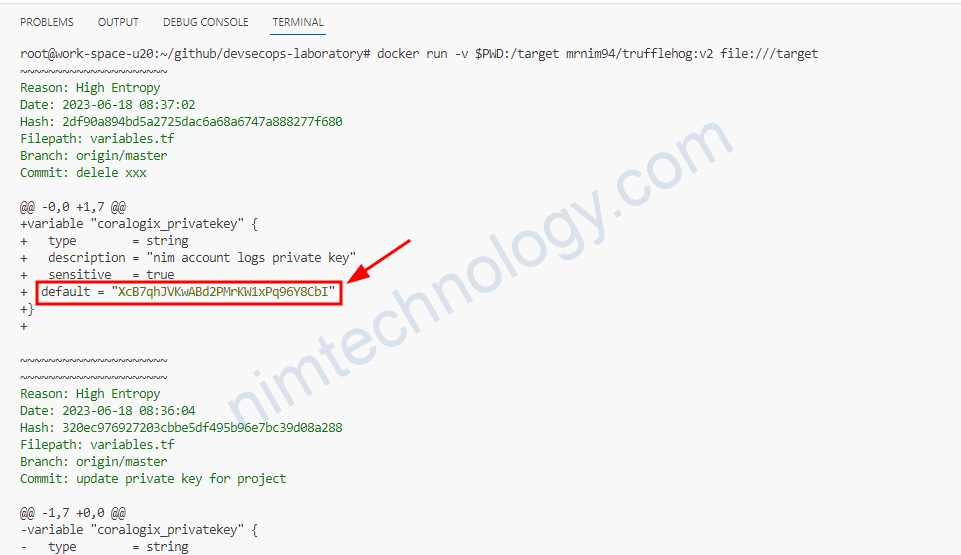
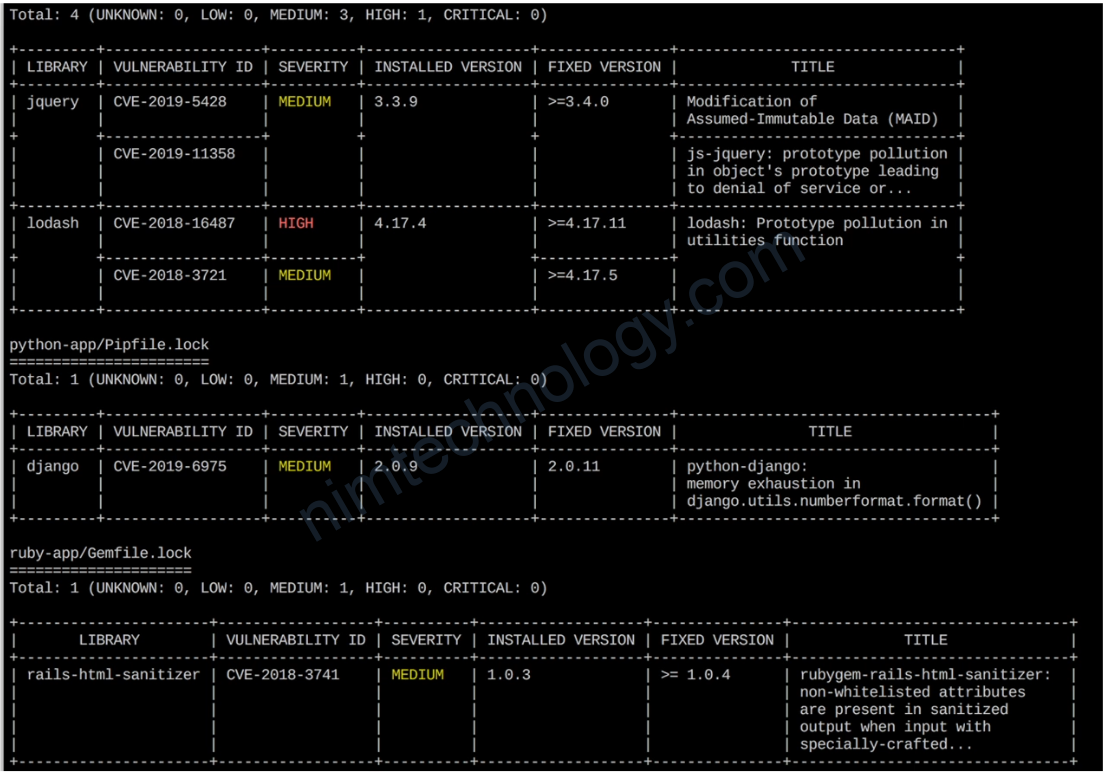
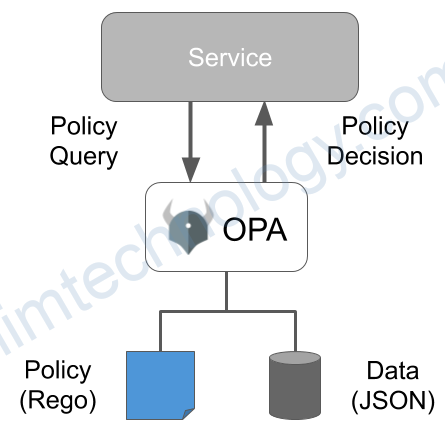
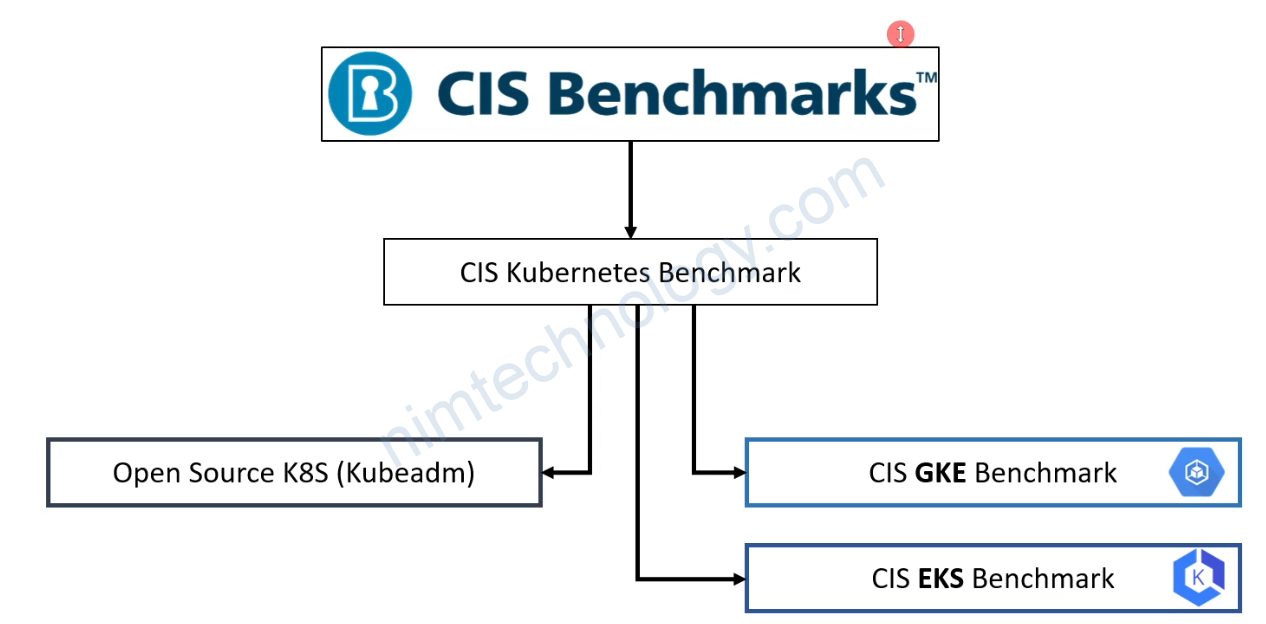
To find vulnerabilities on your EC2 Linux instance, including ones related to OpenSSH and other software, you can use several open-source tools. Here are some recommended steps and tools:
- Update and Patch Your System:
Ensure your system and all installed packages are up-to-date. This can often resolve many known vulnerabilities.
sudo apt-get update && sudo apt-get upgrade # or for RHEL-based systems sudo yum update
- Use OpenVAS:
OpenVAS (Open Vulnerability Assessment Scanner) is a comprehensive open-source vulnerability scanner and manager.
- Installation:
sudo apt-get install openvas sudo gvm-setup sudo gvm-start
- Usage: Access the web interface (typically https://:9392) and follow the instructions to scan your instance.
- Use Lynis:
Lynis is a security auditing tool for Unix-based systems.
- Installation:
sudo apt-get install lynis - Usage:
sudo lynis audit system
- Use ClamAV:
ClamAV is an open-source antivirus engine for detecting trojans, viruses, malware, and other malicious threats.
- Installation:
sudo apt-get install clamav - Usage:
sudo freshclam sudo clamscan -r /home
- Use Nmap and Nmap Scripts (NSE):
Nmap can be used to scan open ports and detect vulnerabilities.
https://www.stationx.net/how-to-scan-vulnerabilities-with-nmap/
- Installation:
sudo apt-get install nmap - Usage:
sudo nmap -sV --script=vuln <your-ec2-ip>
- Use Chkrootkit:
Chkrootkit is a tool to locally check for signs of a rootkit.
- Installation:
sudo apt-get install chkrootkit - Usage:
sudo chkrootkit
- Use Rkhunter:
Rootkit Hunter is a scanner for rootkits, backdoors, and possible local exploits.
- Installation:
sudo apt-get install rkhunter - Usage:
sudo rkhunter --check
- Install and Configure Fail2Ban:
Fail2Ban scans log files and bans IPs that show malicious signs.
- Installation:
sudo apt-get install fail2ban - Configuration: Edit the configuration files in
/etc/fail2ban/to suit your needs. - Usage:
sudo systemctl start fail2ban sudo systemctl enable fail2ban
These tools will help you identify and mitigate vulnerabilities on your EC2 Linux instance. Be sure to regularly update these tools and your system to keep up with the latest security patches and vulnerability definitions.