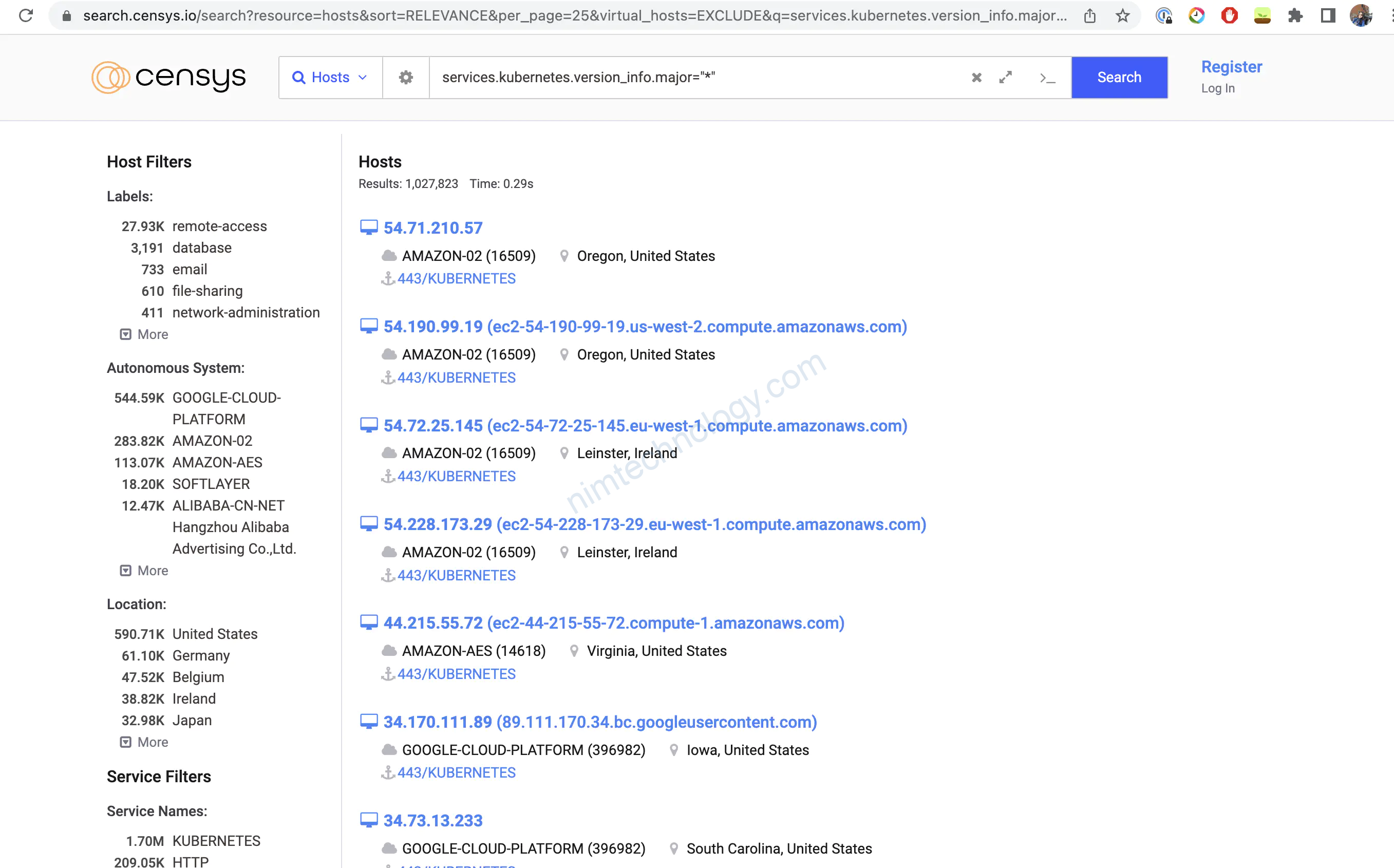
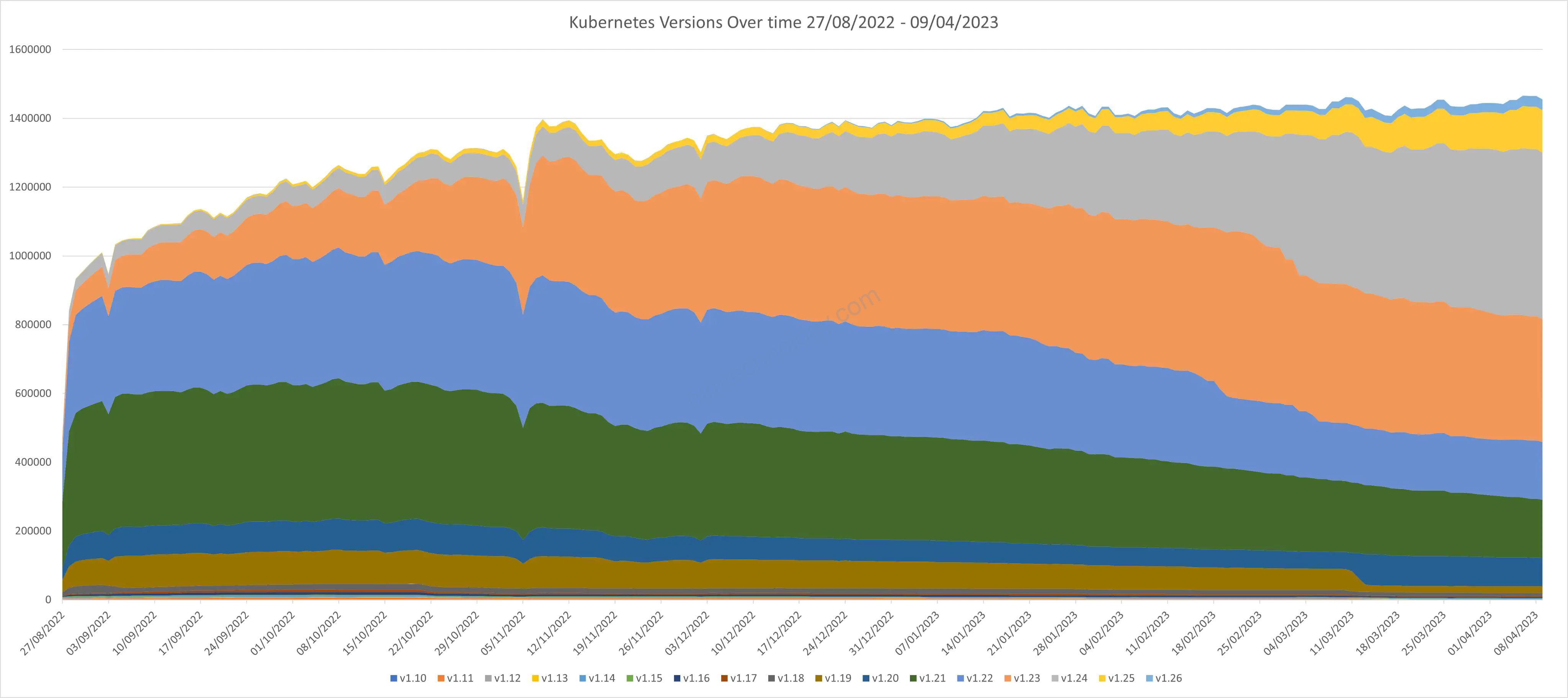
Image by @raesene, follow the link for more about anonymous →
Kubelet Authentication Authorization
Vulnerable Kubernetes clusters with authentication set to –anonymous-auth=true, allowing anyone anonymous access to the Kubernetes API.
Turning off Anonymous Requests
There might be situations where you’d want to disable anonymous requests entirely for more stringent security. That’s entirely doable by setting the –anonymous-auth=false flag on the API server. However, it’s worth noting that this could impact components and features that rely on anonymous access, so ensure you understand the implications before making this change.
The setting
anonymous-auth=is inside the default config file /var/lib/kubelet/config.yaml
Read more in the Kubelet Kubernetes Documentation → and Kubelet Authentication Authorization →
Adding permissions to the user anonymous – Don’t do it !
RBAC in Kubernetes provides the framework for authorizing API requests based on the user’s role.
By default, the anonymous user doesn’t have any permissions. However, admins can grant permissions to anonymous users by binding roles to the 💥system:anonymous💥 group or the 💥system:unauthenticated💥 group, which includes all anonymous users.
Remember, roles define the permissions, which include actions like read, write, and execute, and these are bound to a user through role bindings.
For instance, you might want to allow anonymous users to list the pods in a particular namespace to keep an eye on your cluster’s health. To do that, you would create a Role with the appropriate permissions and then bind it to the system:unauthenticated group.
Before Permission
k get pods --as=system:anonymous Error from server (Forbidden): pods is forbidden: User "system:anonymous" cannot list resource "pods" in API group "" in the namespace "default"
Adding Permission
kubectl create clusterrolebinding anonymous-xdemo --clusterrole=view --user=system:anonymous
After Permission
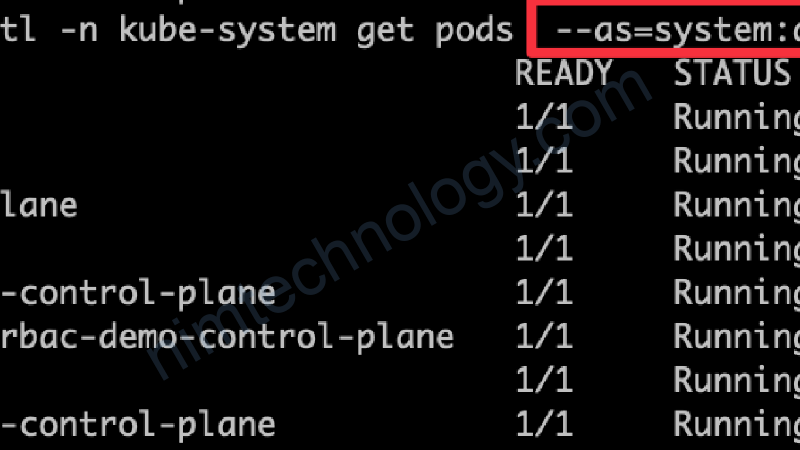
kubectl get pods -A --as=system:anonymous NAMESPACE NAME READY STATUS RESTARTS AGE kube-system coredns-57575c5f89-5j9n2 1/1 Running 1 (21h ago) 35h kube-system coredns-57575c5f89-h7zbn 1/1 Running 1 (21h ago) 35h kube-system etcd-rbac-demo-control-plane 1/1 Running 1 (21h ago) 35h kube-system kindnet-rxqsm 1/1 Running 1 (21h ago) 35h kube-system kube-apiserver-rbac-demo-control-plane 1/1 Running 1 (21h ago) 35h kube-system kube-controller-manager-rbac-demo-control-plane 1/1 Running 1 (21h ago) 35h kube-system kube-proxy-dsbhz 1/1 Running 1 (21h ago) 35h kube-system kube-scheduler-rbac-demo-control-plane 1/1 Running 1 (21h ago) 35h local-path-storage local-path-provisioner-c49b7b56f-t48qf 1/1 Running 2 (21h ago) 35h
Kubernetes RBAC Tools
Exploring the reports searching for the risk of the anonymous user in the Kubernetes cluster.
It was added the anonymous permissions and the tools were executed to find the risk of this configuration.
🔱 The testing environment was a kubernetes 1.24 using kind, details Here →
Finding anonymous-xdemo clusterrolebinding in the tools report
| Krane |
|---|
| 🚫 Not found alert for anonymous user with permissions, issue open here💥. |
| Krane output report here ✍🏿 |
 |
| KubiScan |
|---|
| ✅ Found an alert for anonymous user with permissions, issue open here – done💥. |
KubiScan output report here ✍🏿  |
| Kubescape |
|---|
| 🚫 Not found alert for anonymous user with permissions, issue open here – WIP💥. |
Kubescape output report here ✍🏿  |
| Rbac-Police |
|---|
| 🚫 Not found alert for anonymous user with permissions, issue open here 💥. |
Rbac-Police output report here ✍🏿  |
| AWS-GuardDuty |
|---|
| ✅ Found an alert for anonymous user with permissions. |
AWS-GuardDuty report detail coming 💥  |