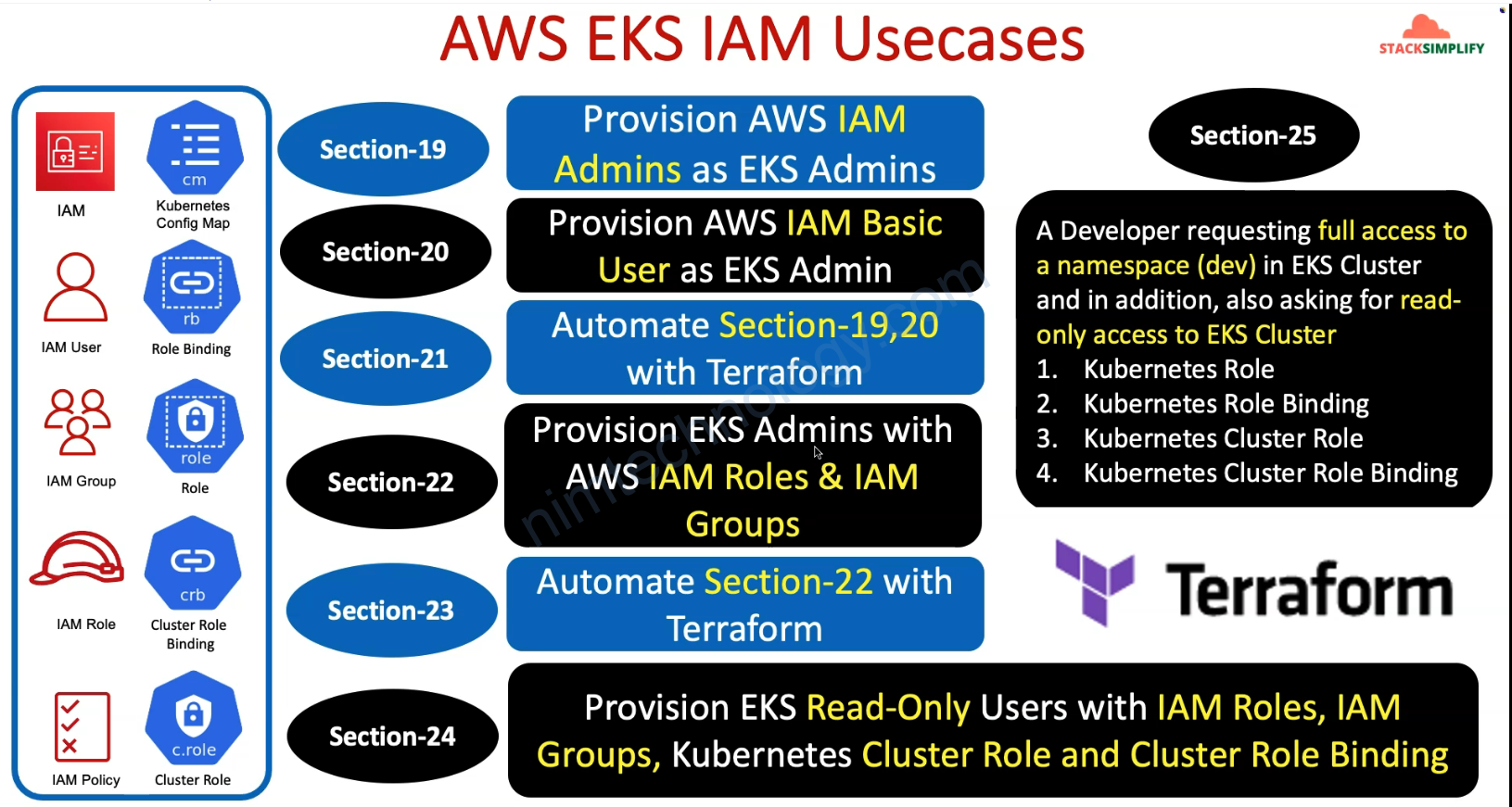
1) Overall EKS IAM Introduction.


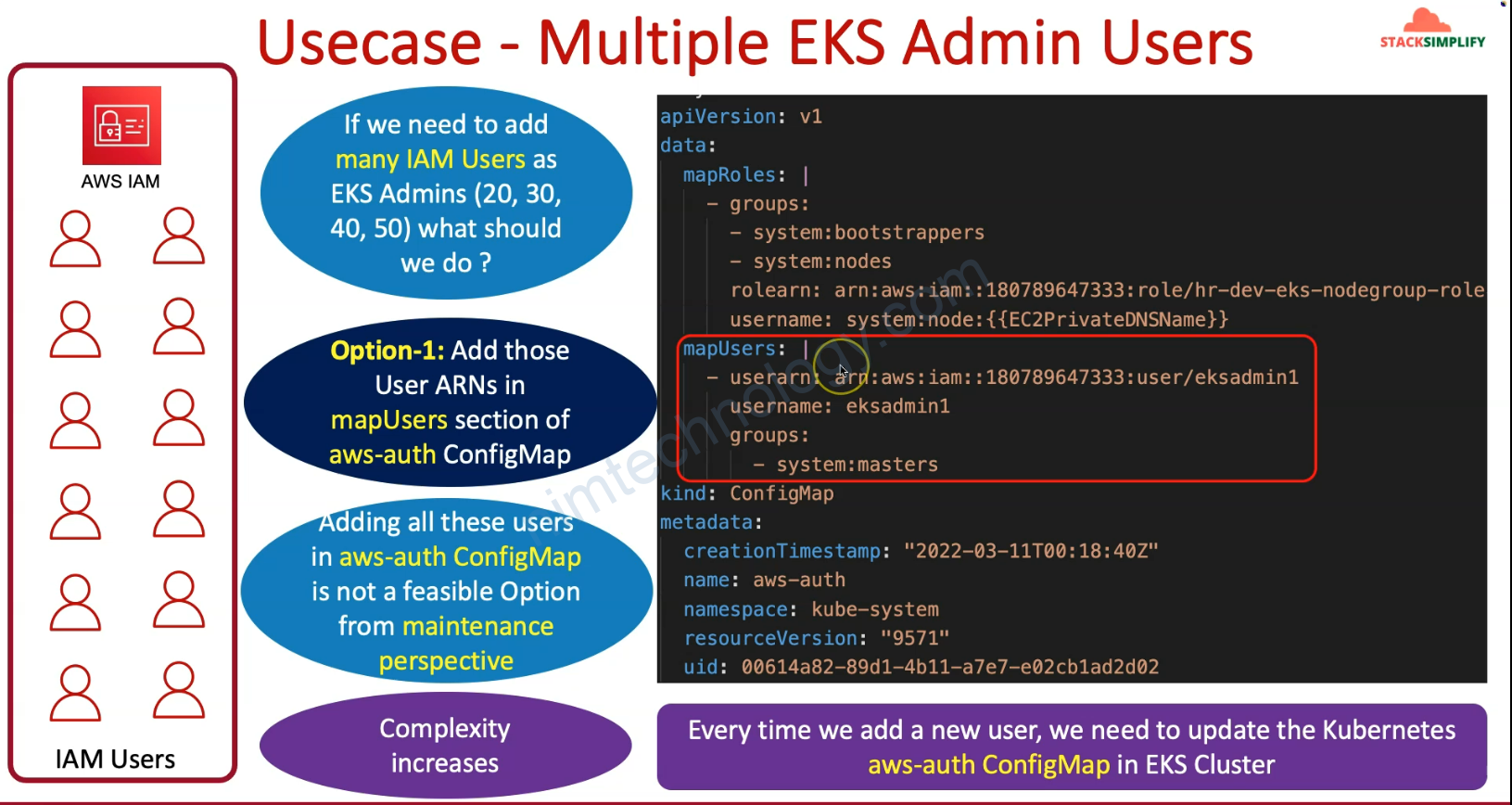
Bạn sẽ cần adjust configmap aws-auth

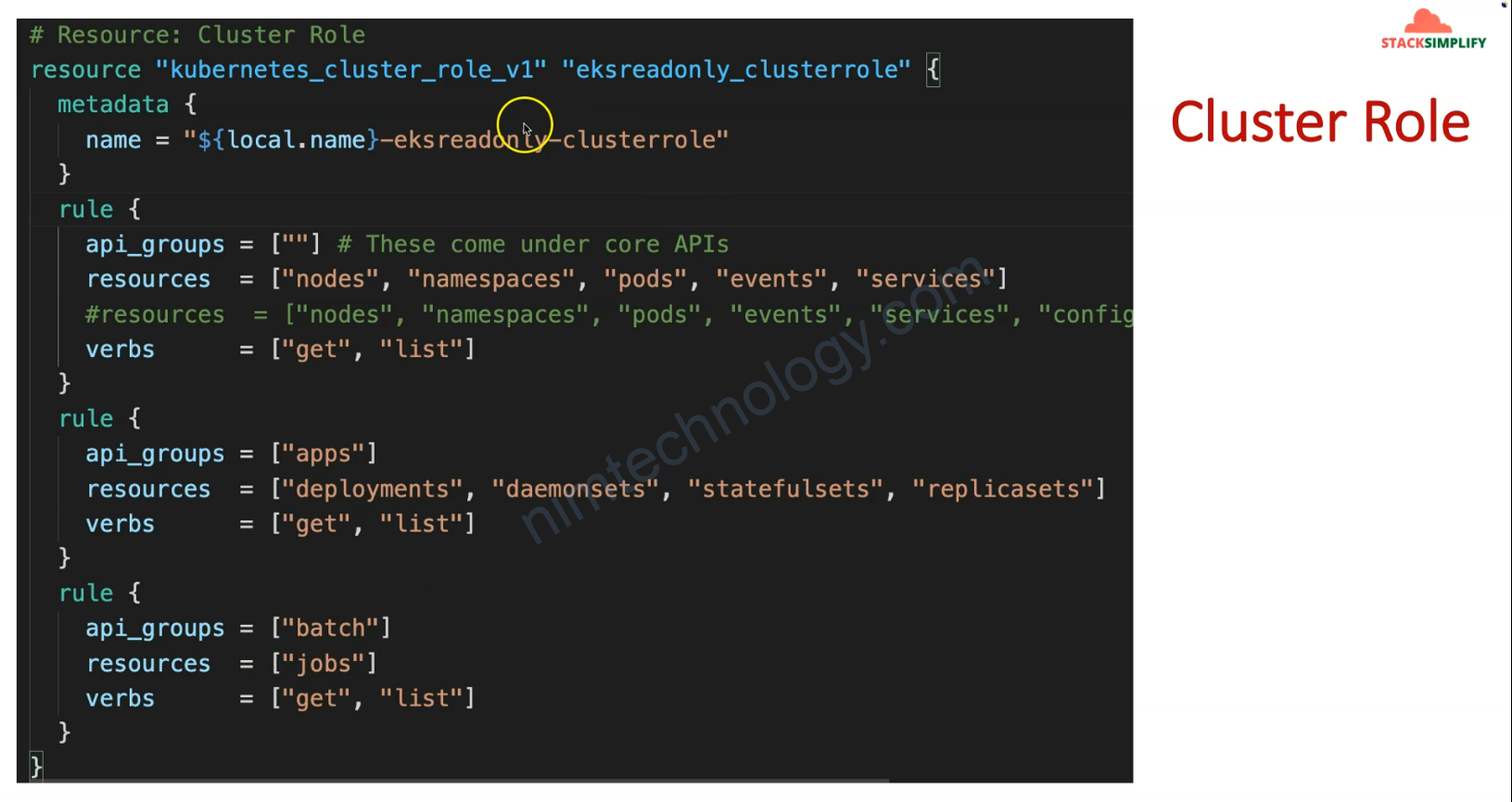

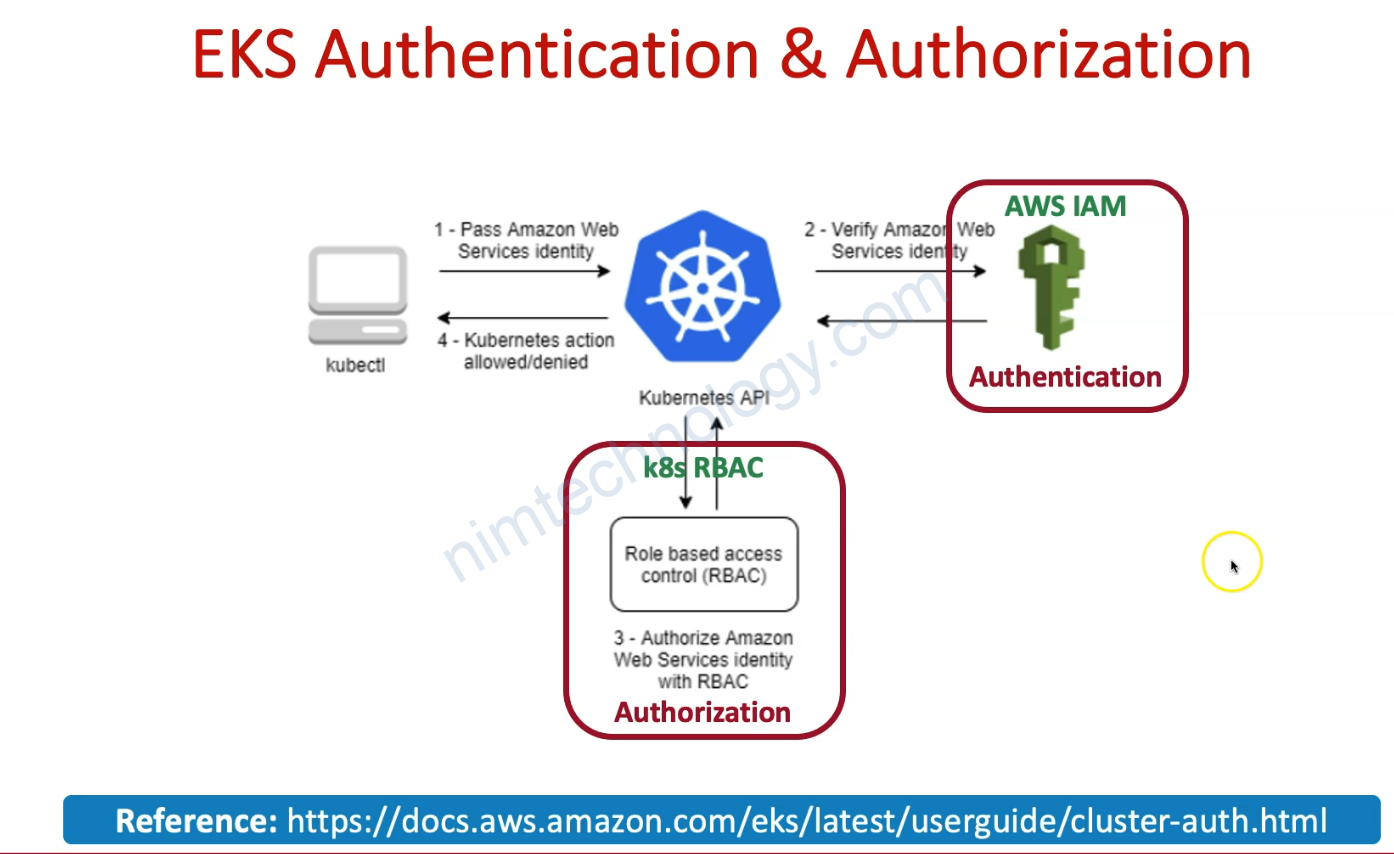
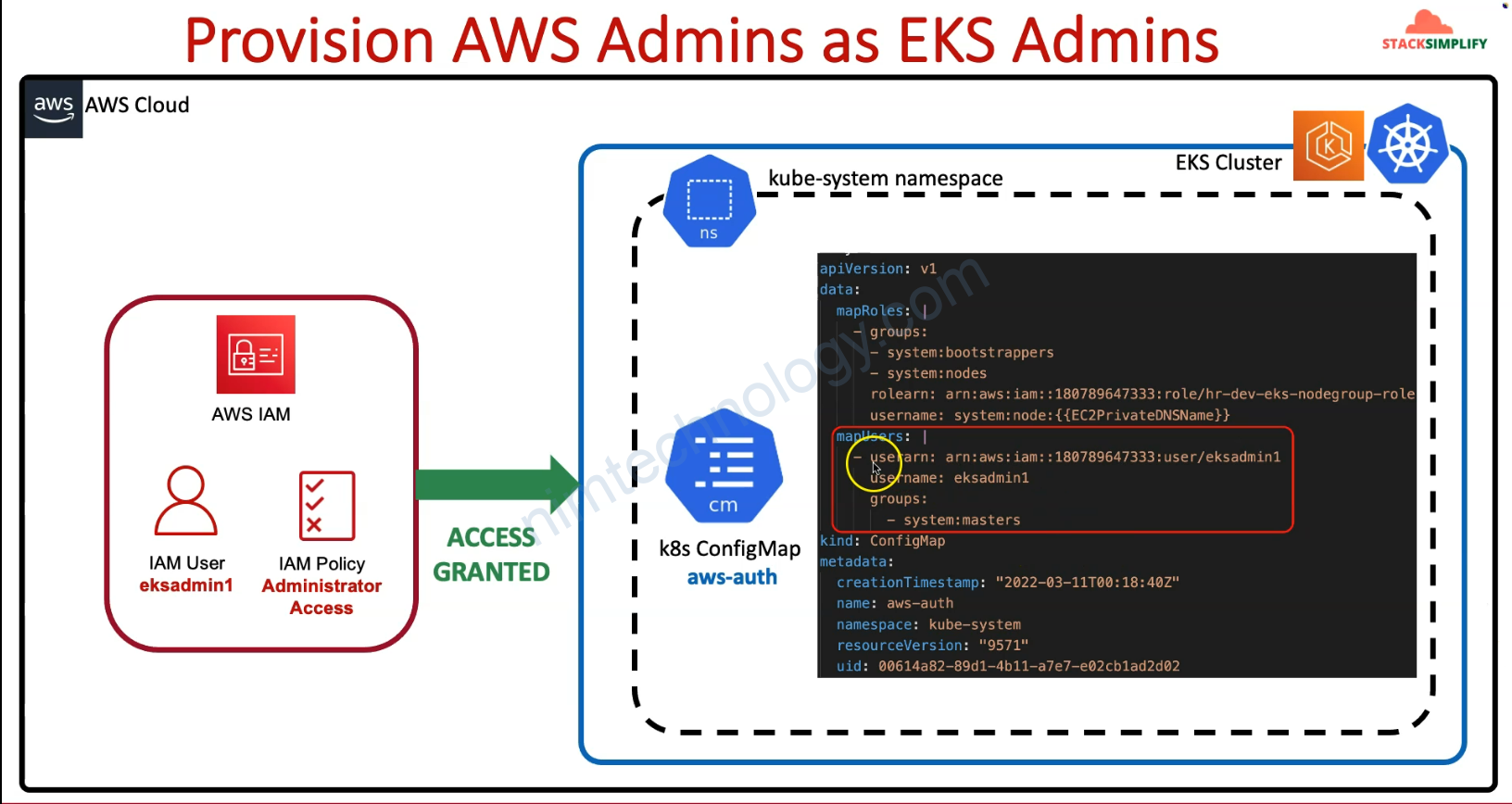
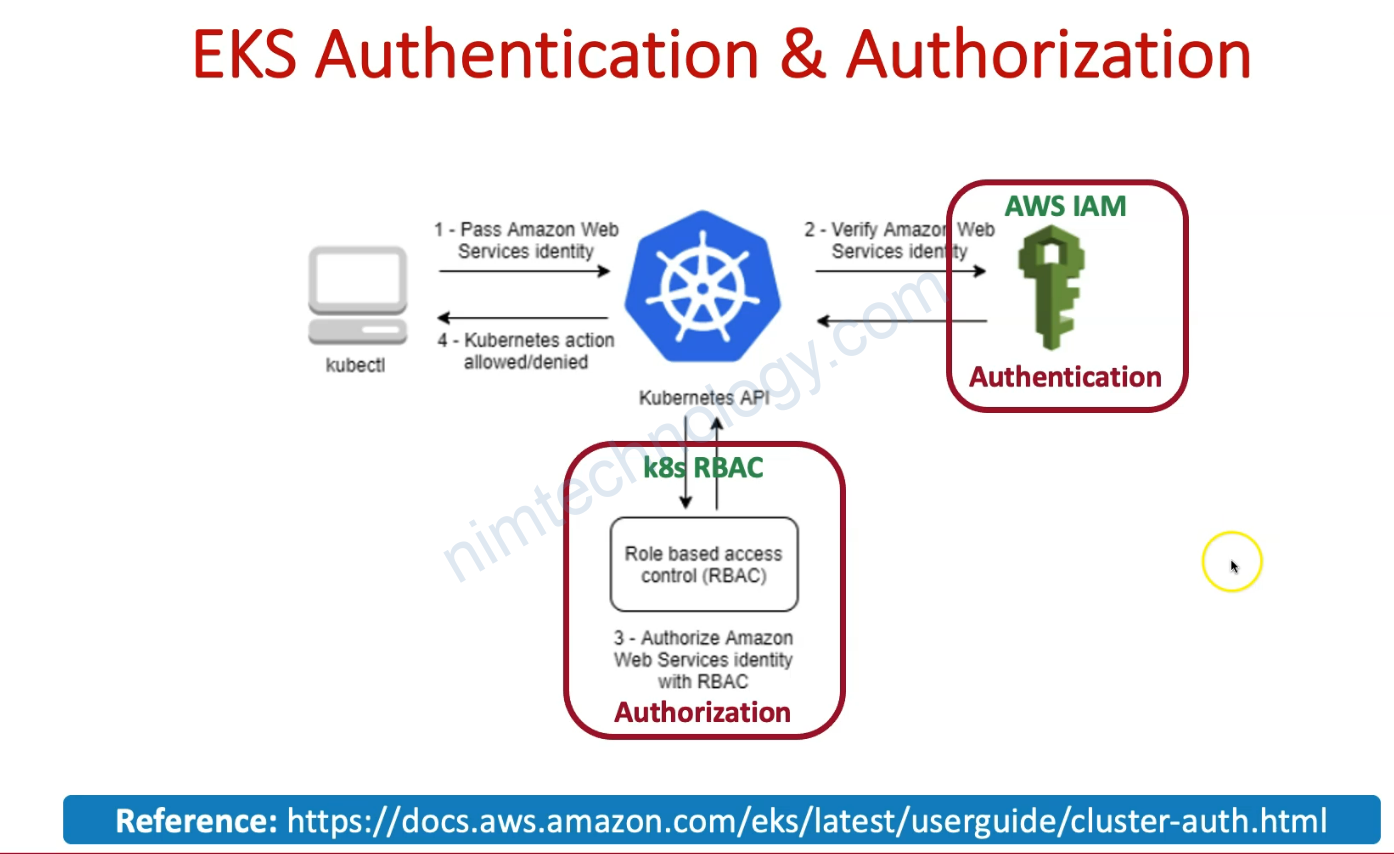
2) Understand AWS EKS Authentication & Authorization
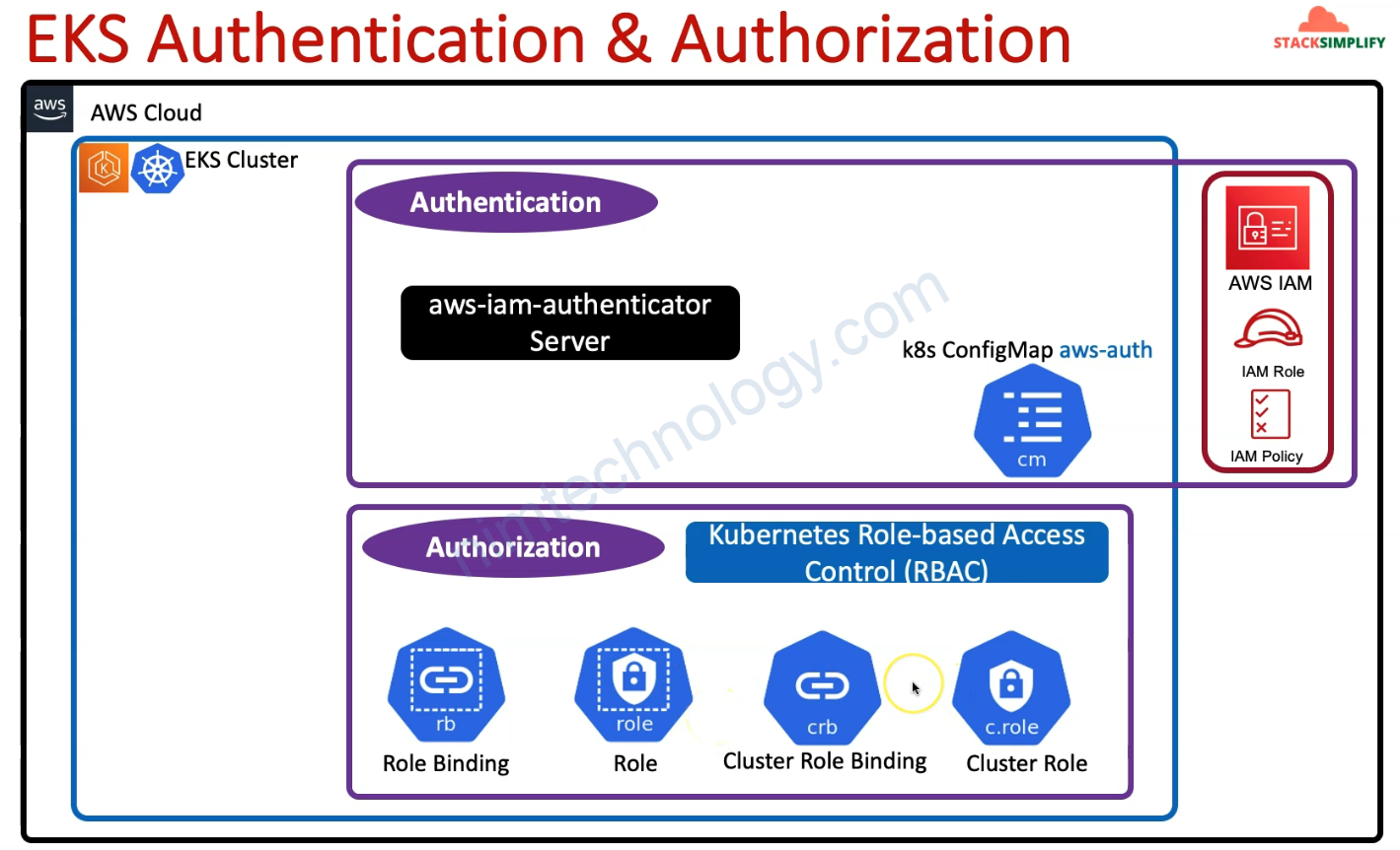
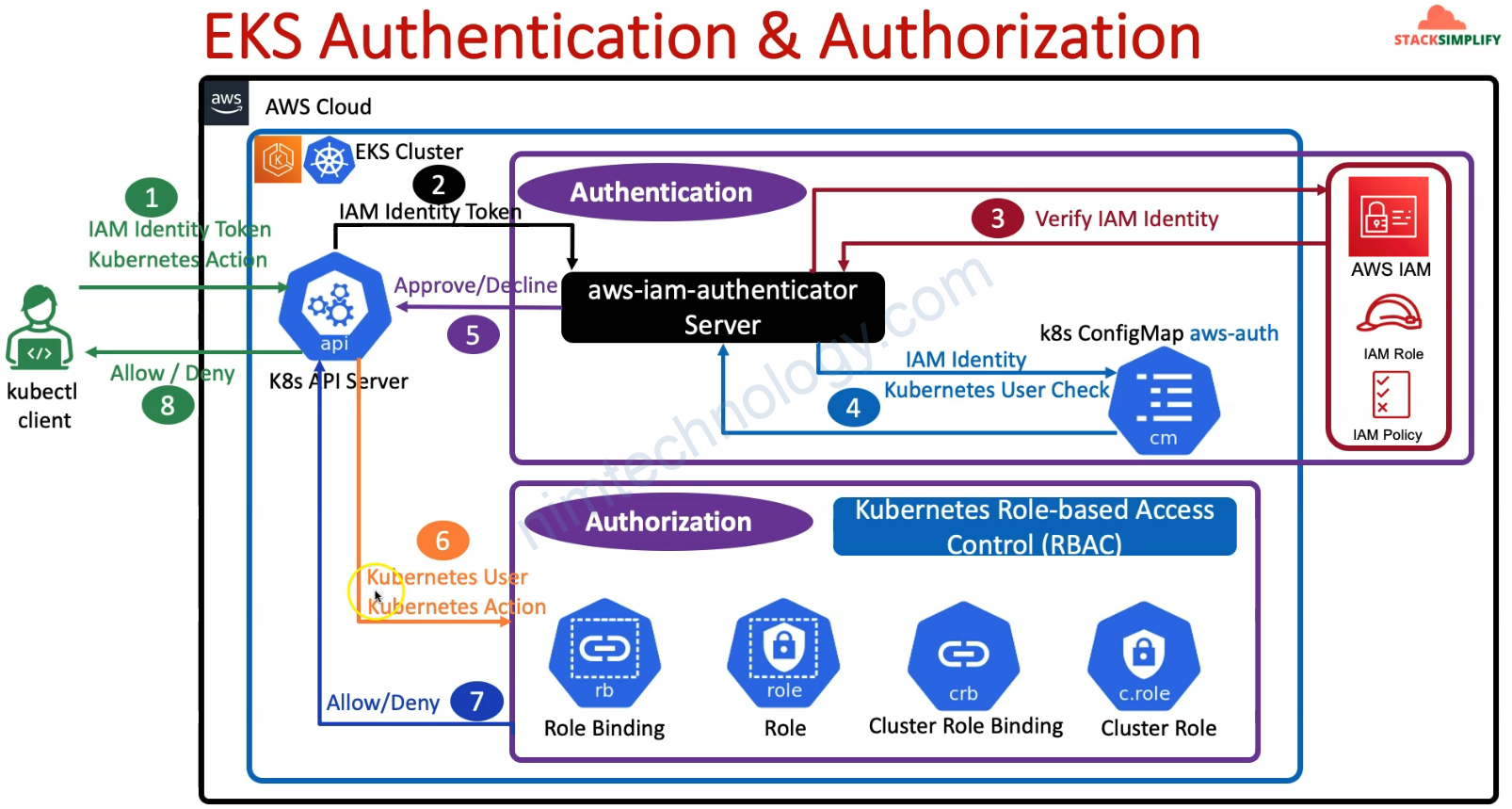
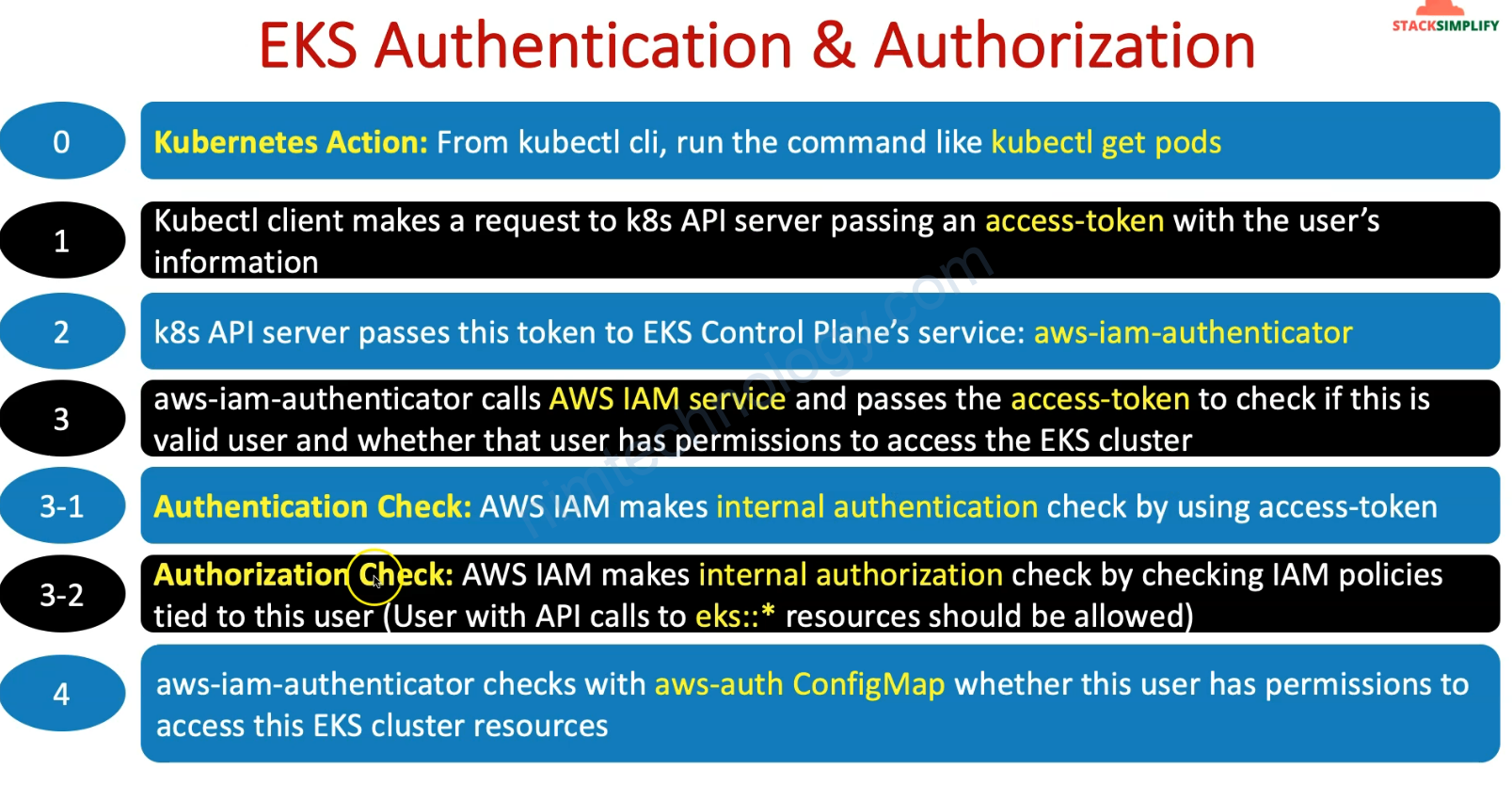
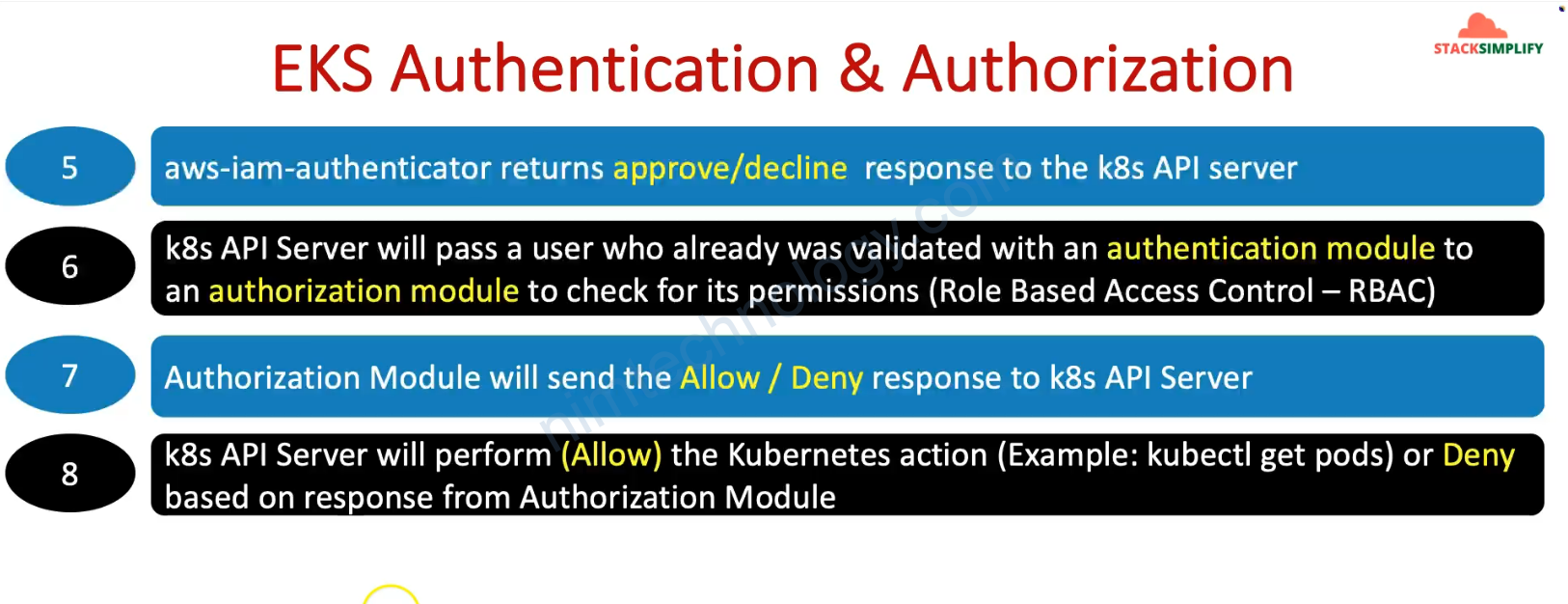
3) Understand about EKS Cluster Creator User
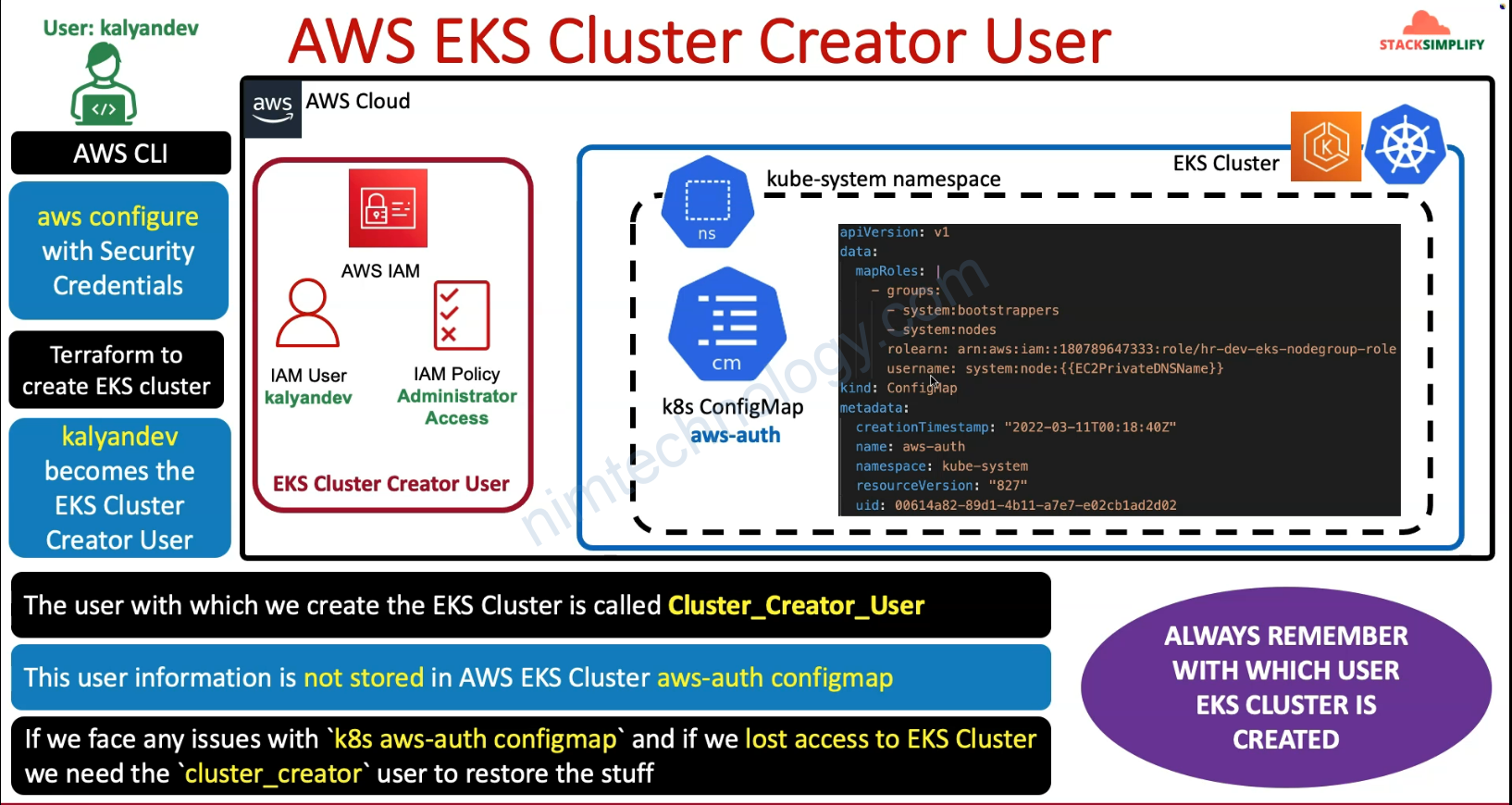
Để create 1 cluster EKS
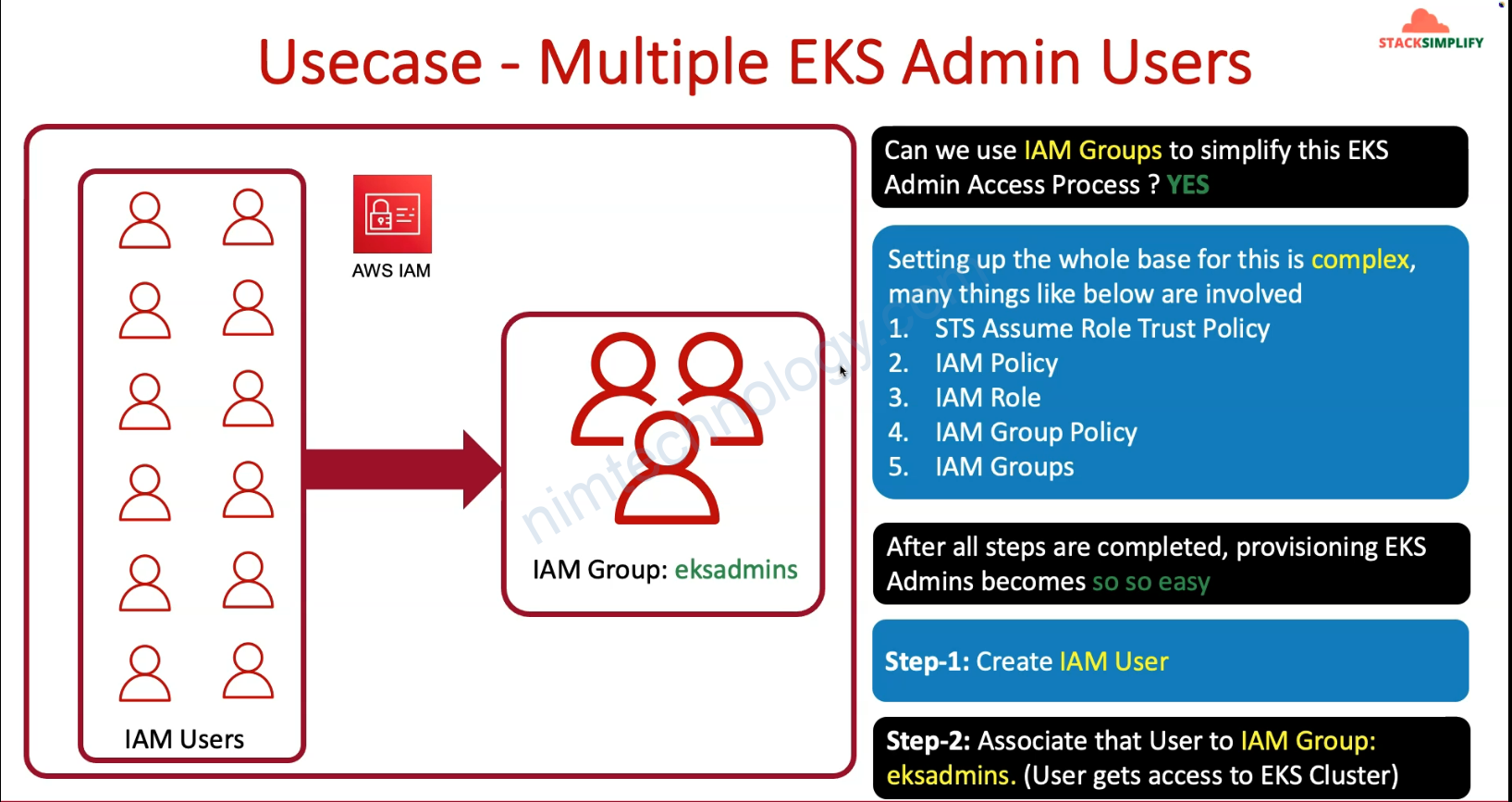
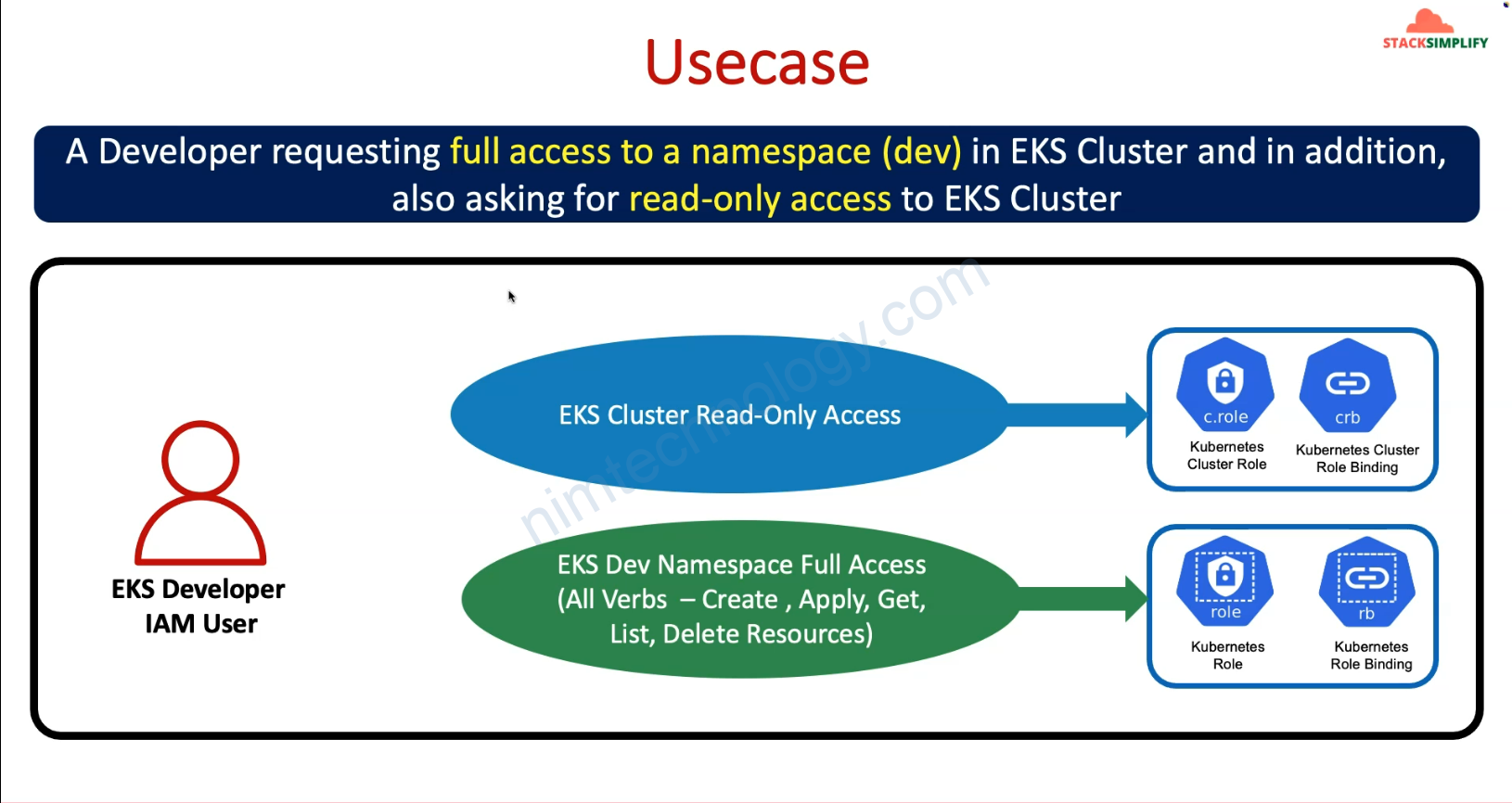
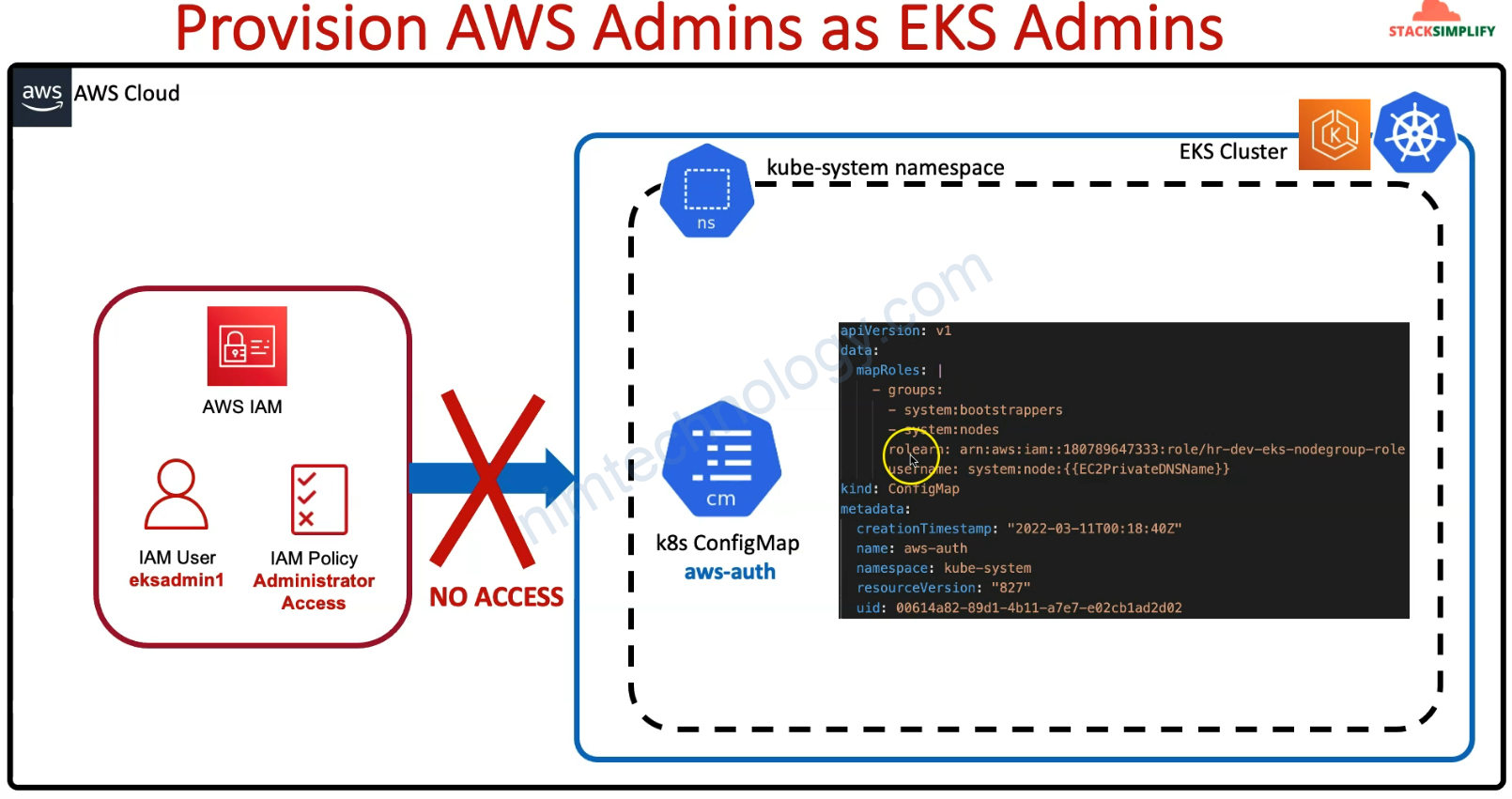
4) Introduction to Provisioning AWS Admin as EKS Admin
Tiếp theo giờ bạn có 1 user eksadmin1 có quyền Administrator Access nhưng mà nó sẽ ko thể gõ kubeclt
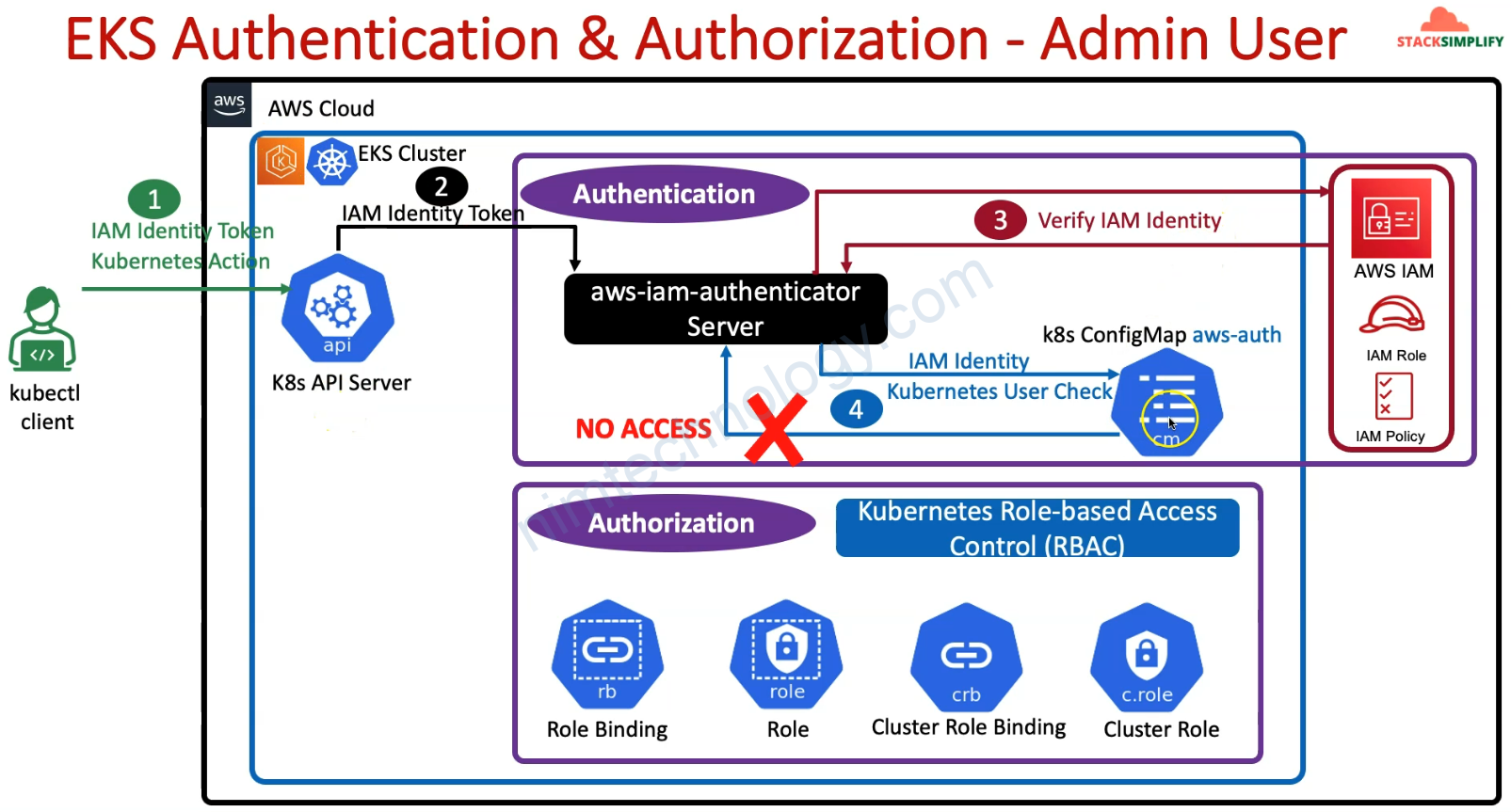
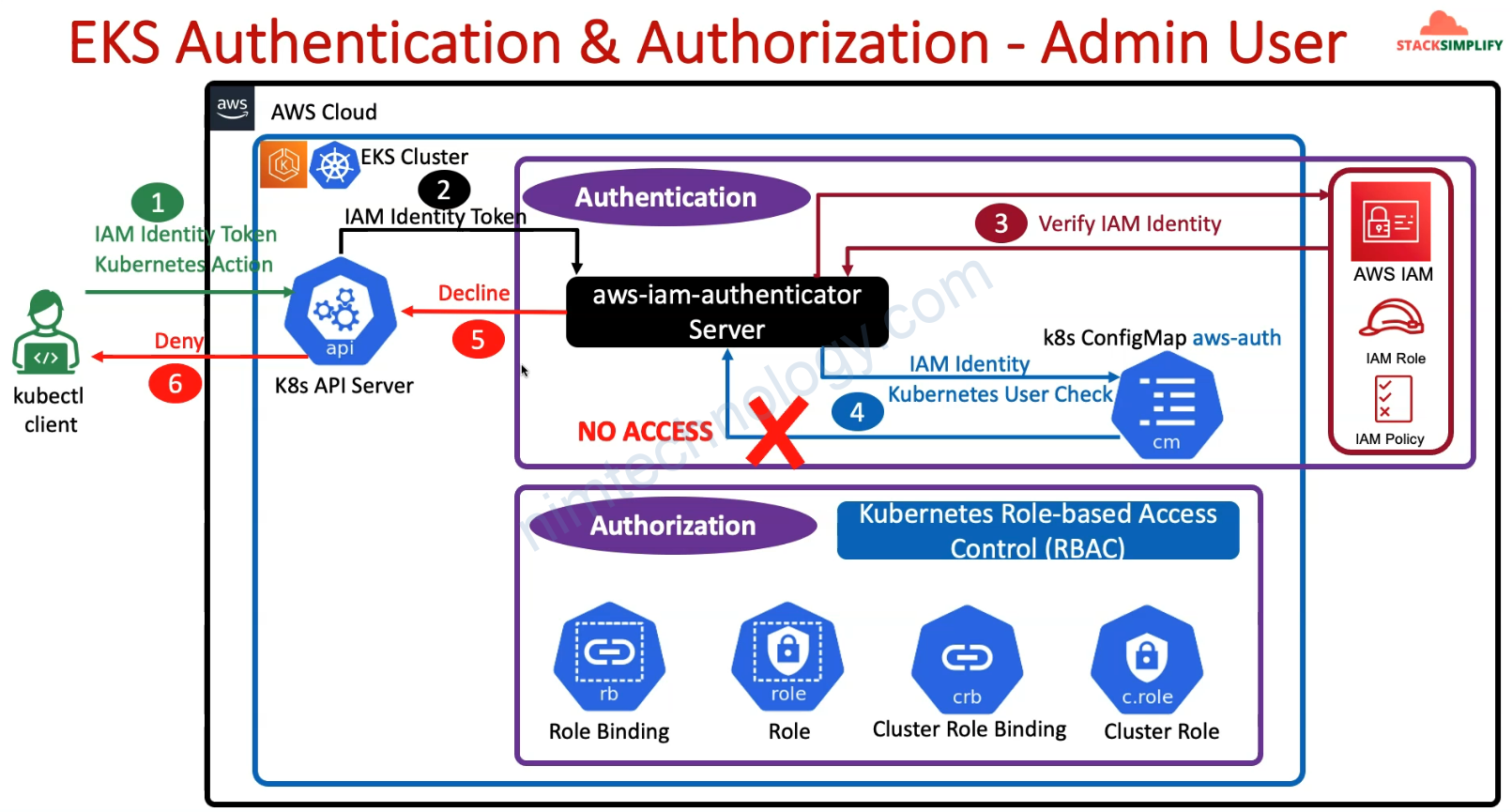
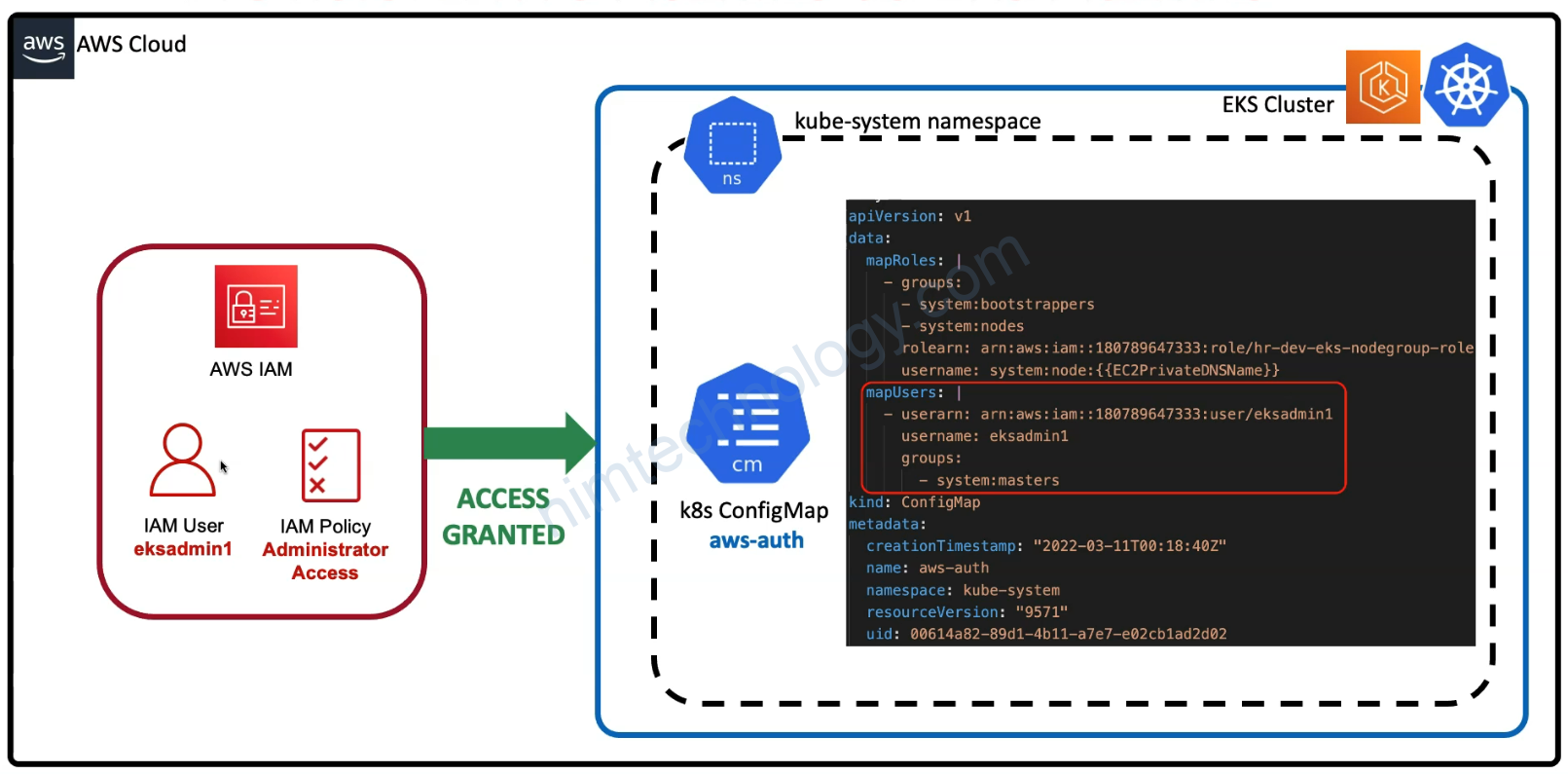
sau đó eksadmin1 có thể gõ kubectl
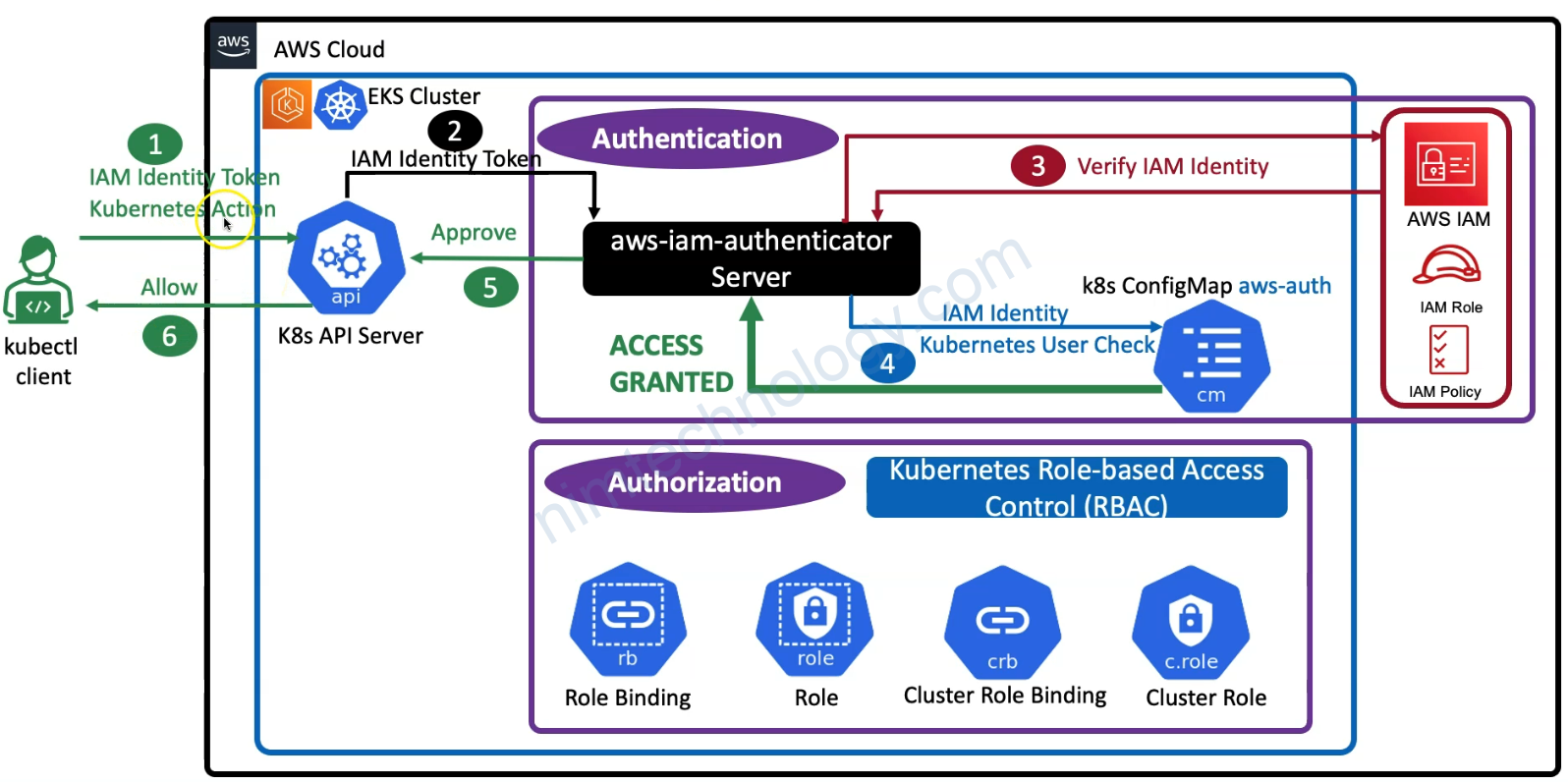
5) Create IAM User and AWS CLI Profile
Đầu tiên là mình đã tạo được 1 cluster eks
và mình gõ command tạo user eksadmin1
root@LP11-D7891:~# aws sts get-caller-identity
{
"UserId": "AIDATU2QSHIISHPLW6PRV",
"Account": "250887682577",
"Arn": "arn:aws:iam::250887682577:user/nim"
}
Yeah! giờ tạo user
# Create IAM User
aws iam create-user --user-name eksadmin1
# Attach AdministratorAccess Policy to User
aws iam attach-user-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --user-name eksadmin1
# Set password for eksadmin1 user
aws iam create-login-profile --user-name eksadmin1 --password @EKSUser101 --no-password-reset-required
# Create Security Credentials for IAM User and make a note of them
aws iam create-access-key --user-name eksadmin1
# Make a note of Access Key ID and Secret Access Key
User: eksadmin1
{
"AccessKey": {
"UserName": "eksadmin1",
"AccessKeyId": "AKIASUF7HC7SYK3RO727",
"Status": "Active",
"SecretAccessKey": "WQEf+lTcucoaKZt4EDnZmXm5VzqLkFLVWQaJxHiH",
"CreateDate": "2022-03-20T03:19:02+00:00"
}
}
# To list all configuration data aws configure list # To list all your profile names aws configure list-profiles # Configure aws cli eksadmin1 Profile aws configure --profile eksadmin1 AWS Access Key ID: AKIASUF7HC7SYK3RO727 AWS Secret Access Key: WQEf+lTcucoaKZt4EDnZmXm5VzqLkFLVWQaJxHiH Default region: us-east-1 Default output format: json # Get current user configured in AWS CLI aws sts get-caller-identity Observation: Should see the user "kalyandev" (EKS_Cluster_Create_User) from default profile
>>>>aws eks --region <region_name> update-kubeconfig --name <eks_cluster_name> --profile <profile_name> root@LP11-D7891:~# aws eks --region us-east-1 update-kubeconfig --name SAP-dev-eksdemo --profile eksadmin1 Added new context arn:aws:eks:us-east-1:250887682577:cluster/SAP-dev-eksdemo to /root/.kube/config
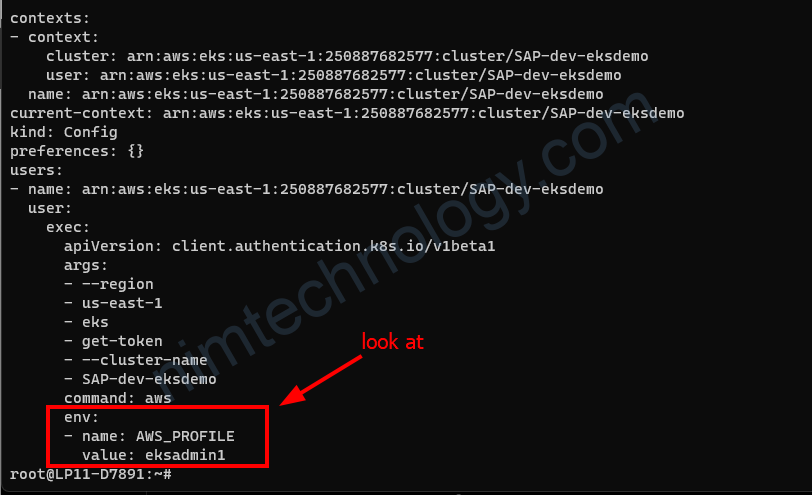
cat $HOME/.kube/configSẽ thấy có env kiểu như hình trên
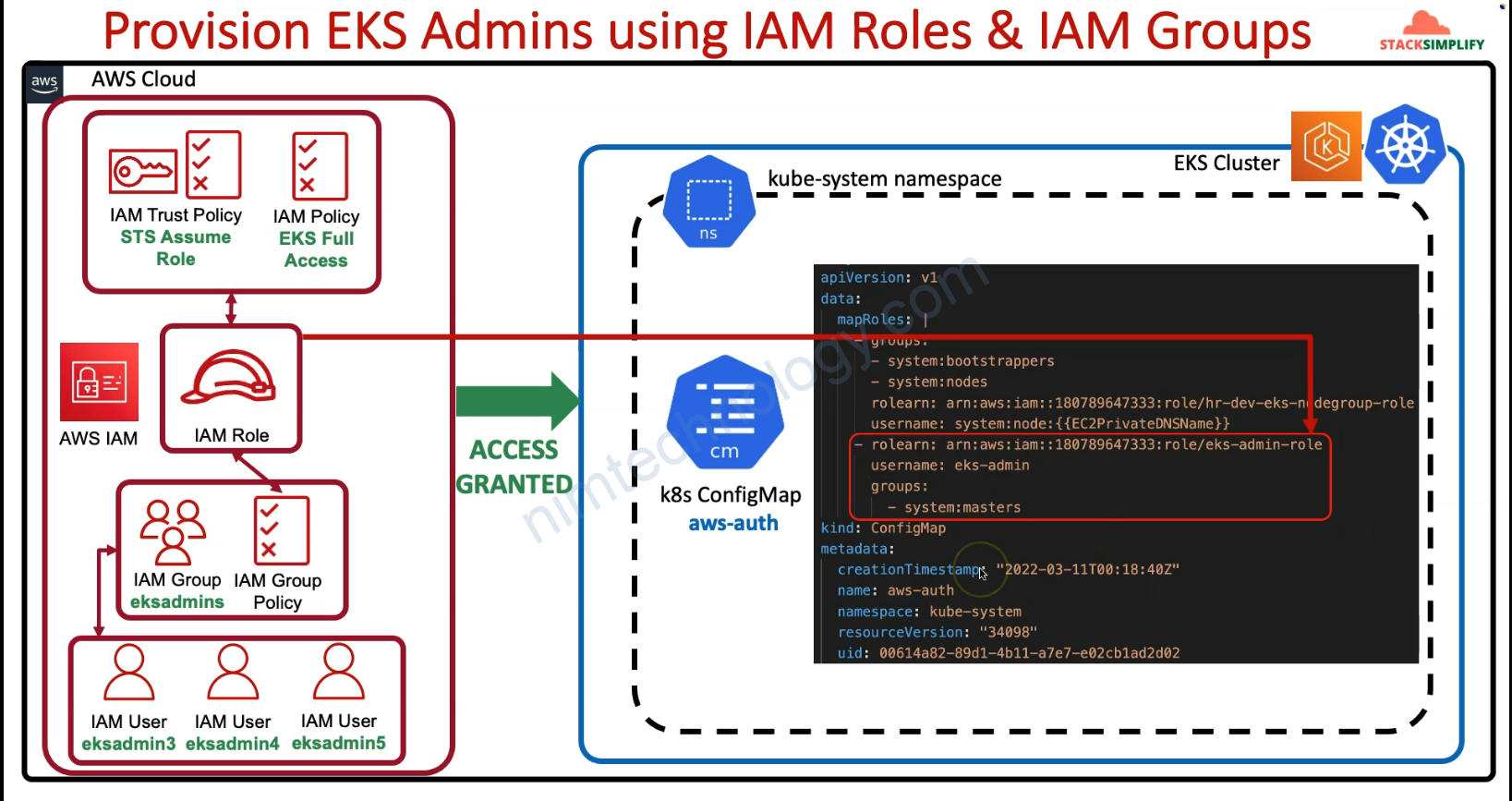
Nếu bạn chưa config strong config map thì sẽ lỗi như bên dưới.
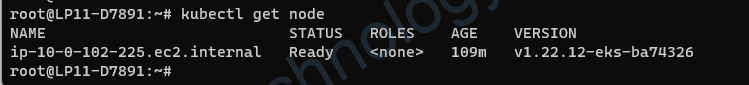
root@LP11-D7891:~# kubectl get node error: You must be logged in to the server (Unauthorized)
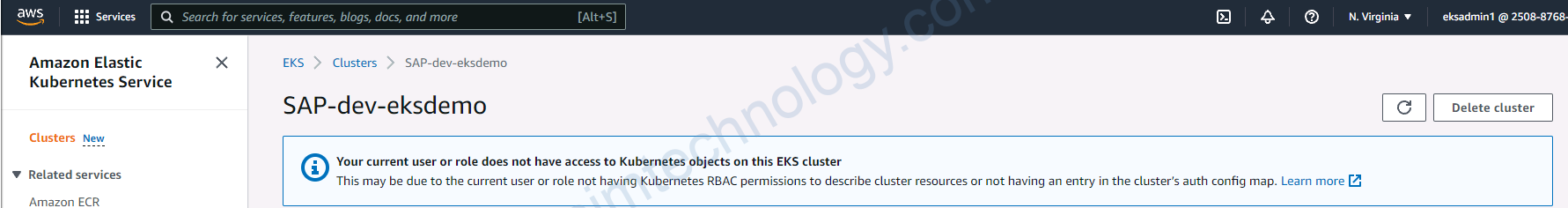
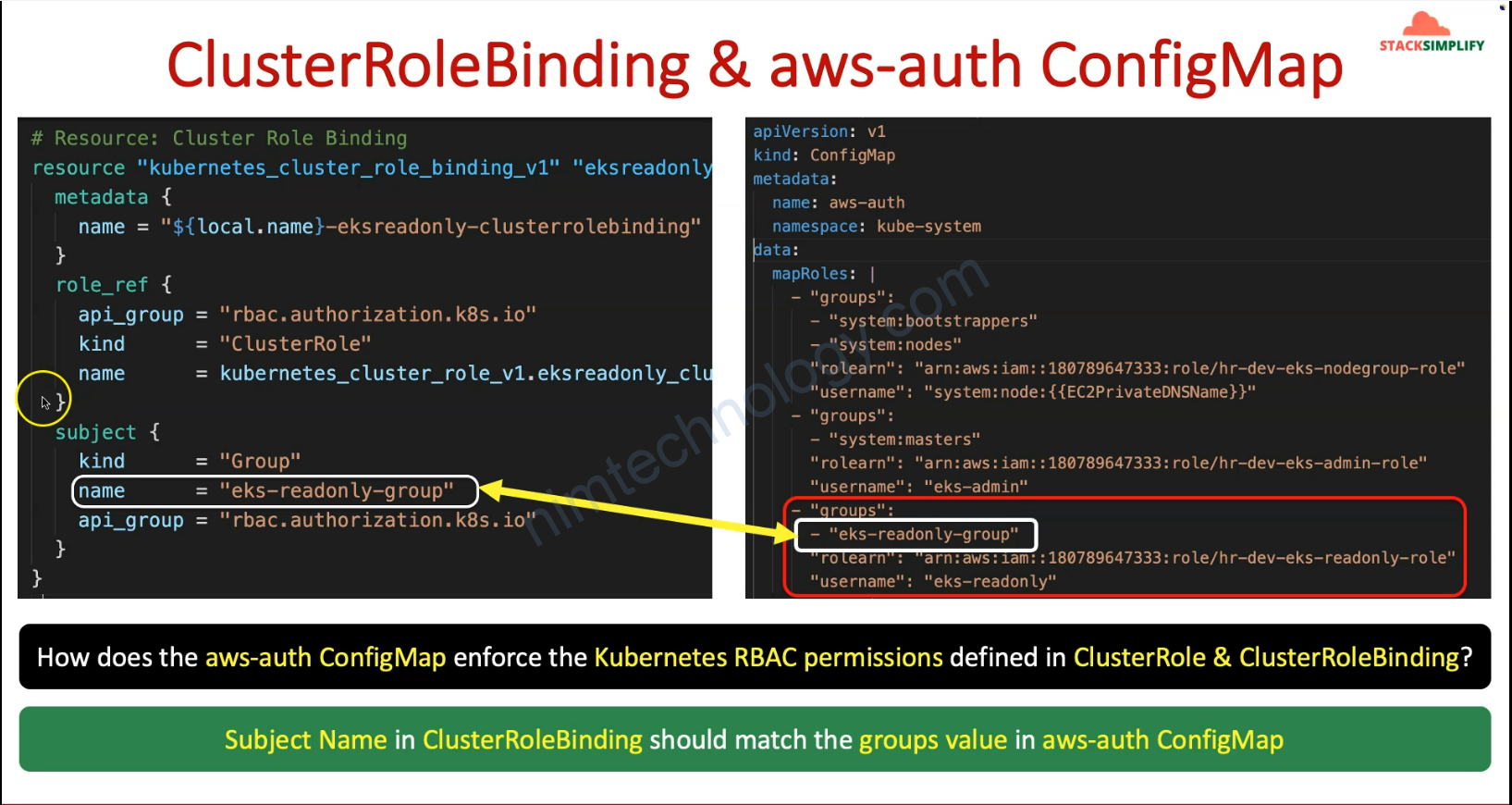
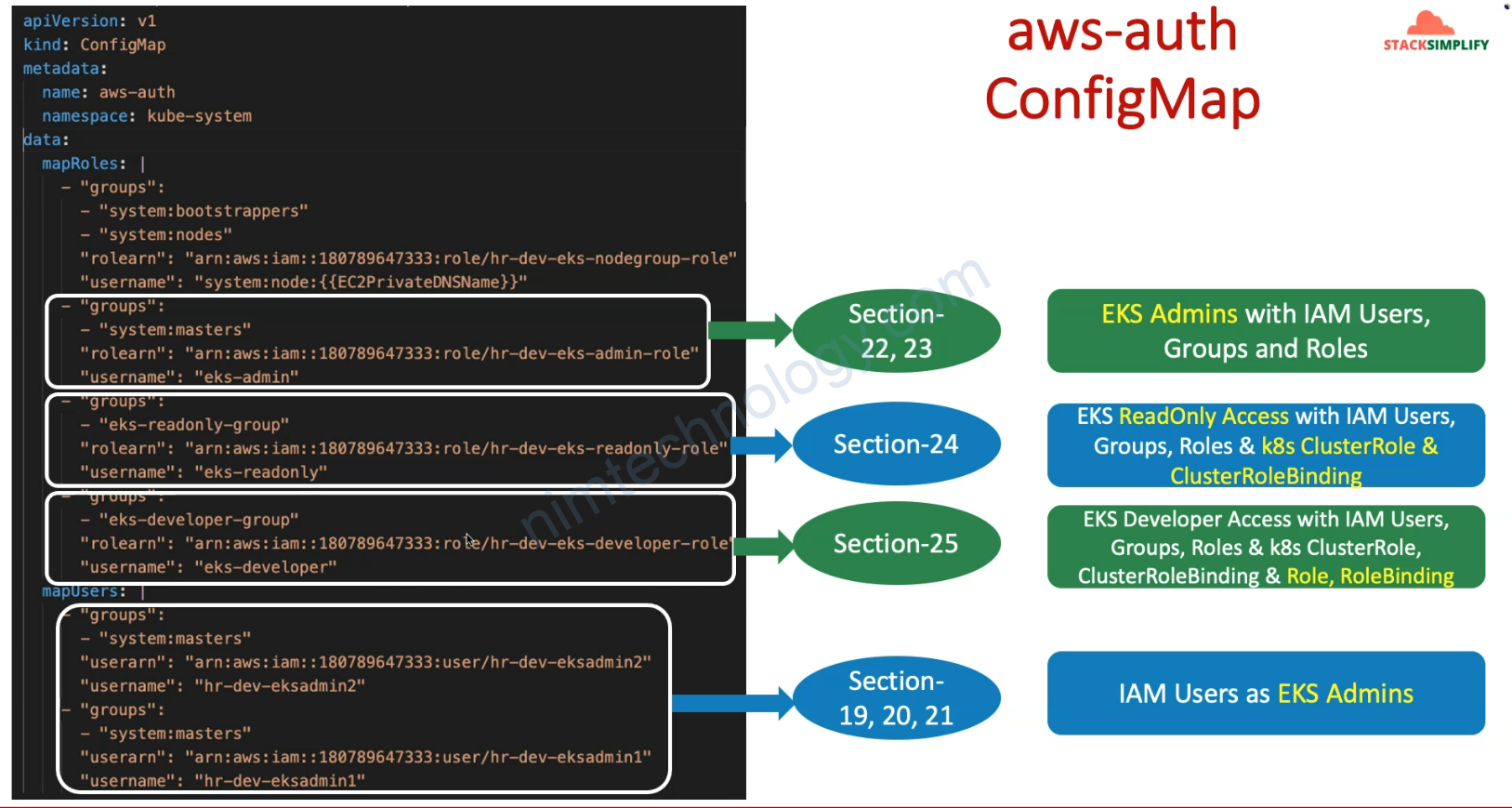
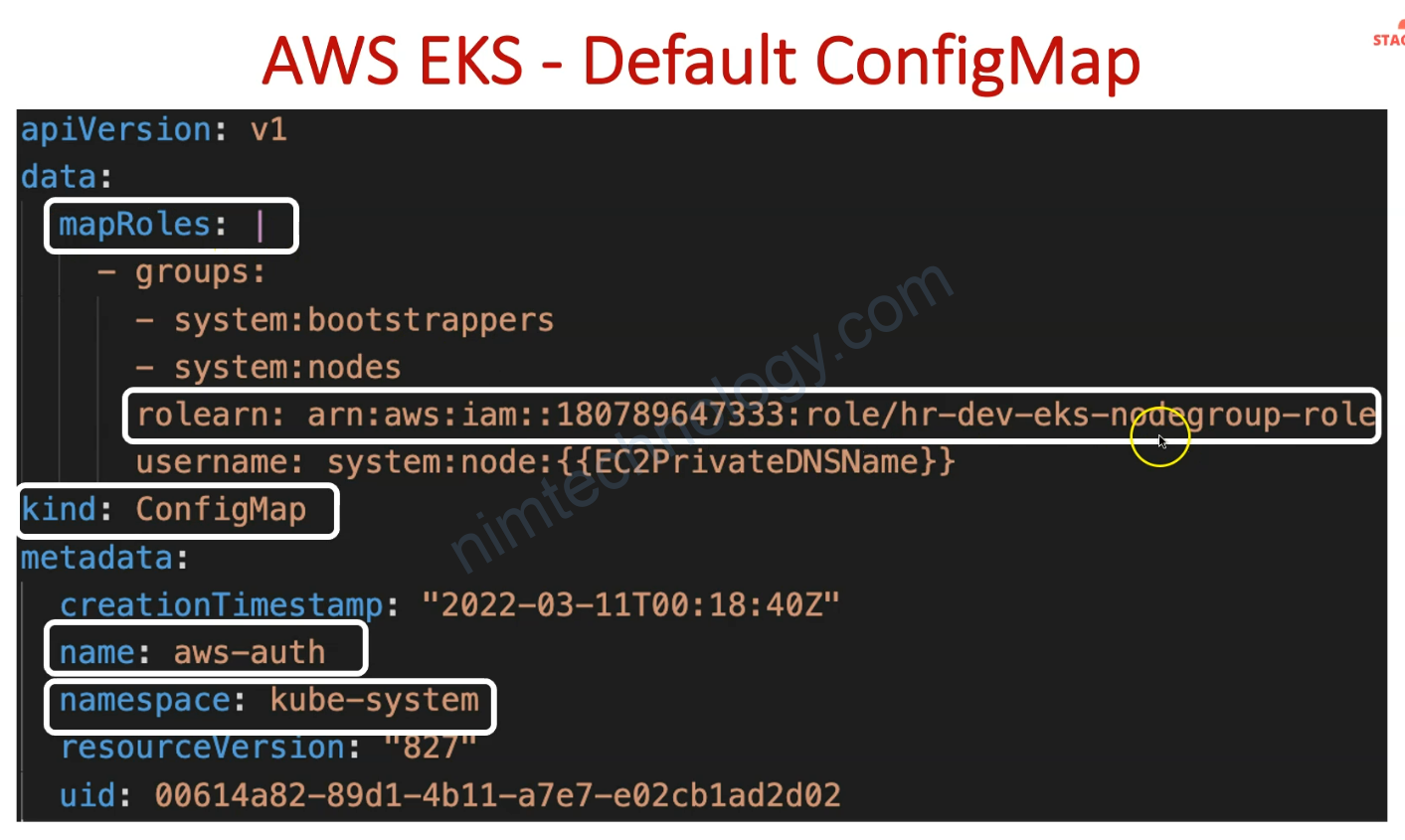
Giờ bạn cần thêm 1 config map trên EKS như anh dưới
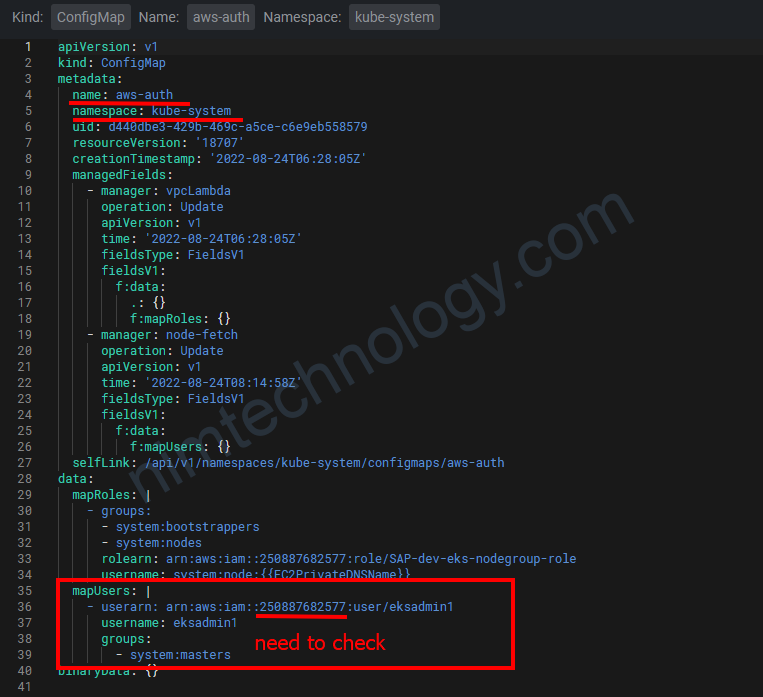
data:
mapRoles: |
- groups:
- system:bootstrappers
- system:nodes
rolearn: arn:aws:iam::250887682577:role/SAP-dev-eks-nodegroup-role
username: system:node:{{EC2PrivateDNSName}}
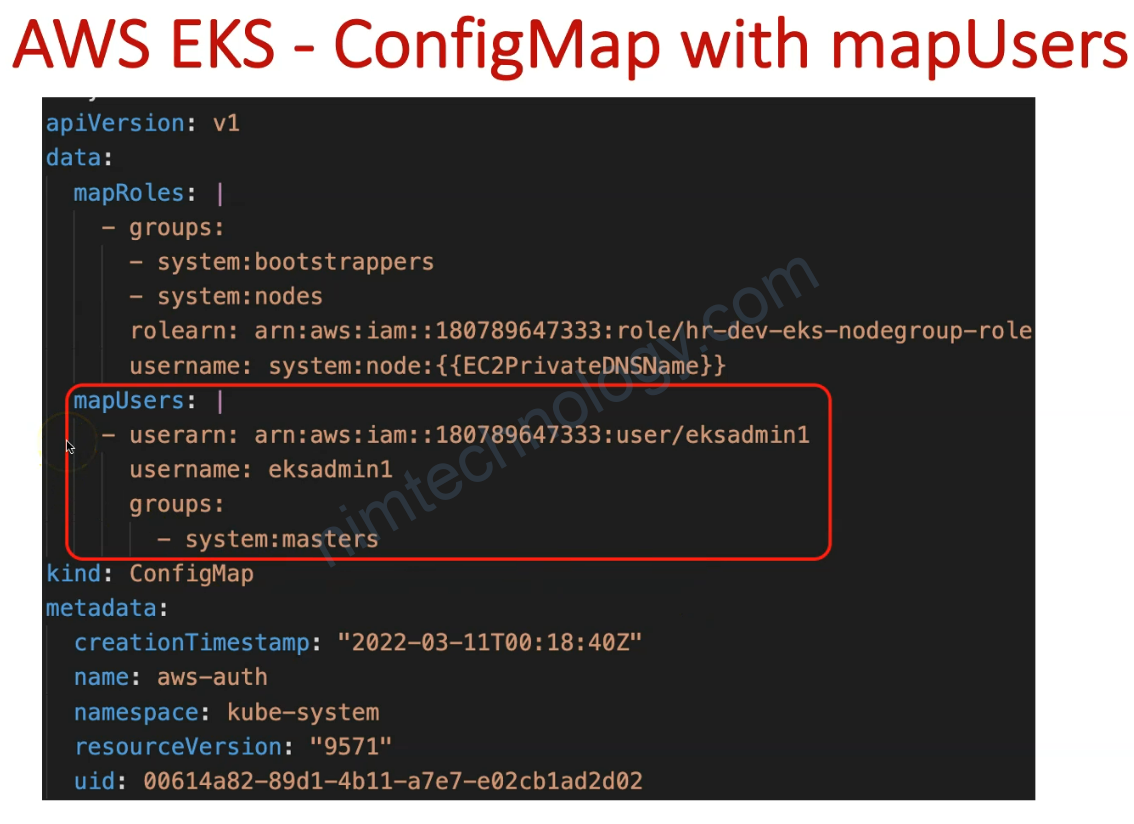
mapUsers: |
- userarn: arn:aws:iam::250887682577:user/eksadmin1
username: eksadmin1
groups:
- system:masters
binaryData: {}
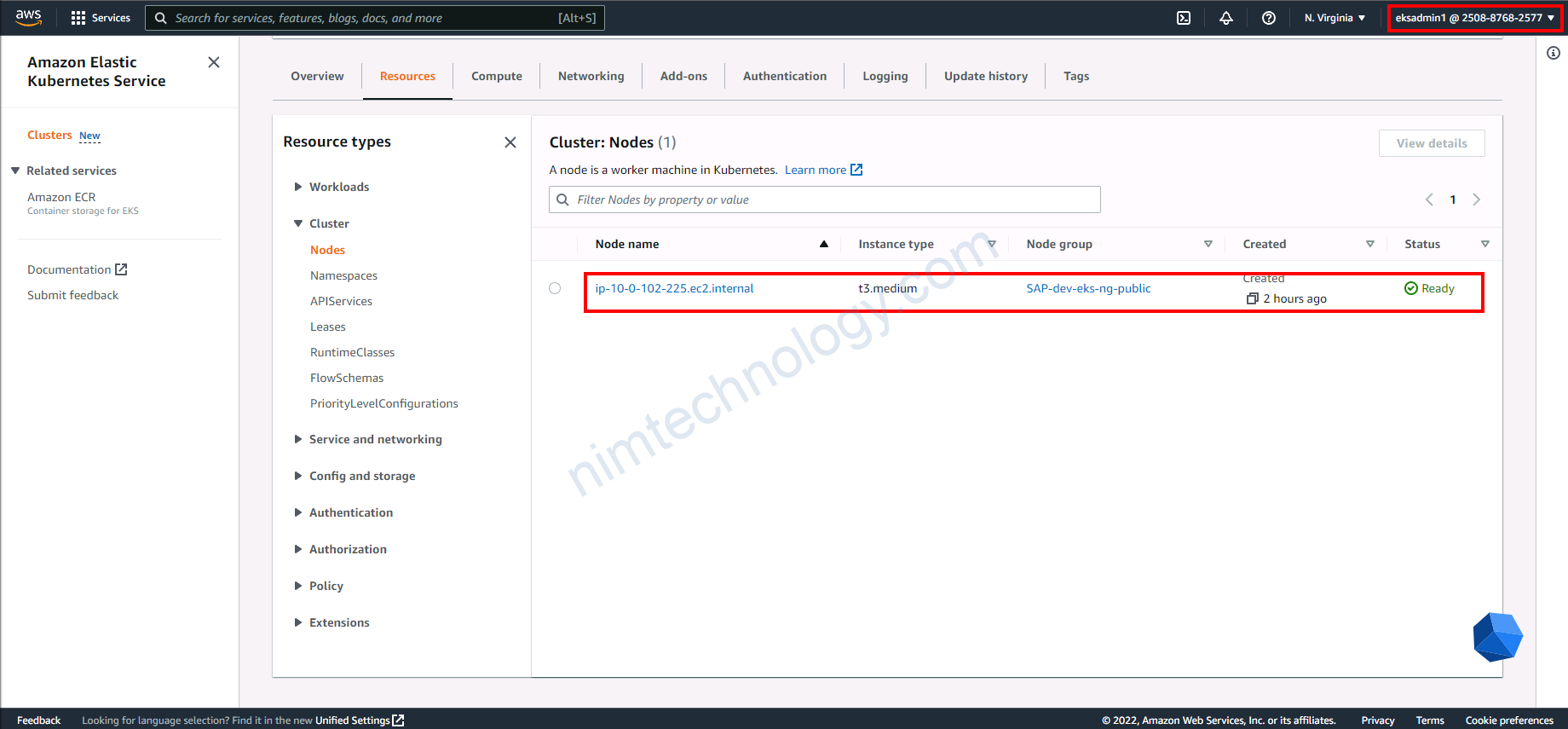
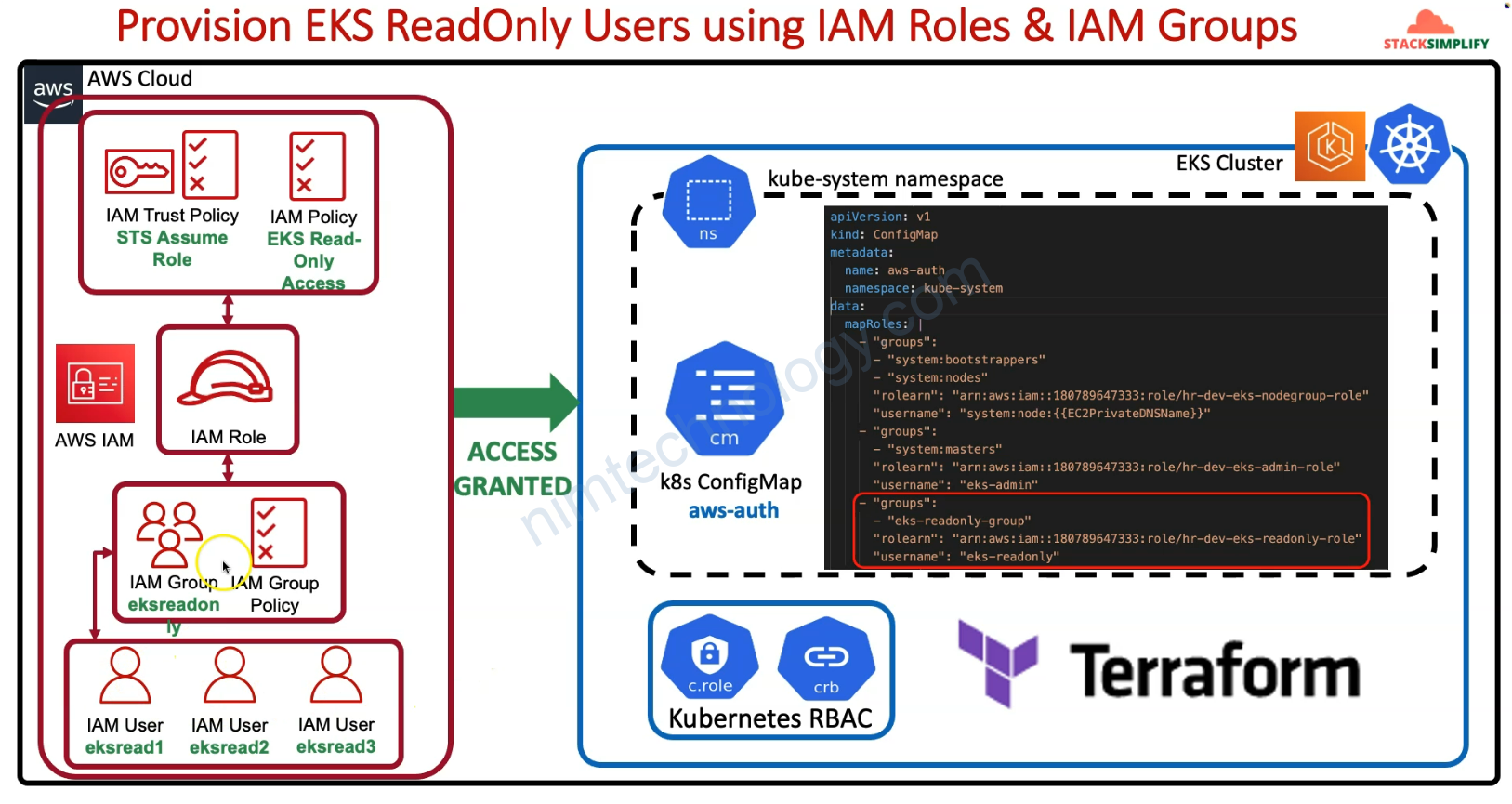
6) Help Federated users can access EKS
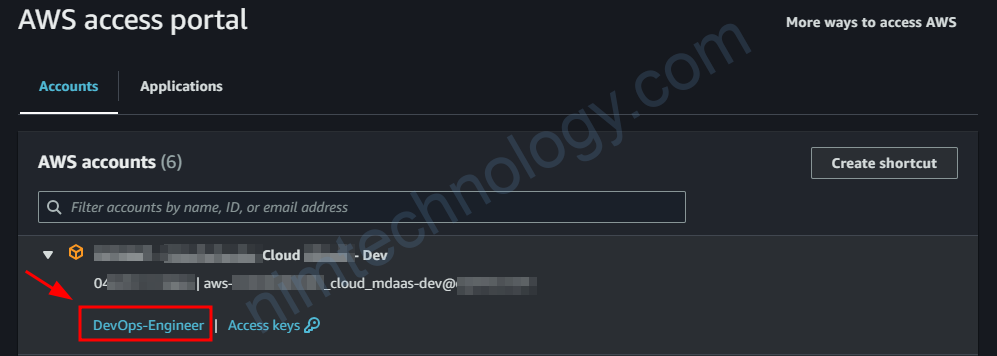
thường chúng ta sẽ được đăng nhập vào AWS console như sau:
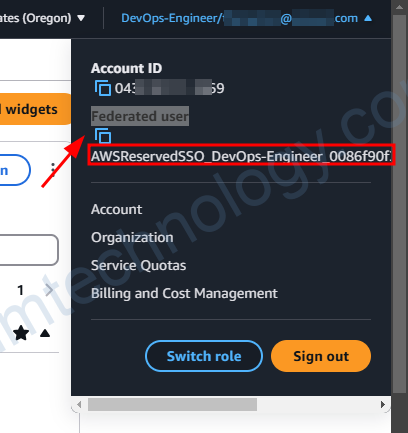
Bạn sẽ cần copy Federated users để sửa configmap: aws-auth trong kube-system namespace
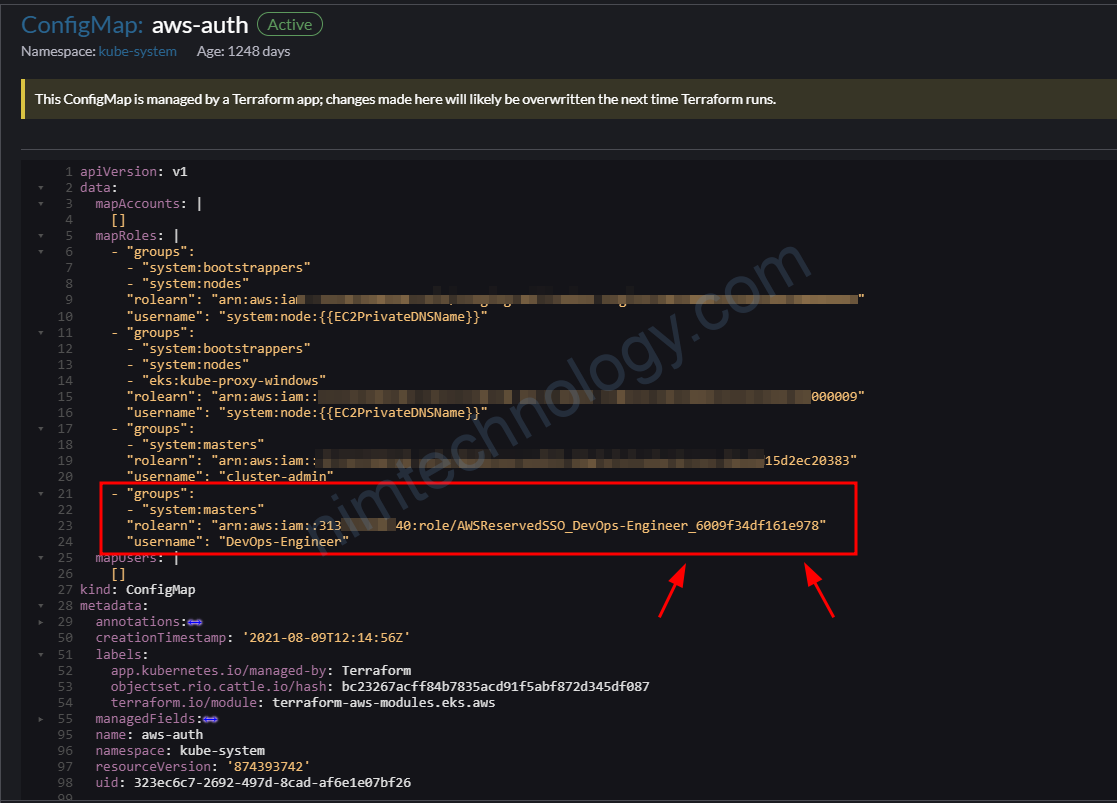
Bạn add thêm Federated users follow theo ảnh trên