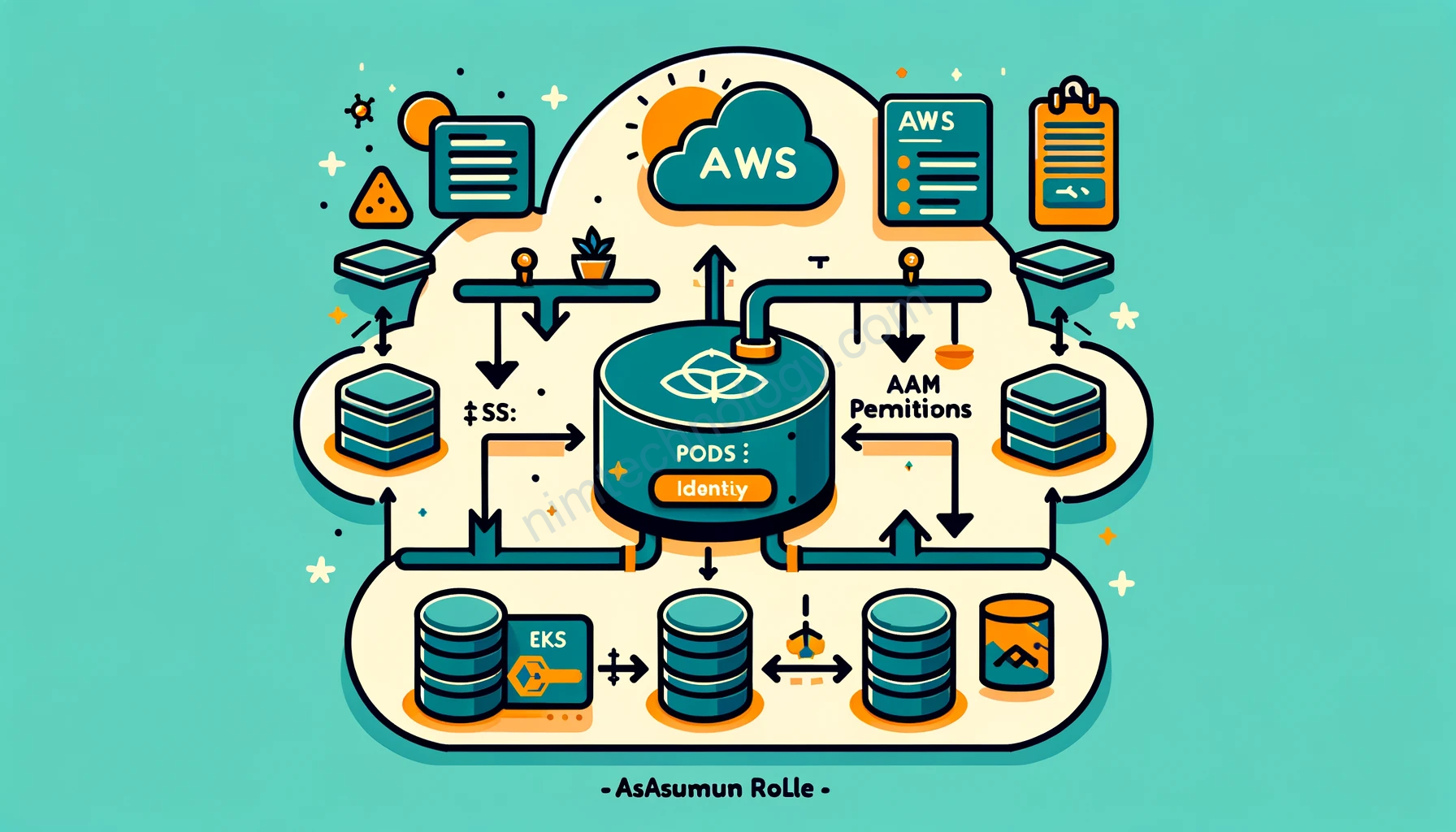
Amazon EKS Pod Identity is a new feature introduced by Amazon EKS that simplifies the process for cluster administrators to configure Kubernetes applications to obtain AWS IAM permissions. This enhancement allows permissions to be configured more easily and with fewer steps, directly through the EKS console, APIs, and CLI. Links
This feature is particularly important because applications must sign their AWS API requests with AWS credentials. EKS Pod Identities offer a streamlined method to manage these credentials for your applications. This approach is similar to how Amazon EC2 instance profiles provide credentials to Amazon EC2 instances. Links
EKS Pod Identity is designed to complement the existing IRSA (IAM Roles for Service Accounts) method, providing an alternative and secure way to grant AWS permissions to pods. It uses sts:AssumeRole and sts:TagSession for assuming the IAM role and passing temporary credentials to the pods. Additionally, the feature includes session tags in the requests to AWS STS (Security Token Service), which can be used in the condition keys in the trust policy. This allows administrators to restrict which service accounts, namespaces, and clusters can utilize a specific role.
https://securitylabs.datadoghq.com/articles/eks-pod-identity-deep-dive/
https://docs.aws.amazon.com/eks/latest/userguide/pod-id-role.html
In summary, Amazon EKS Pod Identity represents a significant advancement in the way Kubernetes applications on AWS interact with IAM, simplifying the process while maintaining the necessary security protocols for credential management.
Demo
(coming soon)