Remove Inbound Rule in the Security Group
Lỗi sau là mình gặp sau khi upgrade module eks từ 1.18 -> 1,19
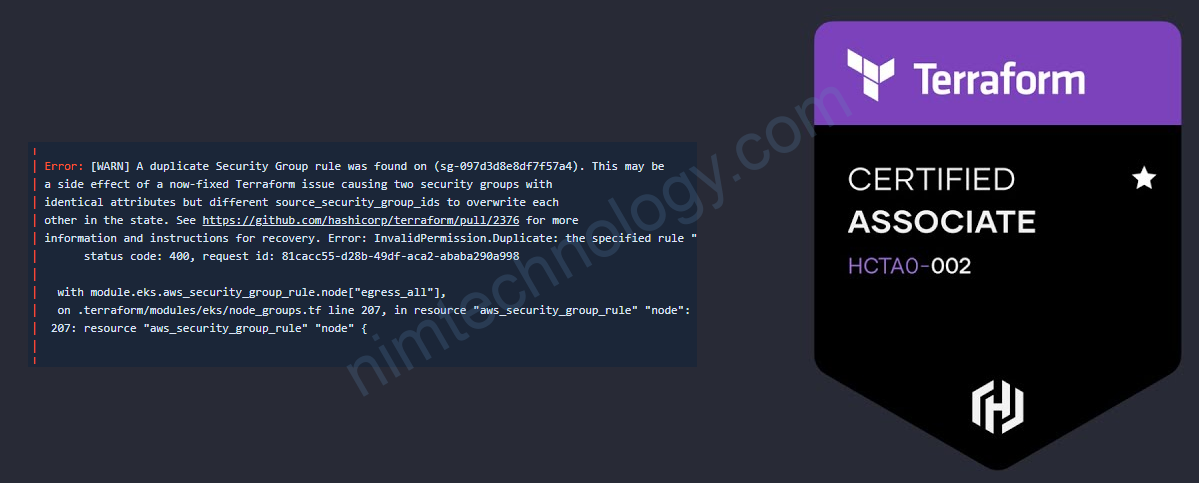
╷
│ Error: [WARN] A duplicate Security Group rule was found on (sg-097d3d8e8df7f57a4). This may be
│ a side effect of a now-fixed Terraform issue causing two security groups with
│ identical attributes but different source_security_group_ids to overwrite each
│ other in the state. See https://github.com/hashicorp/terraform/pull/2376 for more
│ information and instructions for recovery. Error: InvalidPermission.Duplicate: the specified rule "peer: sg-0057a36d87dd949a5, TCP, from port: 4443, to port: 4443, ALLOW" already exists
│ status code: 400, request id: 7c0a36cb-a591-4b33-9666-b8c6f1091a7b
│
│ with module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"],
│ on .terraform/modules/eks/node_groups.tf line 207, in resource "aws_security_group_rule" "node":
│ 207: resource "aws_security_group_rule" "node" {
│
╵
Ở bản 1.19 đã được thêm như là mặc định
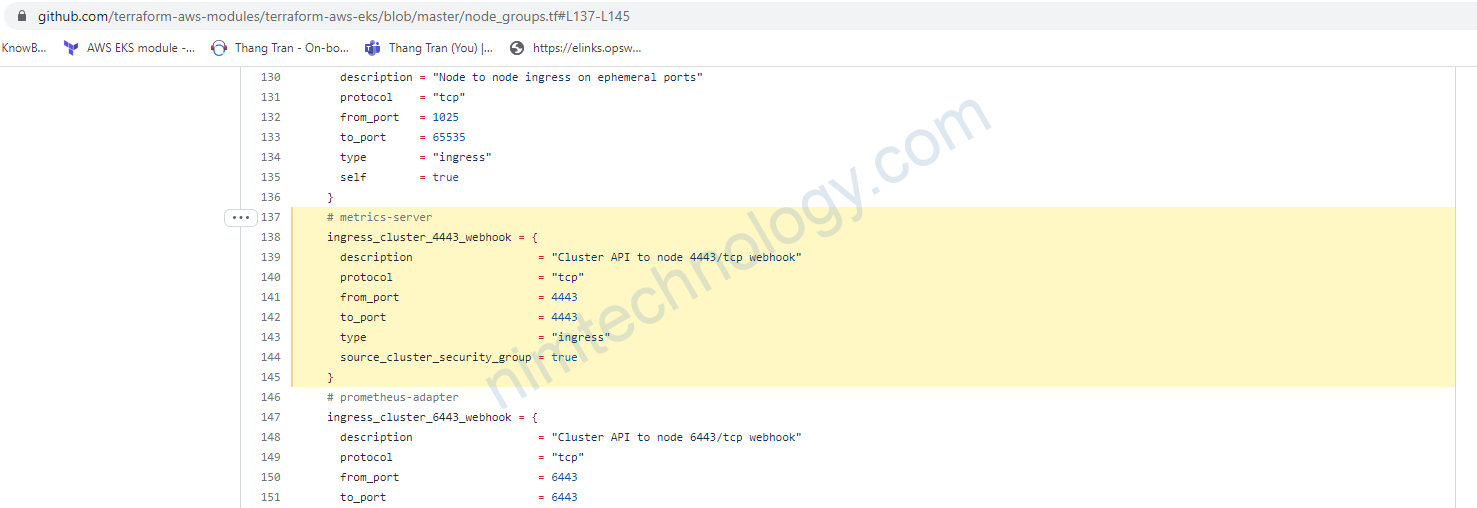
https://github.com/terraform-aws-modules/terraform-aws-eks/blob/master/node_groups.tf#L137-L145
Giờ mình cần xóa rule inbound này.
https://bobbyhadz.com/blog/aws-cli-remove-security-group-rule
aws ec2 describe-security-groups --profile <profile_name>Bạn chịu khó list tất cả ra, xong dựa vào format bên dưới
Điểm đặc biệt đây là rule link với –source-group
aws ec2 revoke-security-group-ingress --group-id sg-097d3d8e8df7f57a4 --protocol tcp --port 4443 --source-group sg-0057a36d87dd949a5 --profile <profile_name>Remove Outbound Rule in the Security Group
╷
│ Error: [WARN] A duplicate Security Group rule was found on (sg-097d3d8e8df7f57a4). This may be
│ a side effect of a now-fixed Terraform issue causing two security groups with
│ identical attributes but different source_security_group_ids to overwrite each
│ other in the state. See https://github.com/hashicorp/terraform/pull/2376 for more
│ information and instructions for recovery. Error: InvalidPermission.Duplicate: the specified rule "peer: 0.0.0.0/0, ALL, ALLOW" already exists
│ status code: 400, request id: 81cacc55-d28b-49df-aca2-ababa290a998
│
│ with module.eks.aws_security_group_rule.node["egress_all"],
│ on .terraform/modules/eks/node_groups.tf line 207, in resource "aws_security_group_rule" "node":
│ 207: resource "aws_security_group_rule" "node" {
│
╵
Releasing state lock. This may take a few moments...
aws ec2 describe-security-groups --profile <profile_name>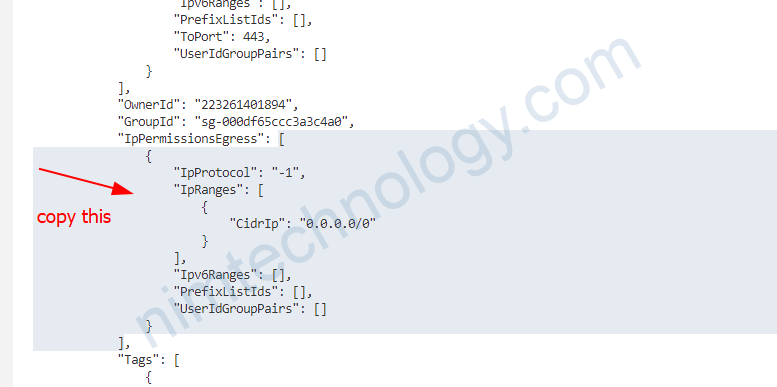
xong bạn muốn ép chúng thành 1 dòng thì paste it to address bar of Browser
aws ec2 revoke-security-group-egress \
--profile <profile_name> \
--group-id sg-097d3d8e8df7f57a4 \
--ip-permissions '[ { "IpProtocol": "-1", "IpRanges": [ { "CidrIp": "0.0.0.0/0", "Description": "Node all egress" } ], "Ipv6Ranges": [ { "CidrIpv6": "::/0", "Description": "Node all egress" } ], "PrefixListIds": [], "UserIdGroupPairs": [] } ]'