1) Symmetric Encryption

How it works:
- Stream cipher – encrypt one byte at the time
- Block cipher – encrypt entire units or blocks using predetermined key length such as 128, 192, or 256 bits.
Sender and receiver use same key to encrypt and decrypt
Example:
AES(Advance Encrypt Standard) – block cipher of 128, 192, 256 bits, most well-known and effective use. Take billions of years to crack, more secure than DES, Triple DES, IDEA.
DES(Data Encrypt Standard)
Triple DES
IDEA (International Data Encryption Algorithm)
TLS/SSL Protocol: session key
Pros:
– Encrypt & Decrypt large amount data quickly
– Easy to implement
– Speed: because of shorter key length.
– Industry adoption & Acceptance: AES is gold standard
Cons:
– Use single key to encrypt and decrypt
2) Asymmetric Encryption
• Use public key and secret key to encrypt and decrypt
sensitive information
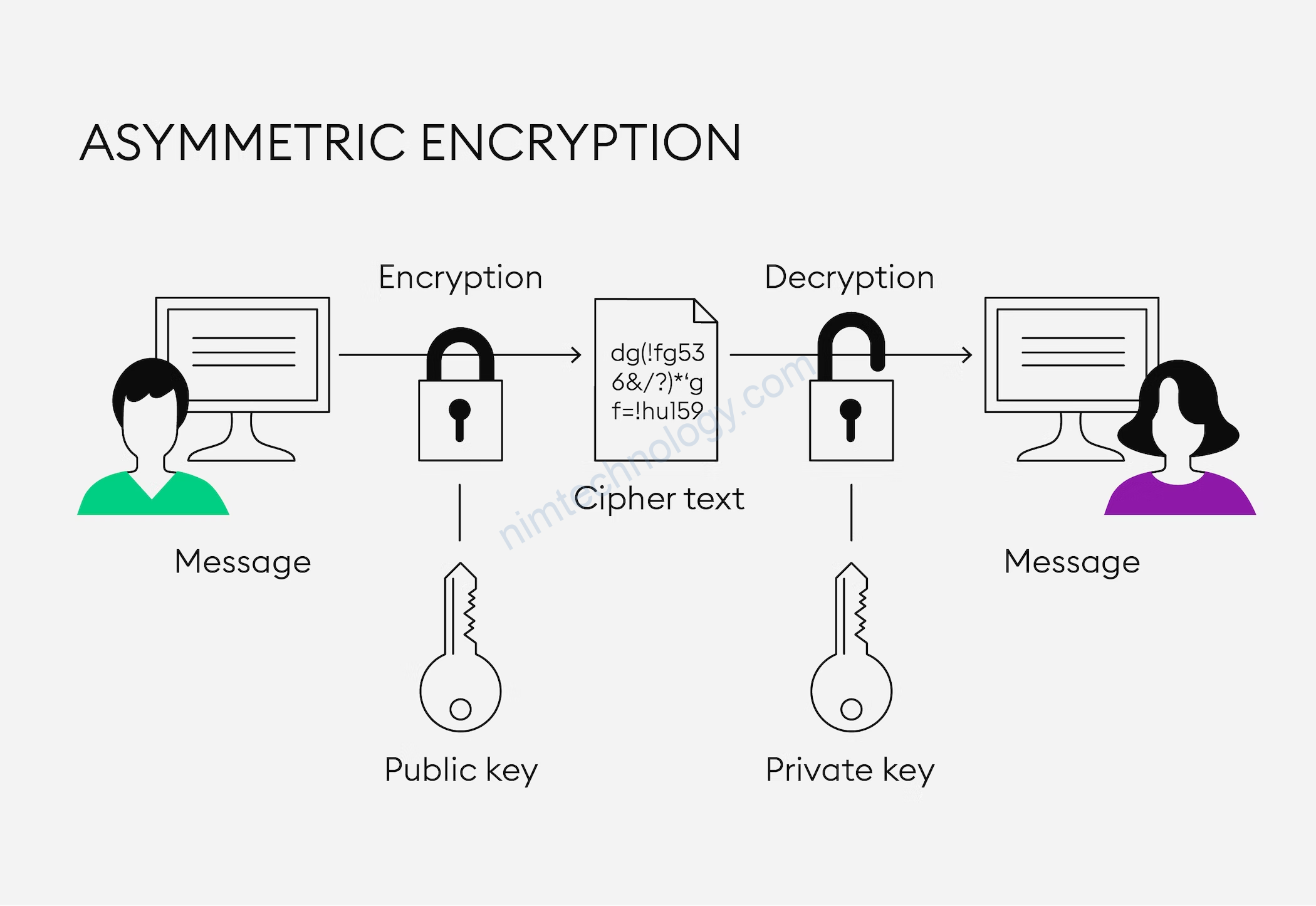
• RSA (Rivest Shamir Adlerman)
• DSA (Digital Signature Algorithm)
• ECC (Elliptical Curve Cryptography)
• Diffie-Hellman exchange method
• TLS/SSL protocol: TLS handshake
Pros:
• Key distribution not necessary
• Exchange of private key not necessary
• Digital signature / message authentication
Cons:
• Speed: longer key length
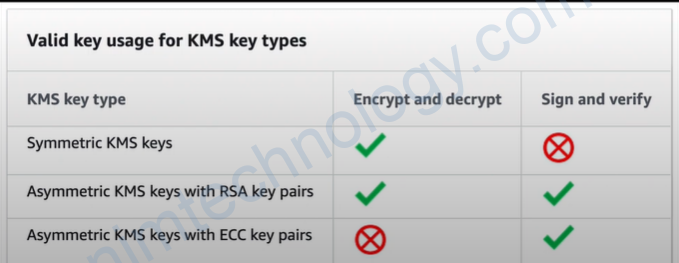
3) AWS KMS
AWS KMS Supports:
Symmetric KMS key: 256-bit secret encryption, AES algorithm in Galois Counter Mode (AES-GCM) is used
Asymmetric KMS key
4) Demo AWS KMS
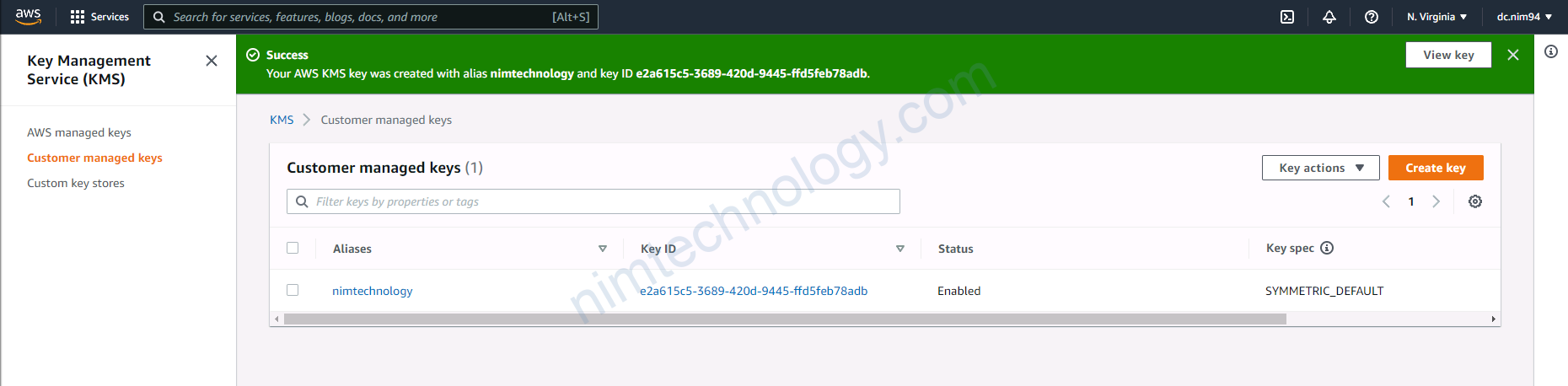
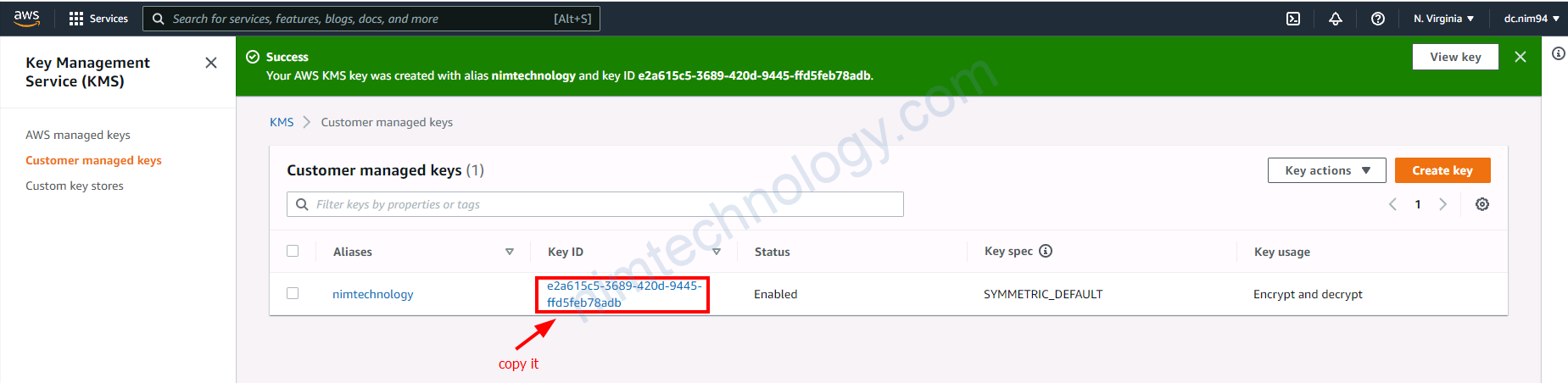
4.1) Create the customer managed key
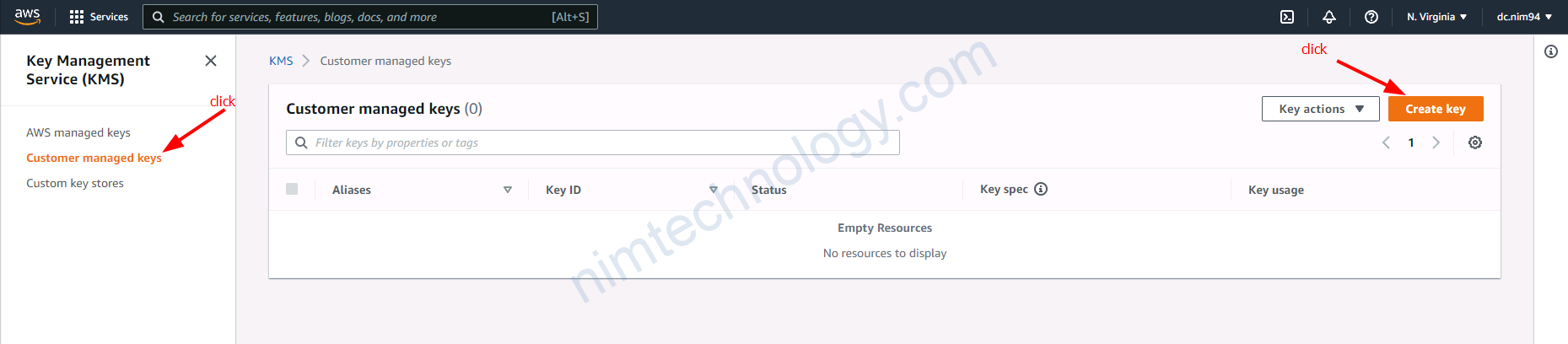
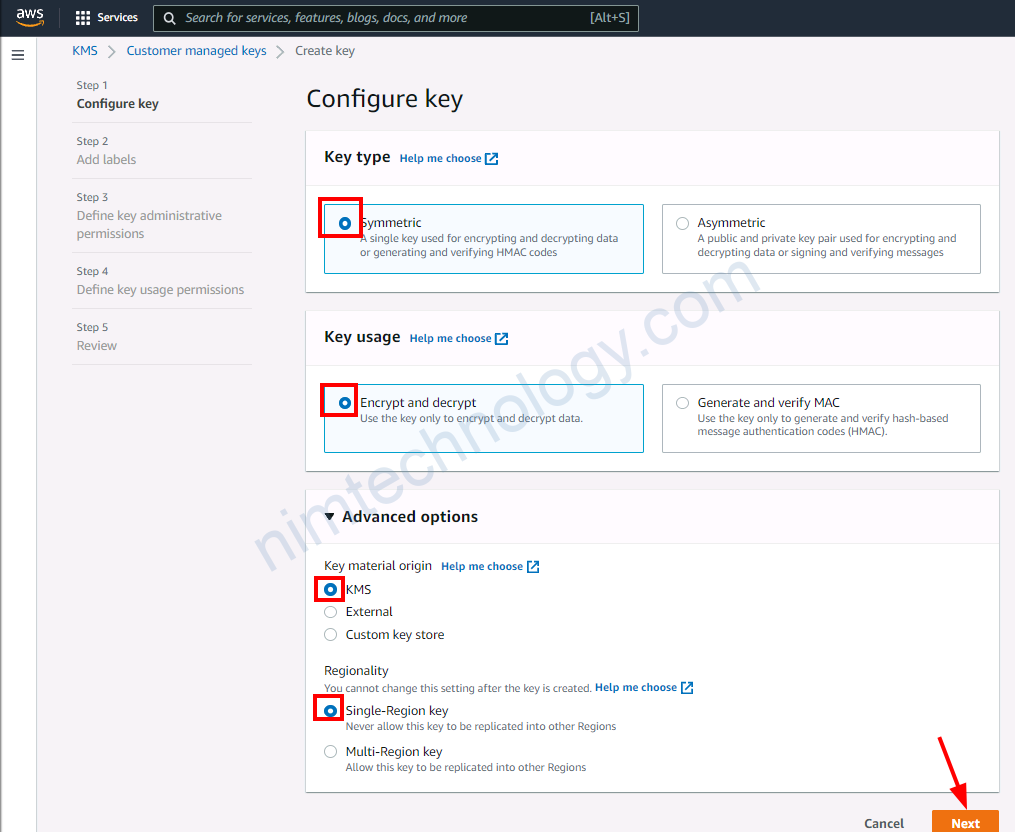
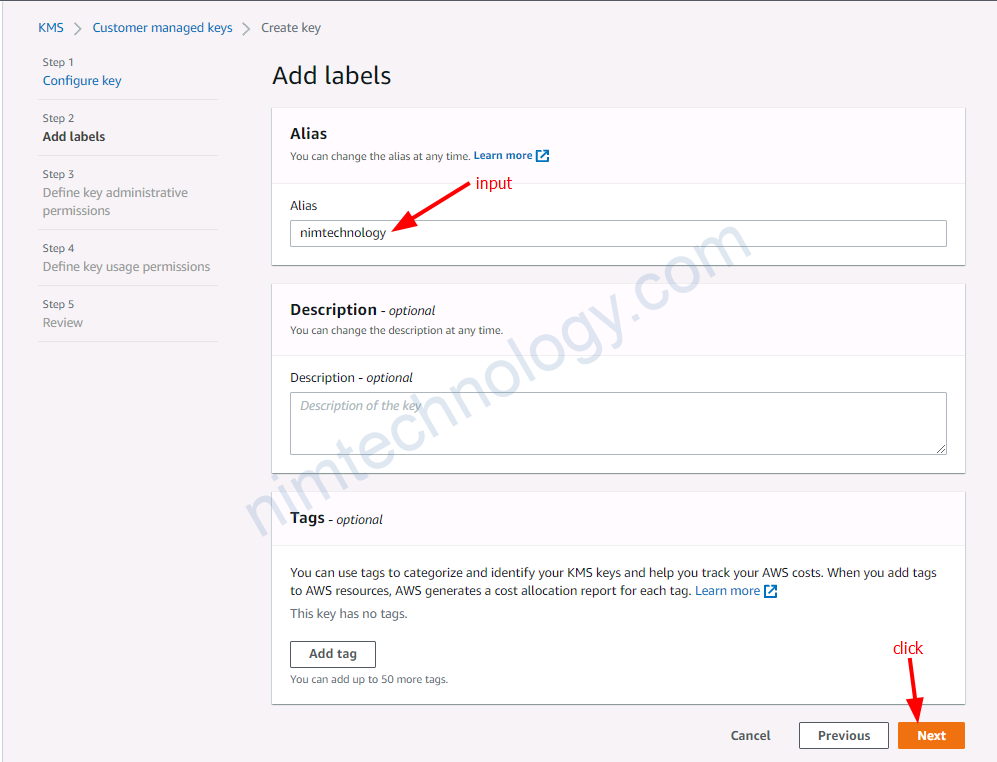
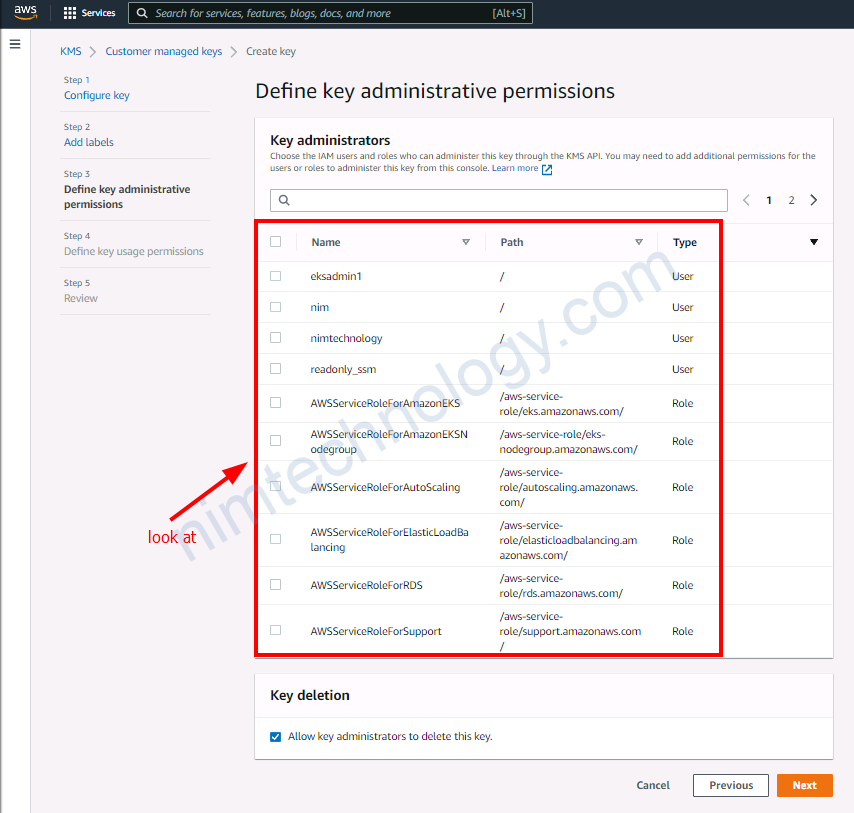
Chỗ define key administrative permission:
nghĩa là ta sẽ chọn ai sẽ được quản trị key này.
=> Nếu bạn ko chọn thì là tất cả các user này!
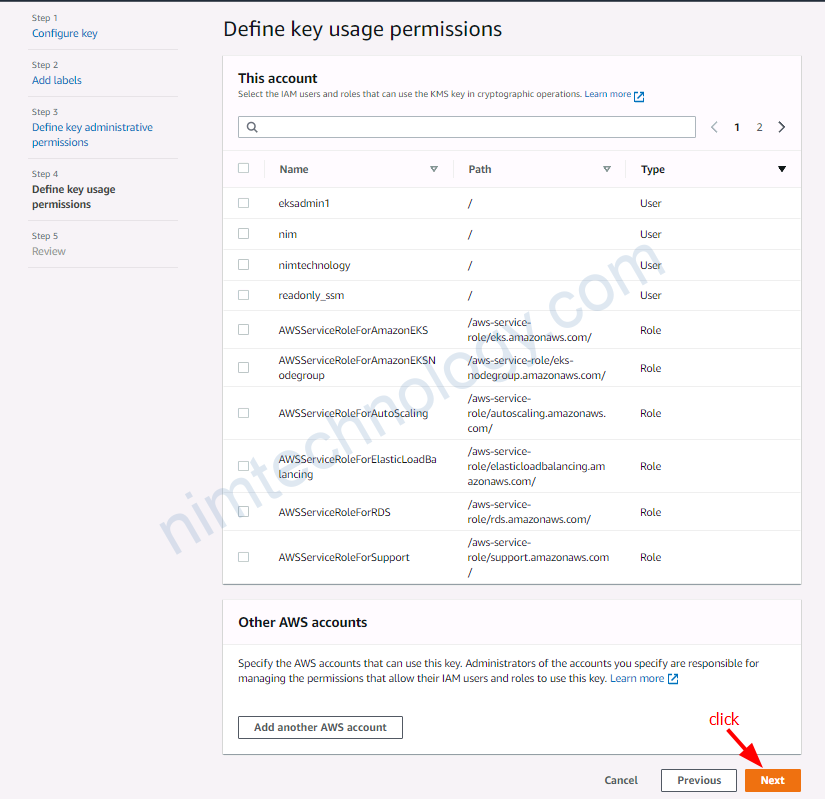
Ai được quyền mã hóa
ai được quền giải mã
Ở đây mình không chọn nên là phải mở tất cả!
Tiếp đến review lại và ấn Finish.
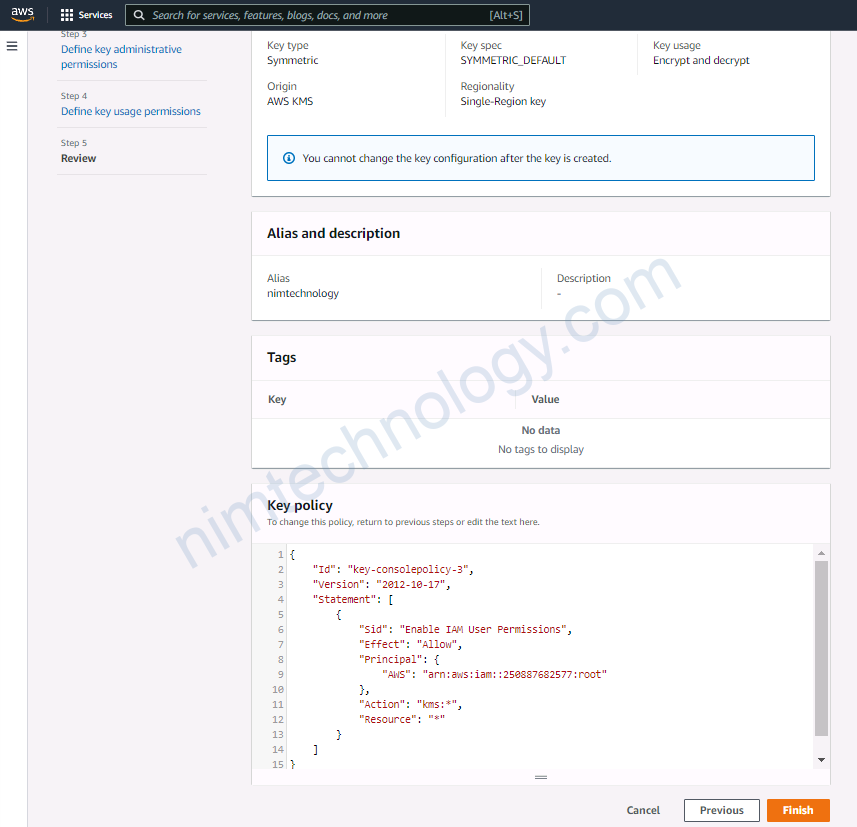
{
"Id": "key-consolepolicy-3",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::250887682577:root"
},
"Action": "kms:*",
"Resource": "*"
}
]
}
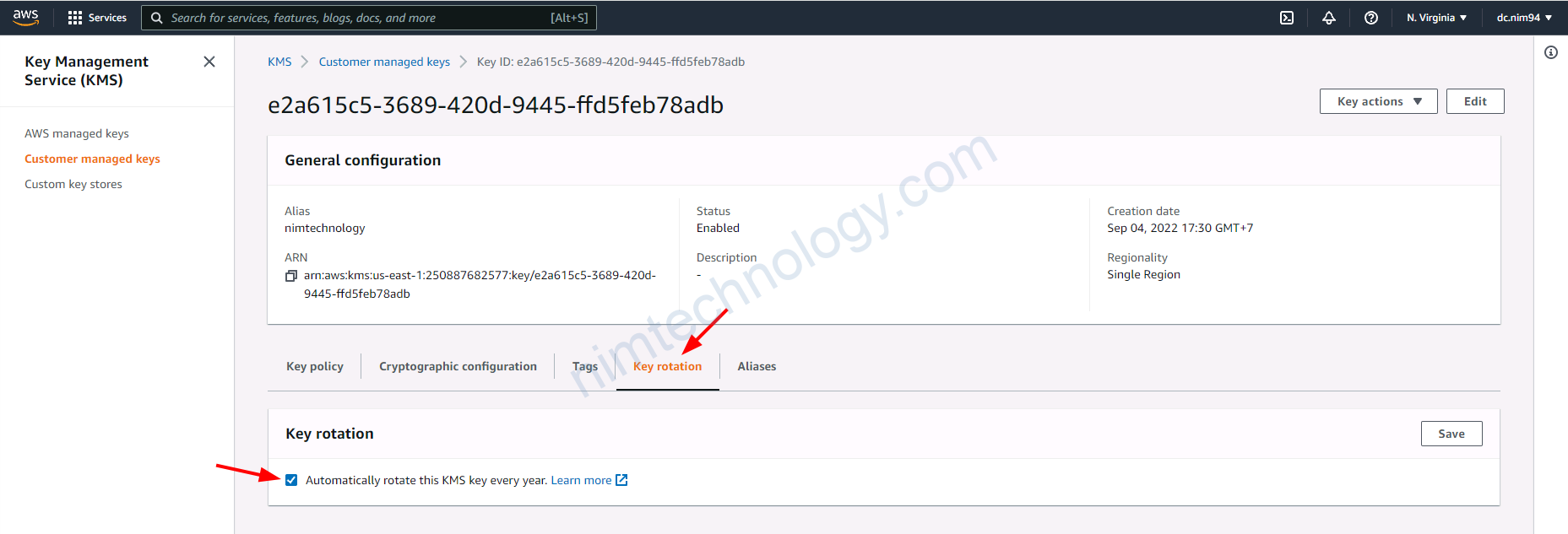
Giờ vào custom key này chút
==> thực hiện rotation key mỗi năm
4.2) Encrypt data through KMS – AWS
https://docs.aws.amazon.com/cli/latest/reference/kms/encrypt.html
Giờ thực hiện run command
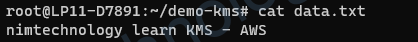
aws kms encrypt \
--key-id e2a615c5-3689-420d-9445-ffd5feb78adb \
--plaintext fileb://data.txt \
--output text \
--query CiphertextBlob | base64 \
--decode > dataEncryptedFile

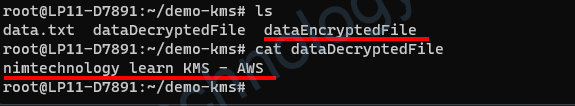
4.3) Decrypt data through KMS – AWS
https://docs.aws.amazon.com/cli/latest/reference/kms/decrypt.html
aws kms decrypt \
--ciphertext-blob fileb://dataEncryptedFile \
--key-id e2a615c5-3689-420d-9445-ffd5feb78adb \
--output text \
--query Plaintext | base64 \
--decode > dataDecryptedFile
4.4) Delete Customer managed key
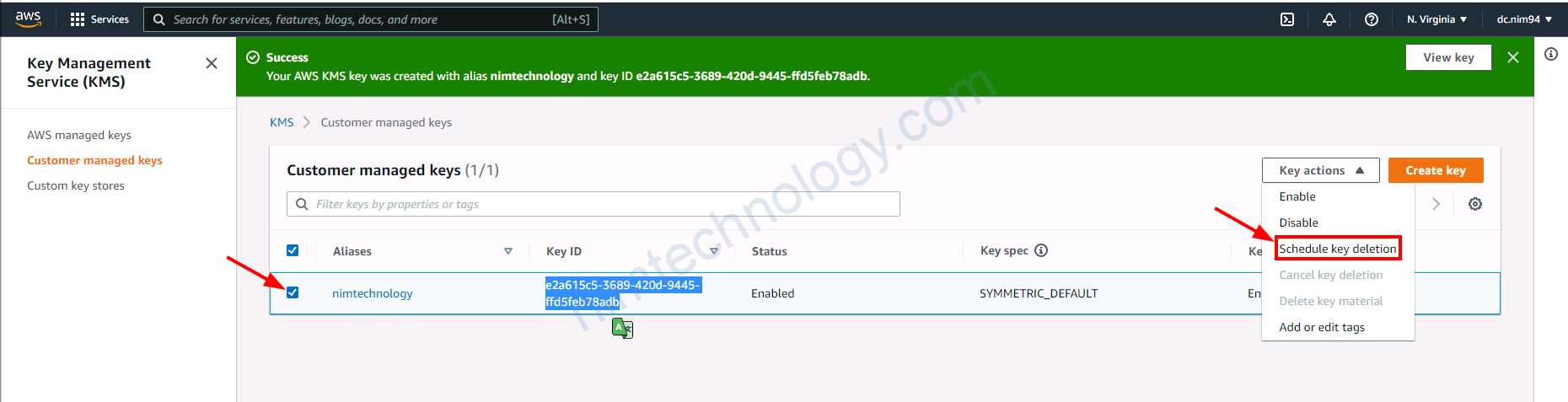
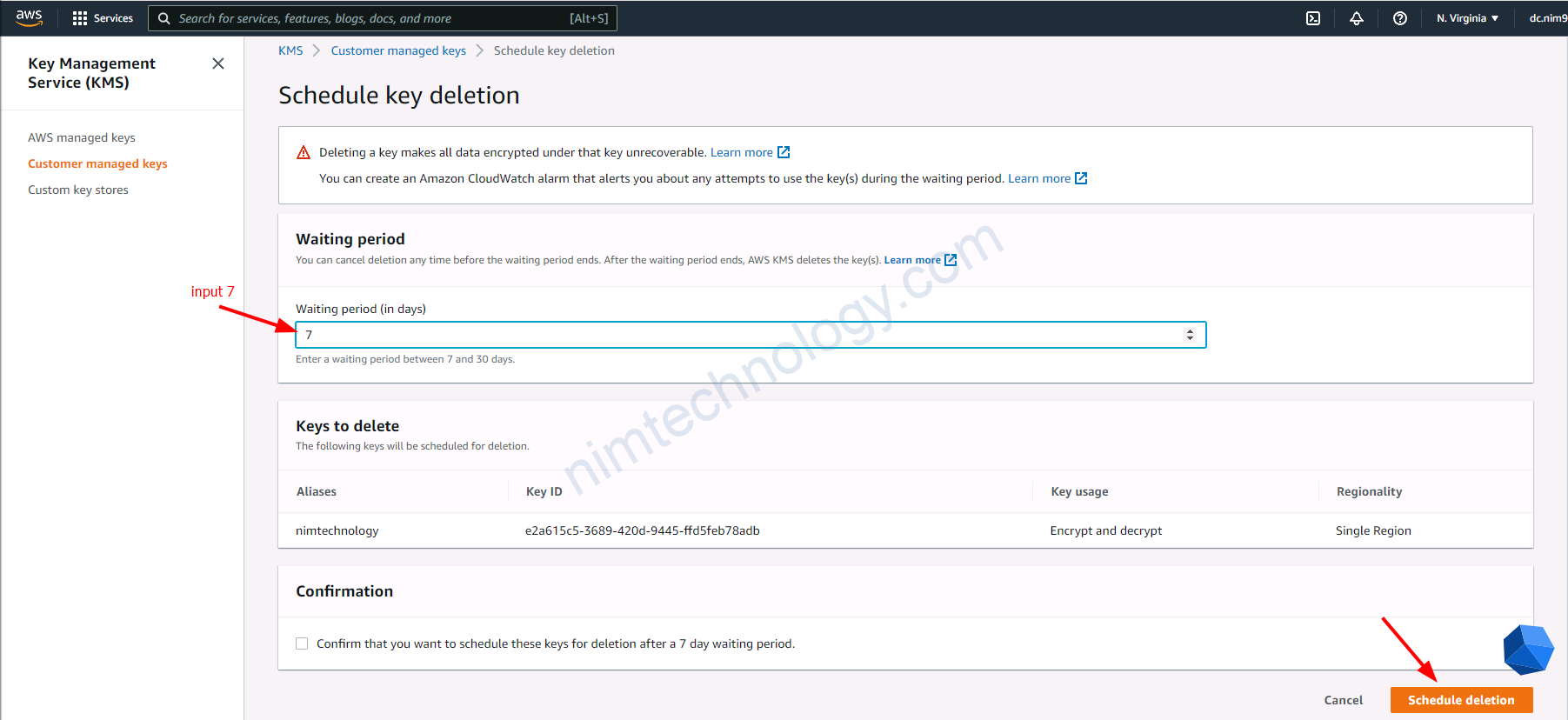
Mình sẽ cần đặt là 7 ngày sau nó sẽ delete
4.5) KMS Other account.
Giờ mình có 1 account Với ID như ảnh

Giờ mình muốn user thuộc Account ID: 2508-8768-2577 có thể sửa dụng KMS trên ảnh
Đầu tiên mĩnh sẽ sửa key policy ở ảnh trên:
{
"Version": "2012-10-17",
"Id": "key-default-1",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::794155915849:root"
},
"Action": "kms:*",
"Resource": "*"
},
// Below content of other AWS account
{
"Sid": "Enable IAM User Permissions of other AWS account",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::250887682577:root"
},
"Action": "kms:*",
"Resource": "*"
}
]
}

"Principal": {
"AWS": "arn:aws:iam::250887682577:root"
},khi config là root nó sẽ open cho tất cả các user trong account0 250887682577 đều có thể encrypt và decrypt.
aws kms encrypt \
--profile dev-nimtechnology-engines \
--key-id b6713452-966f-4348-90bf-d5083f8f1fdc \
--plaintext fileb://data.txt \
--output text \
--query CiphertextBlob | base64 \
--decode > dataEncryptedFile
# be different region
# specify profile
aws kms decrypt \
--region us-west-2 \
--profile eksadmin1 \
--ciphertext-blob fileb://dataEncryptedFile \
--key-id b6713452-966f-4348-90bf-d5083f8f1fdc \
--output text \
--query Plaintext | base64 \
--decode > dataDecryptedFile
Giờ mình limit user trong key policy
{
"Version": "2012-10-17",
"Id": "key-default-1",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::794155915849:root"
},
"Action": "kms:*",
"Resource": "*"
},
// Below content of other AWS account
// Particular User
{
"Sid": "Enable IAM User Permissions of other AWS account",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::250887682577:user/eksadmin1"
},
"Action": "kms:*",
"Resource": "*"
}
]
}
Giờ minh thực hiện decrypt
aws kms decrypt \
--region us-west-2 \
--ciphertext-blob fileb://dataEncryptedFile \
--key-id b6713452-966f-4348-90bf-d5083f8f1fdc \
--output text \
--query Plaintext | base64 \
--decode > dataDecryptedFile
==> error
====>
An error occurred (AccessDeniedException) when calling the Decrypt operation: The ciphertext refers to a customer master key that does not exist, does not exist in this region, or you are not allowed to access.
aws kms decrypt \
--region us-west-2 \
--profile eksadmin1 \
--ciphertext-blob fileb://dataEncryptedFile \
--key-id b6713452-966f-4348-90bf-d5083f8f1fdc \
--output text \
--query Plaintext | base64 \
--decode > dataDecryptedFile
===> this ok
4.6) Get key policy to follow KMS
Chúng ta có thể kiểm tra key policy bằng command
aws kms get-key-policy \
--region <region_name> \
--profile <profile_name> \
--key-id arn:aws:kms:<region_name>:<ACCOUNT_ID>:key/<KMS_ID> \
--policy-name default \
--output text
>>>>output
>>>>>>
{
"Version" : "2012-10-17",
"Id" : "key-default-1",
"Statement" : [ {
"Sid" : "Enable IAM User Permissions",
"Effect" : "Allow",
"Principal" : {
"AWS" : "arn:aws:iam::2923917XXXXX:root"
},
"Action" : "kms:*",
"Resource" : "*"
} ]
}
4.7) Edit key policy to follow KMS
giờ bạn chỉnh sửa key policy của KMS bằng aws cli
vi key_policy_flatform.json
{
"Version" : "2012-10-17",
"Id" : "key-default-1",
"Statement" : [ {
"Sid" : "Enable IAM User Permissions",
"Effect" : "Allow",
"Principal" : {
"AWS" : "arn:aws:iam::2923917XXXXX:root"
},
"Action" : "kms:*",
"Resource" : "*"
} ]
}
aws kms put-key-policy \
--region <region_name> \
--profile <profile_name> \
--key-id arn:aws:kms:us-west-2:<ACCOUNT_ID>:key/<KMS_ID> \
--policy-name default \
--policy file://key_policy_flatform.json