1) Install Awgo WorkFlows.
helm repo add argo https://argoproj.github.io/argo-helm
>>>value.yaml
server:
extraArgs:
- --auth-mode=server
singleNamespace: true
controller:
containerRuntimeExecutor: emissary
workflowDefaults:
spec:
serviceAccountName: argo-workflows-server
workflow:
serviceAccount:
create: true
1.1) explain a few configuration.
useStaticCredentials: true
When useStaticCredentials is set to true, Argo Workflows uses the static AWS credentials provided to it (typically through a Kubernetes Secret), instead of attempting to use other methods of obtaining AWS credentials, such as IAM roles for service accounts (IRSA) or instance metadata.
The static credentials generally refer to the AWS Access Key ID and Secret Access Key. These should be stored securely, such as in a Kubernetes Secret, and provided to the Argo Workflows components that need them.
2) Simple template
2.1) container-template
apiVersion: argoproj.io/v1alpha1
kind: Workflow
metadata:
generateName: wf-container-template- # Name of this workflow
spec:
entrypoint: container-template # defines "whalesay" as the "main" template
templates:
- name: container-template #defining the "whalesay" template
container:
image: python:3.8-slim
command: [echo, "Nimtechnology"]
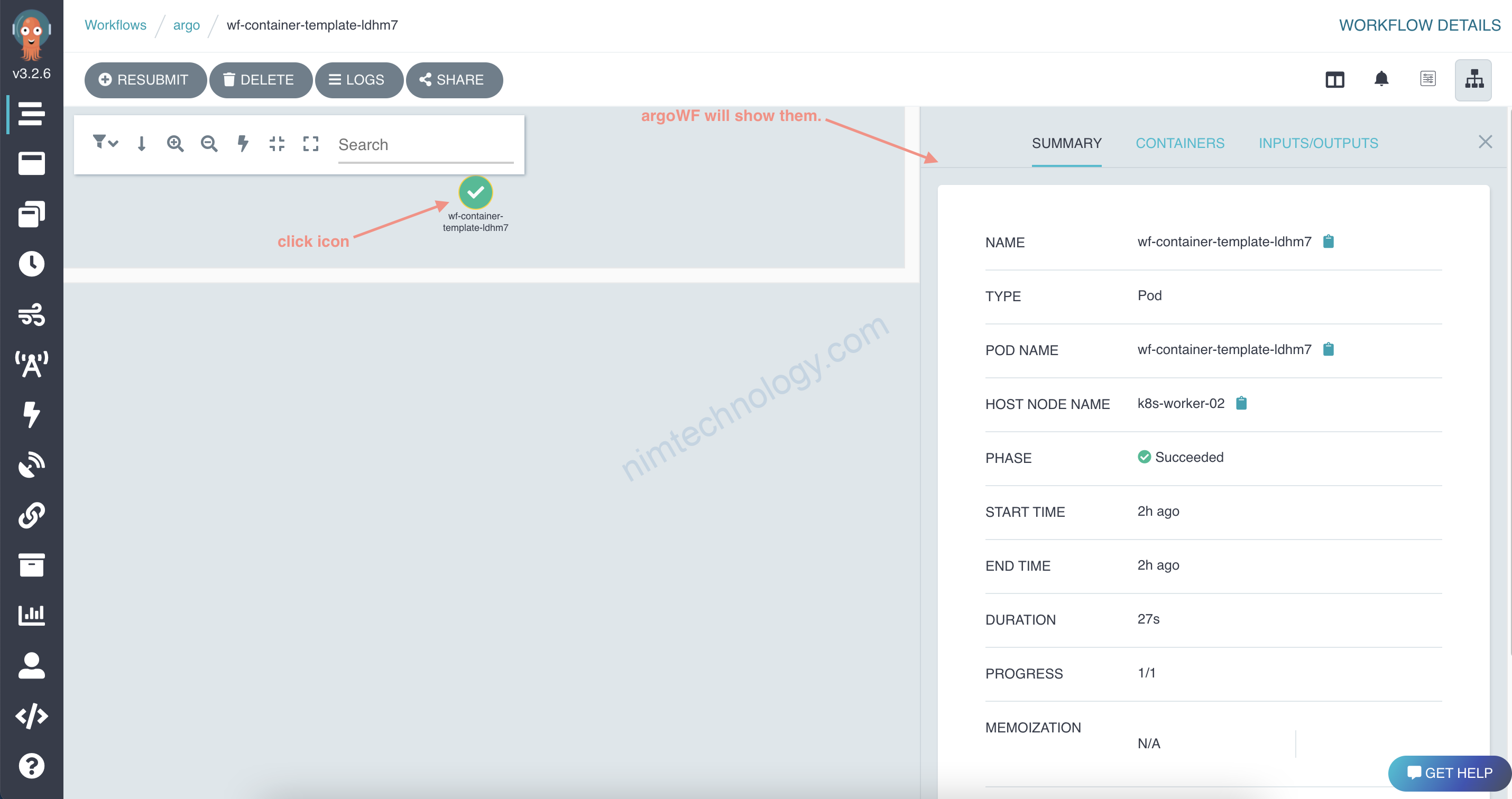
Để chạy được cái này bạn chọn create nhé.
Mình apply thì nó báo lỗi.
kubectl -n argo create -f hello-world.yamlhttps://argoproj.github.io/argo-workflows/workflow-executors/#kubelet-kubelet
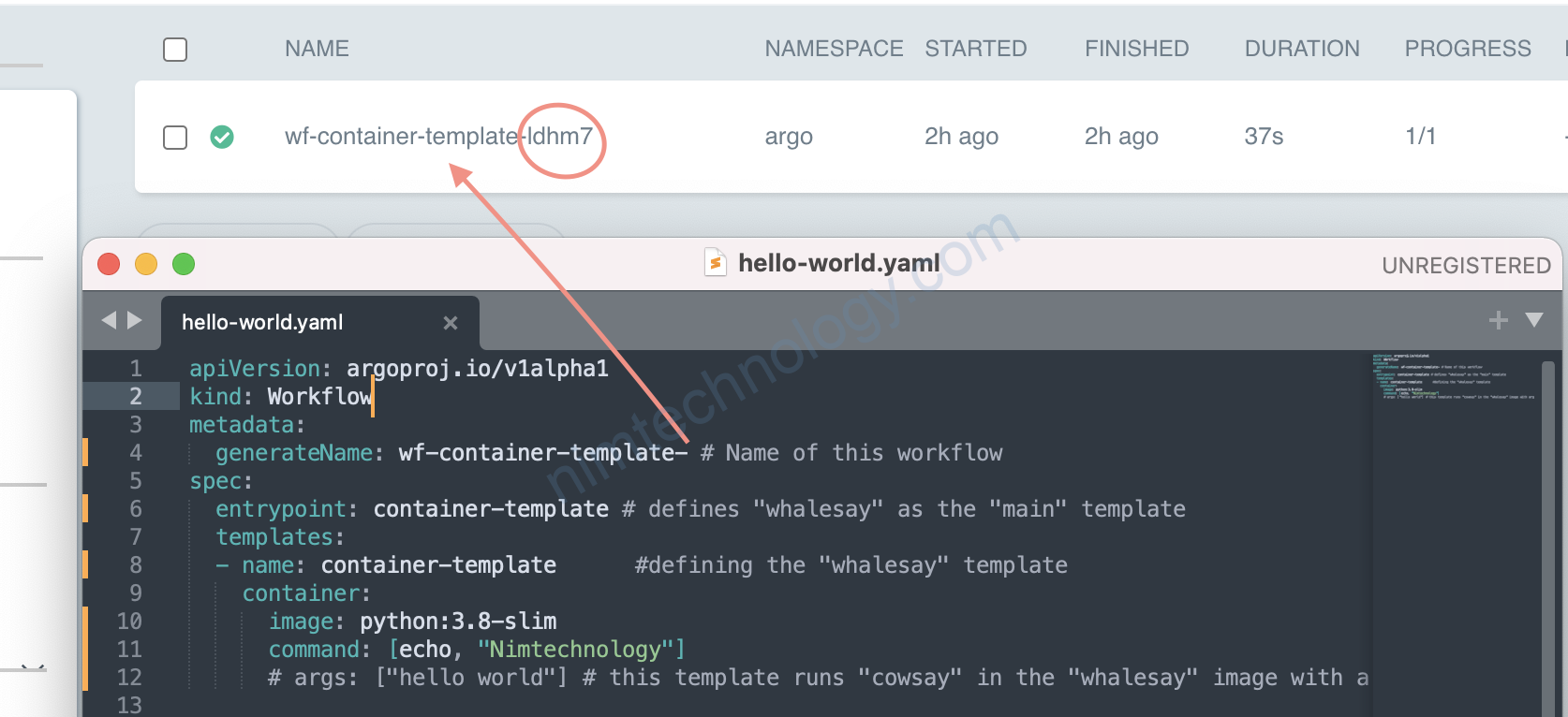
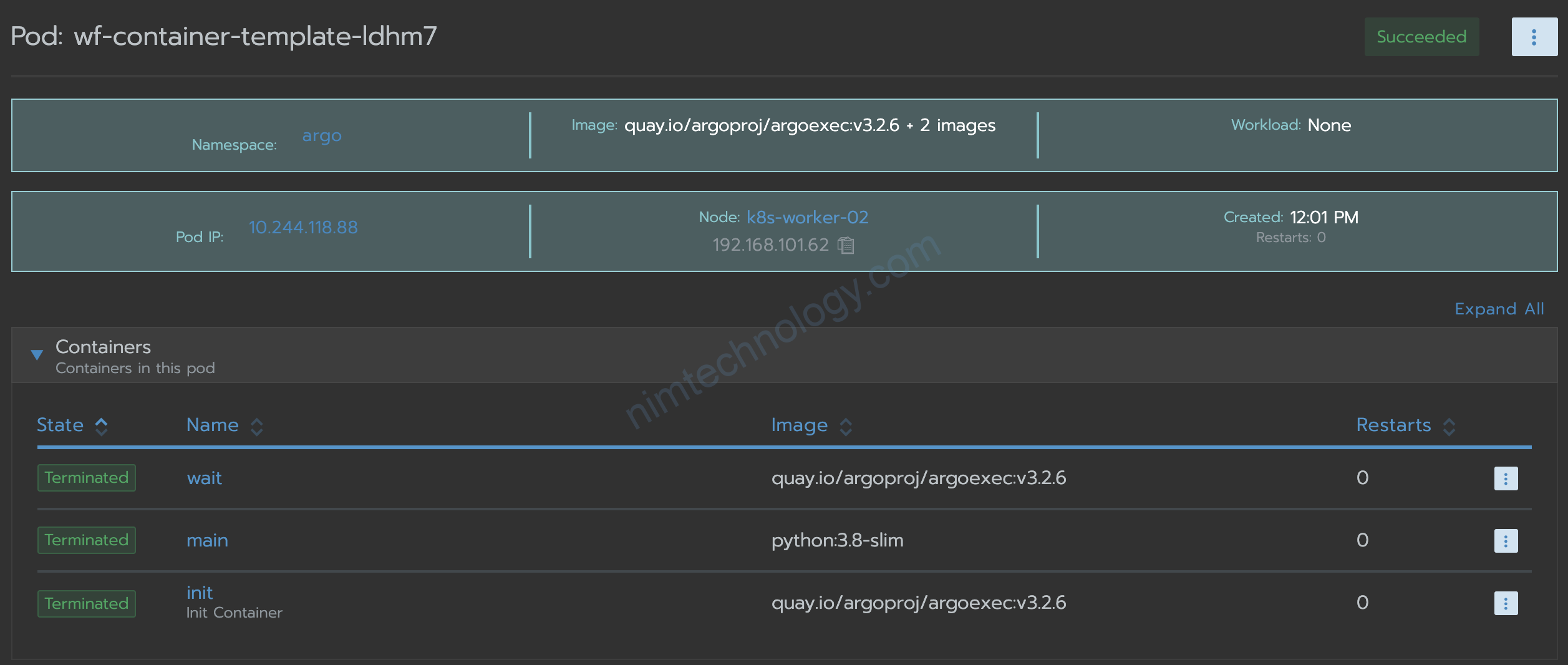
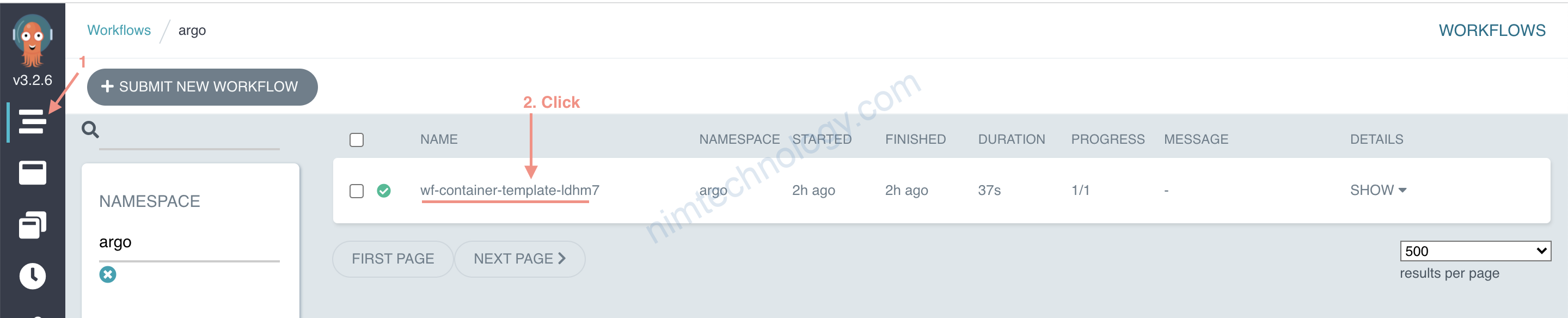
Argoworkflow sẽ thêm 5 kí tự vào đó, để đảm bảo nó là unique.(Duy nhất)
generateName sẽ hỉnh là tên pod luôn

Workflow Executors thì mình đang chạy mode: Emissary (emissary)
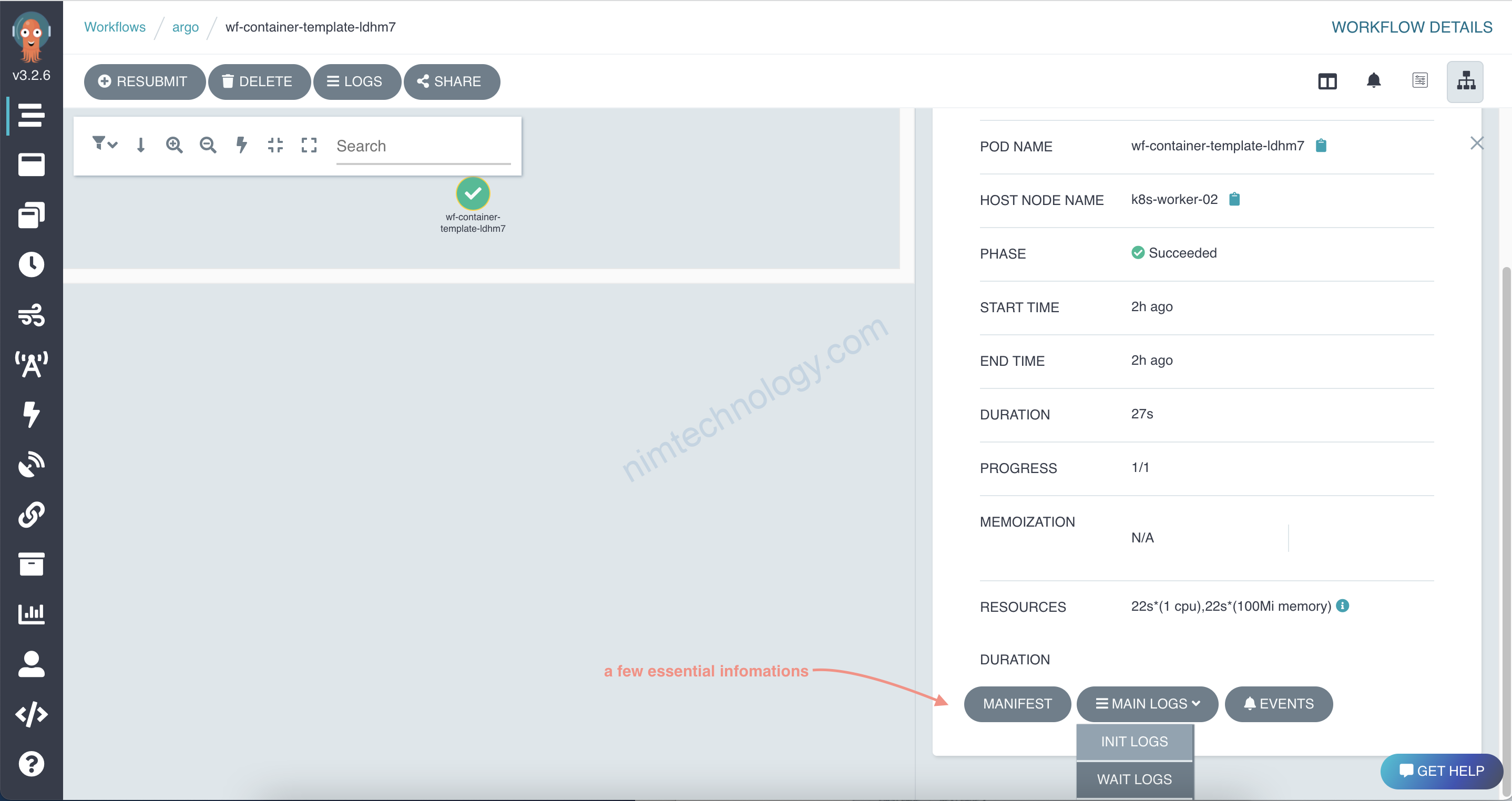
2.2) script-template
apiVersion: argoproj.io/v1alpha1
kind: Workflow
metadata:
generateName: wf-script-template- # Name of this workflow
spec:
entrypoint: script-template # defines "whalesay" as the "main" template
templates:
- name: script-template #defining the "whalesay" template
script:
image: python:3.8-slim
command: [python]
source: |
print("Nimtechnology - the script template was executed successfully.")
Anh/em tiếp tục: kubectl -n argo create
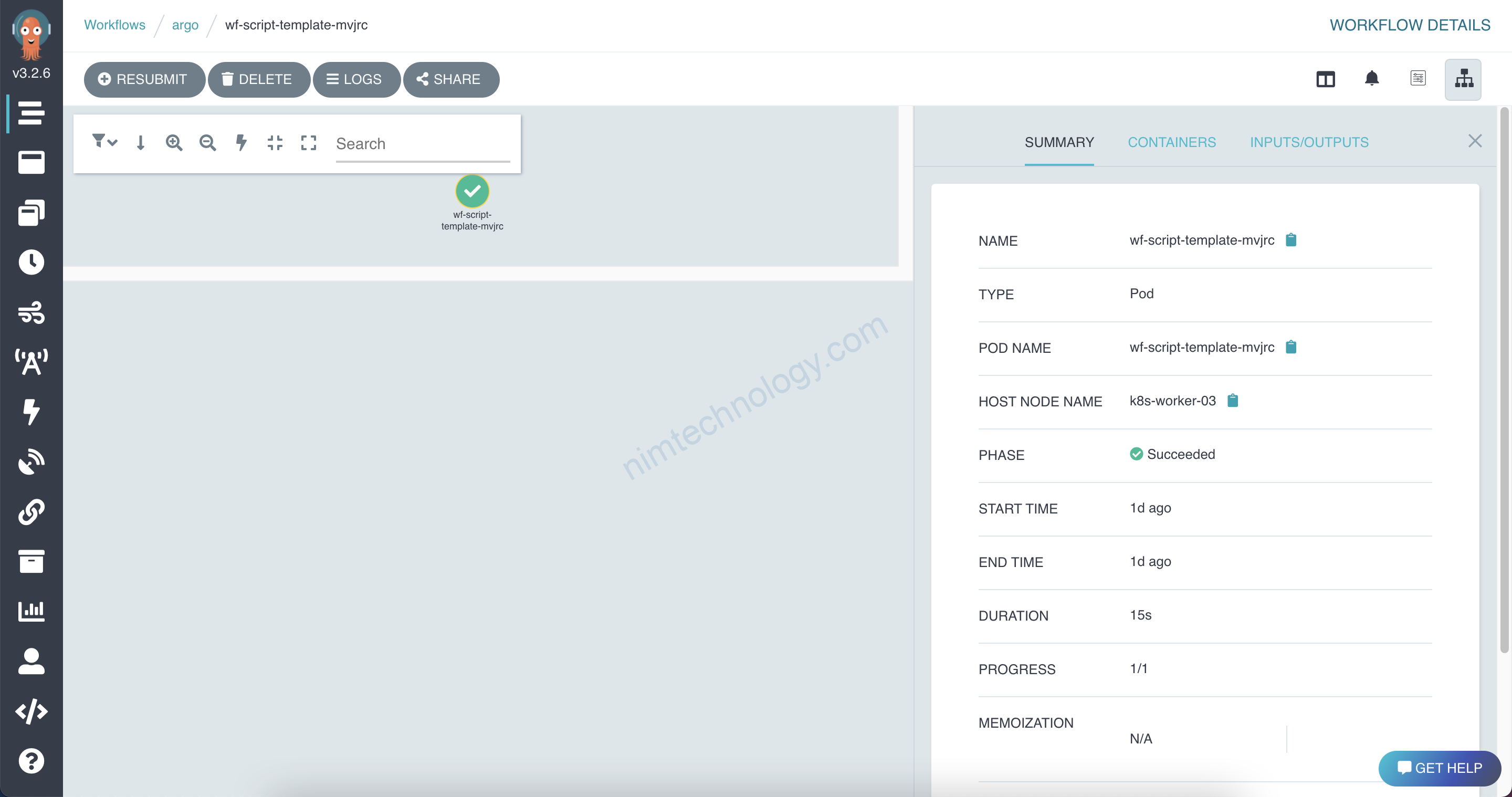
Ở nhưng Bài đầu này mình cũng gần như chưa thấy nhiều sự khách biệt giữa container-template và script-template.
Hiện tại mình chỉ thấy khách ở việc run command trong container.
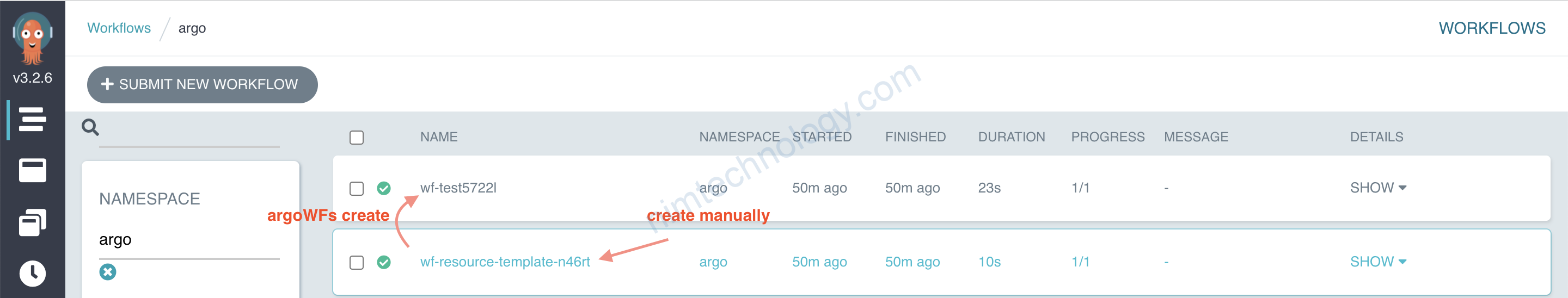
2.3) resource-template
apiVersion: argoproj.io/v1alpha1
kind: Workflow
metadata:
generateName: wf-resource-template- # Name of this workflow
spec:
entrypoint: resource-template # defines "whalesay" as the "main" template
templates:
- name: script-template #defining the "whalesay" template
resource:
action: create
manifest: |
apiVersion: argoproj.io/v1alpha1
kind: Workflow
metadata:
generateName: wf-test
spec:
entrypoint: test-template
templates:
- name: test-template
script:
image: python:3.8-slim
command: [python]
source: |
print("Nimtechnology - the script template was executed successfully.")
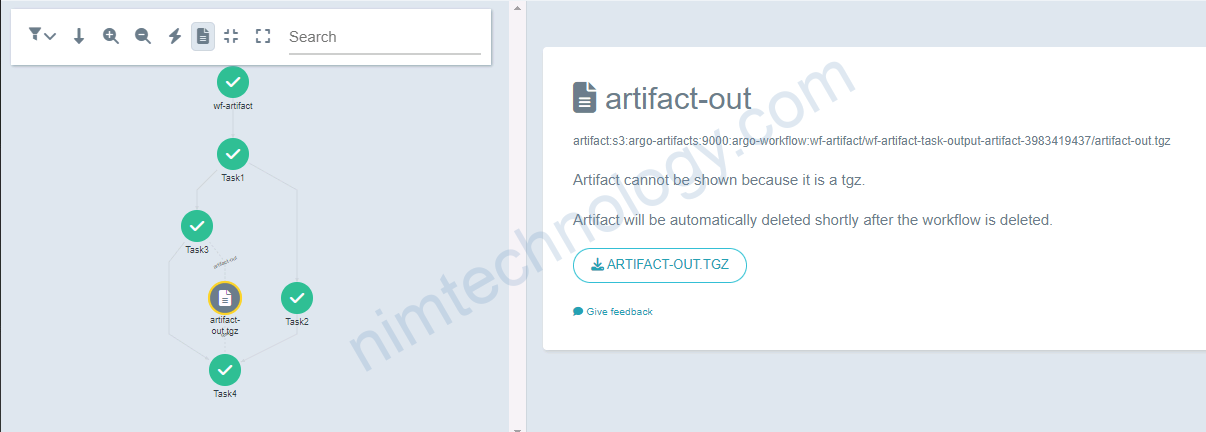
kubectl -n argo create -f wf-resource-template.yaml
>>>outout
workflow.argoproj.io/wf-resource-template-2t5n9 created
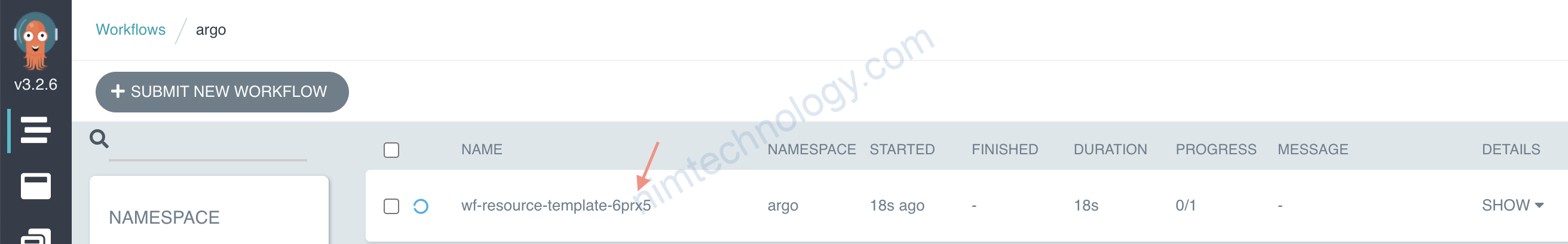
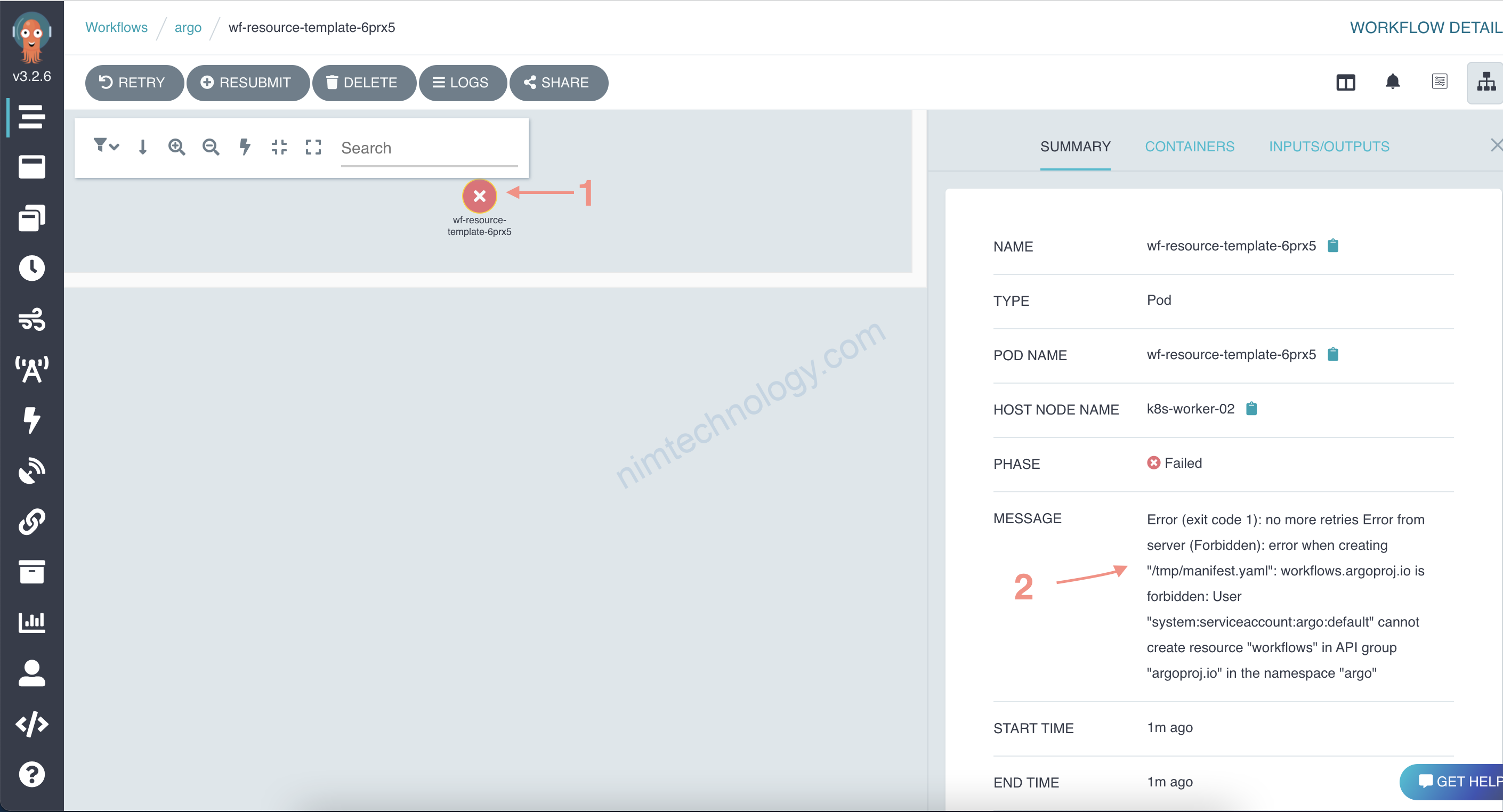
Đại loại thì lỗi trên là nó dùng 1 service acount là default mà SA default này lại ko có quyên tạo resource “workflows”
resolve this problem: https://github.com/argoproj/argo-workflows/issues/1021
Mình đoán là argo workflows sẽ có SA đáp đứng được điều kiện trên. Giờ đi tìm thôi.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: server
app.kubernetes.io/instance: argo-workflows
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: argo-workflows-server
app.kubernetes.io/part-of: argo-workflows
helm.sh/chart: argo-workflows-0.9.4
name: argo-workflows-server
namespace: argo
rules:
- apiGroups:
- ''
resources:
- configmaps
- events
verbs:
- get
- watch
- list
- apiGroups:
- ''
resources:
- pods
- pods/exec
- pods/log
verbs:
- get
- list
- watch
- delete
- apiGroups:
- ''
resources:
- secrets
verbs:
- get
- apiGroups:
- ''
resources:
- events
verbs:
- watch
- create
- patch
- apiGroups:
- argoproj.io
resources:
- eventsources
- sensors
- workflows
- workfloweventbindings
- workflowtemplates
- cronworkflows
verbs:
- create
- get
- list
- watch
- update
- patch
- delete
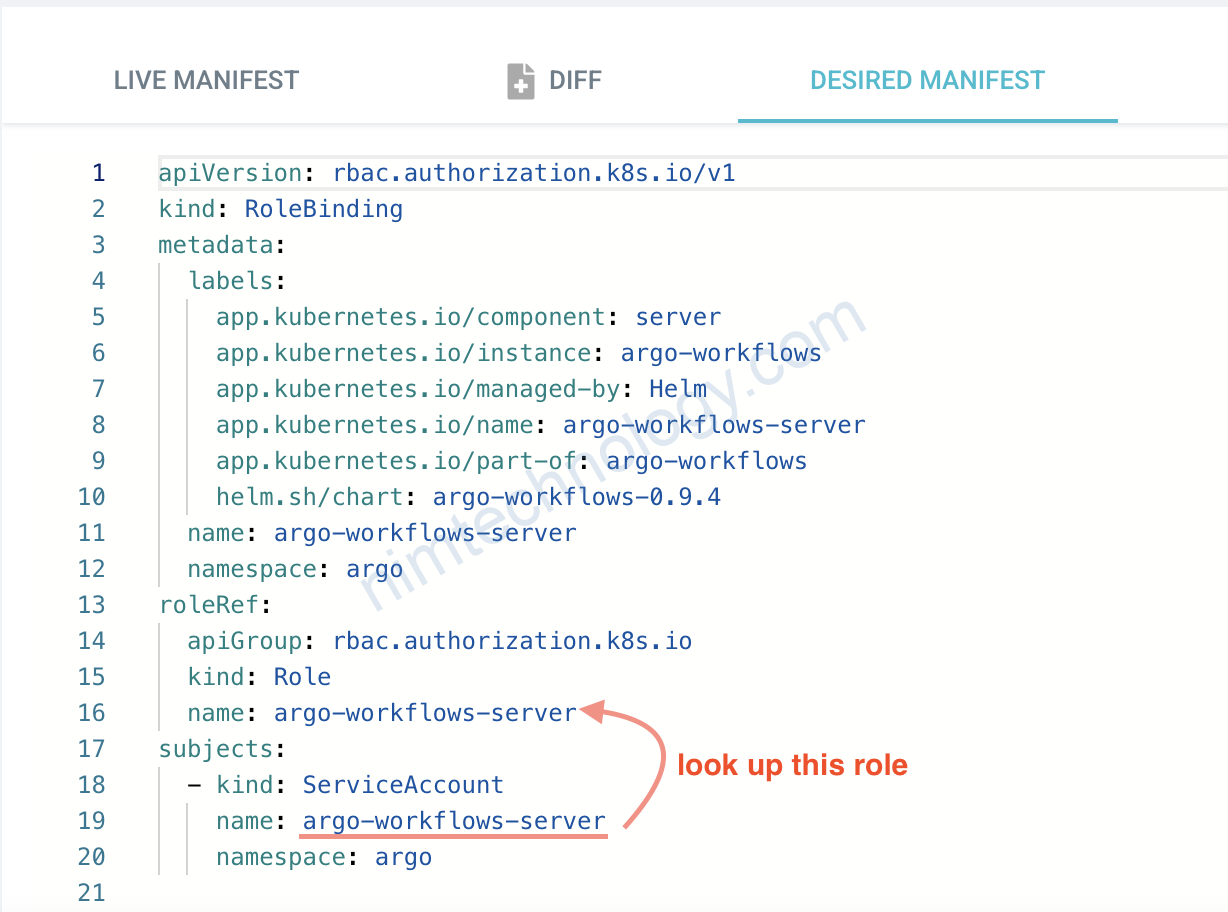
Anh em có thể thấy là role khá nhiều quyền. Lấy service account service argo-workflows-server sài thôi
file value của helm chart sẽ là:
server:
extraArgs:
- --auth-mode=server
singleNamespace: true
controller:
containerRuntimeExecutor: emissary
workflowDefaults:
spec:
serviceAccountName: argo-workflows-server
workflow:
serviceAccount:
create: true
Giờ create lại yaml resource: