1) Overview!
Trước đây để cài eks windows hay là k8s windows trên aws chúng ta sẽ lựa chọn mode self managed node Group. Bạn có thể tham khảo ở đây: https://nimtechnology.com/2022/09/25/aws-creating-eks-windows-on-aws-and-running-windows-pods/
Hiện tại có 1 tin là terraform module đã Native support for Windows based managed nodegroups similar to AL2 and Bottlerocket
https://github.com/terraform-aws-modules/terraform-aws-eks/releases/tag/v20.0.0
Bạn có thể tham khoa template terraform để provisioning eks windows:
https://github.com/mrnim94/terraform-aws-eks-windows/blob/issue/can-not-assign-ip-to-windows-pods/c3-02-eks.tf
On EKS Windows, windows pods can not resolve any domains.
Check the inbound Security Group.
Nếu bạn gặp trường hợp là pod trên windows không thể phân giải được bất cứ domain nào thì chúng ta inspect từng bước nhé
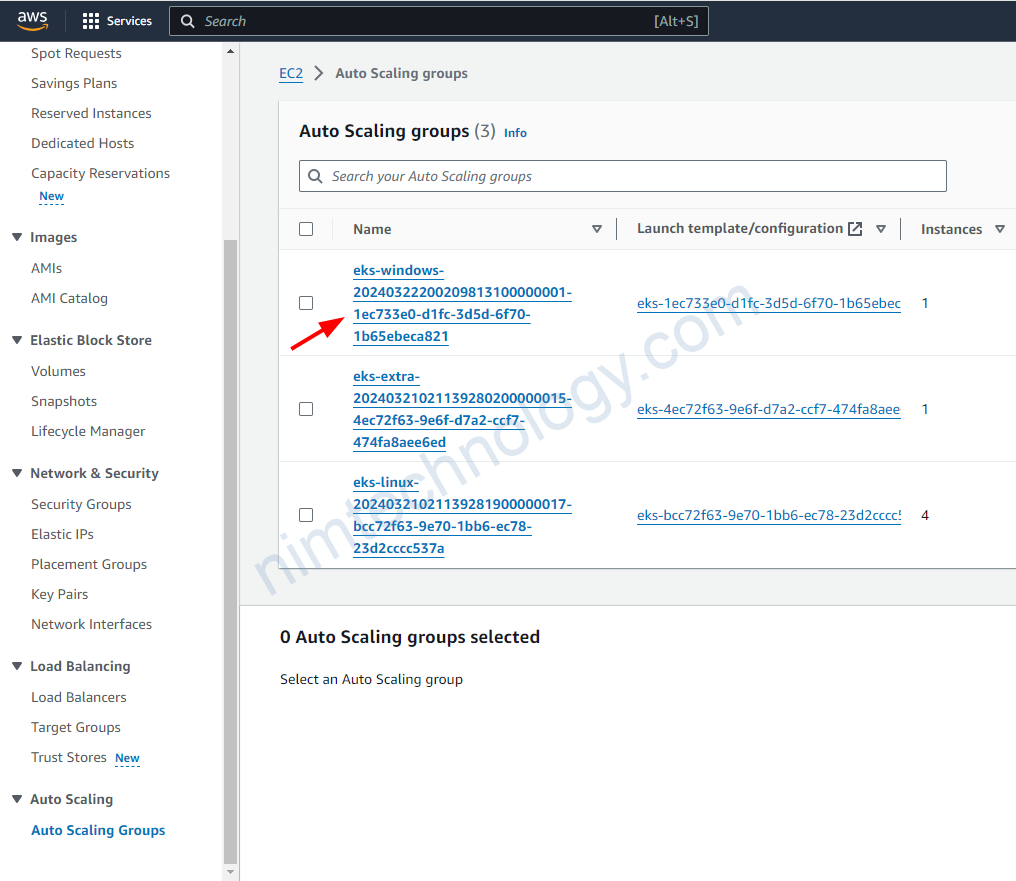
Trong Autoscaling Group chúng ta đang có 3 groups.
Đây là con windows instance:
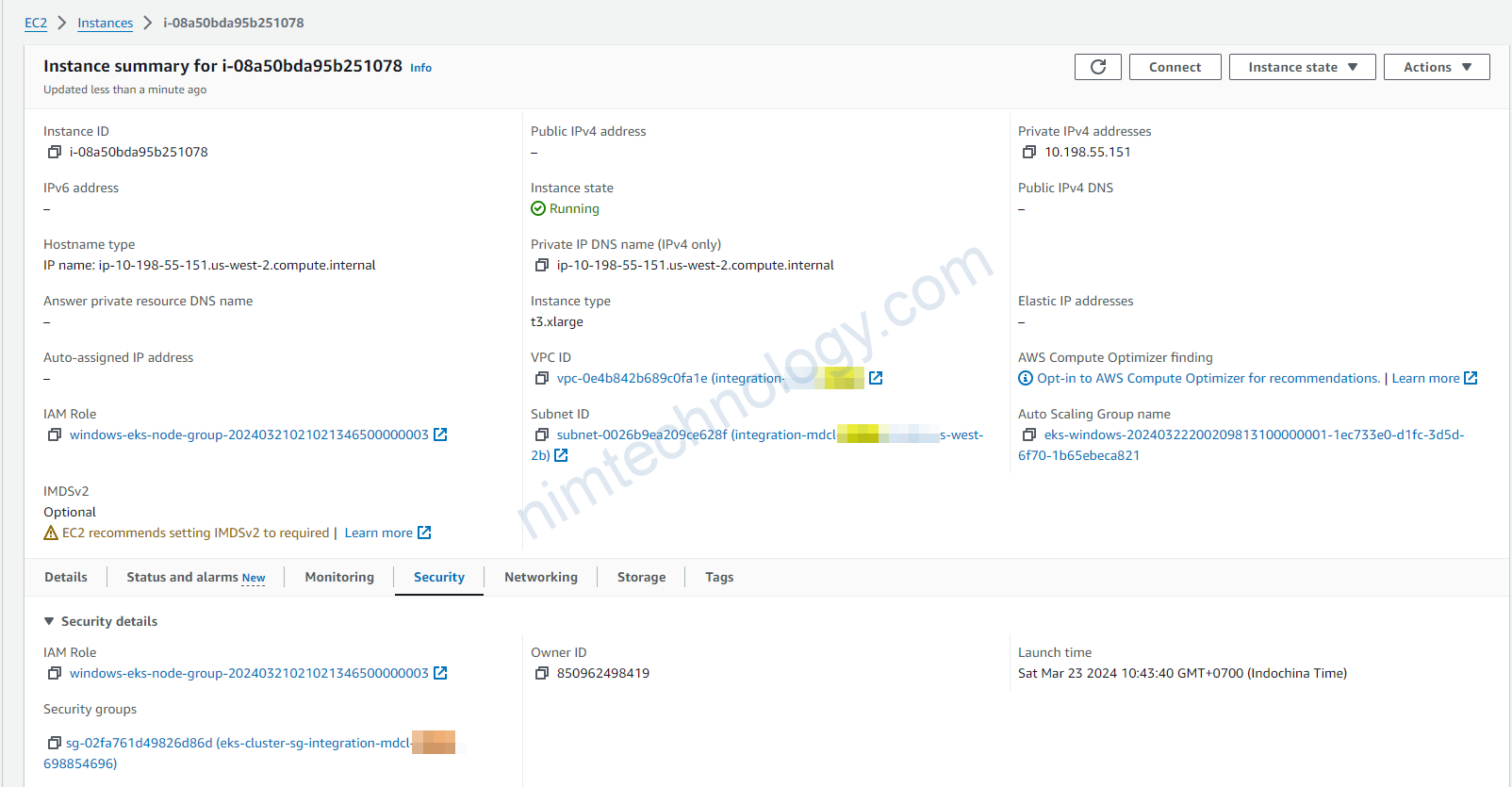
Windows instance đang sử dụng Security Group là: sg-02fa761d49826d86d
Đầu tiên cần test là windows pod có kết nối được đến service IP của coredns chưa nhé.
Nếu rồi thì chúng ta sẽ cần kiểm tra Security Group:
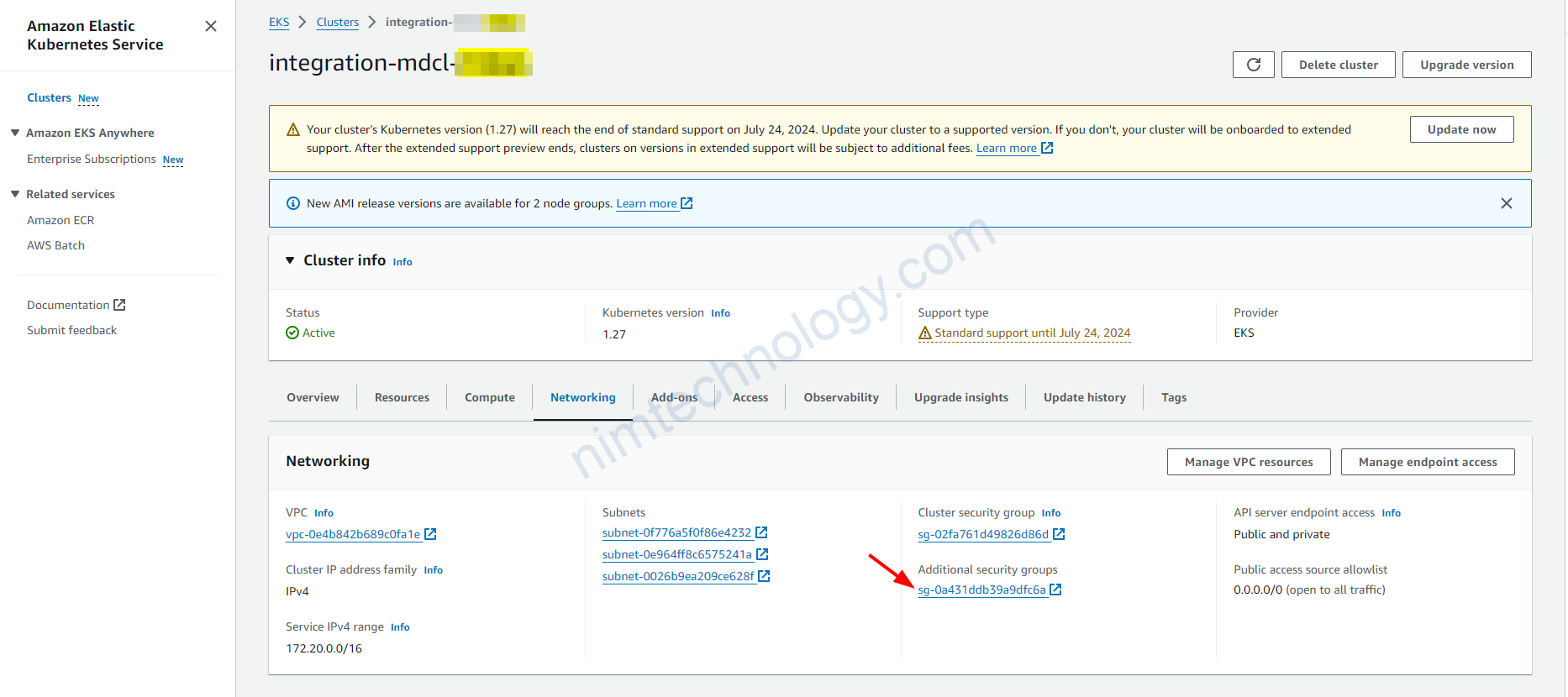
Bạn sẽ cần kiểm tra giúp mình cái Aditional Security Group:
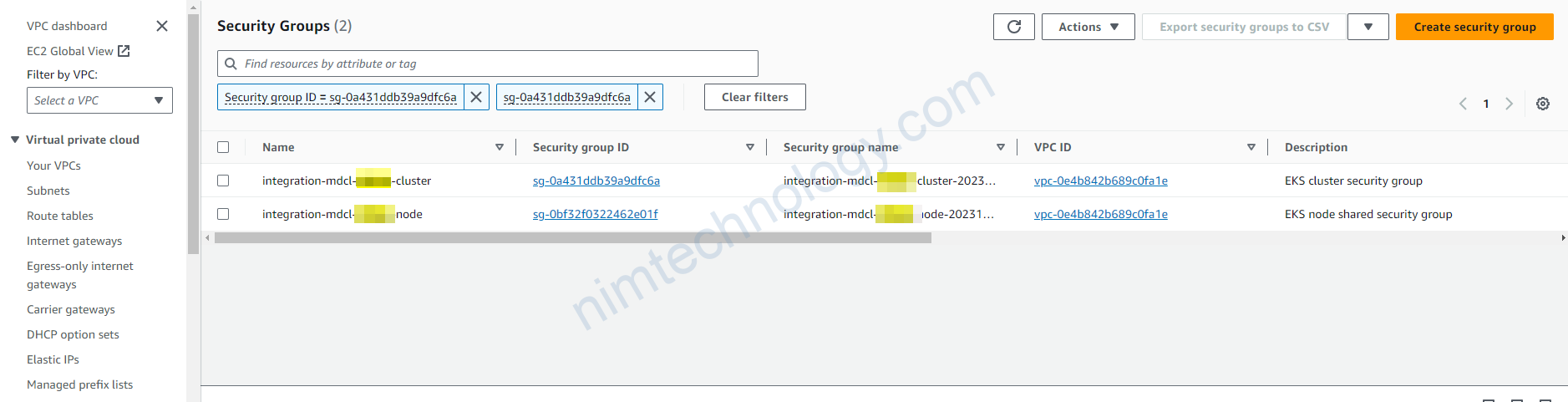
Nếu bạn tìm Aditional Security Group thì nó sẽ hiện 2 SecGroup luôn nhé!
Bạn sẽ đi vào SecGroup mà to be like: xxxx-node và Description của nó là: EKS node shared security group
Thường nó nó sẽ là Security Group đang được apply cho Linux Node.

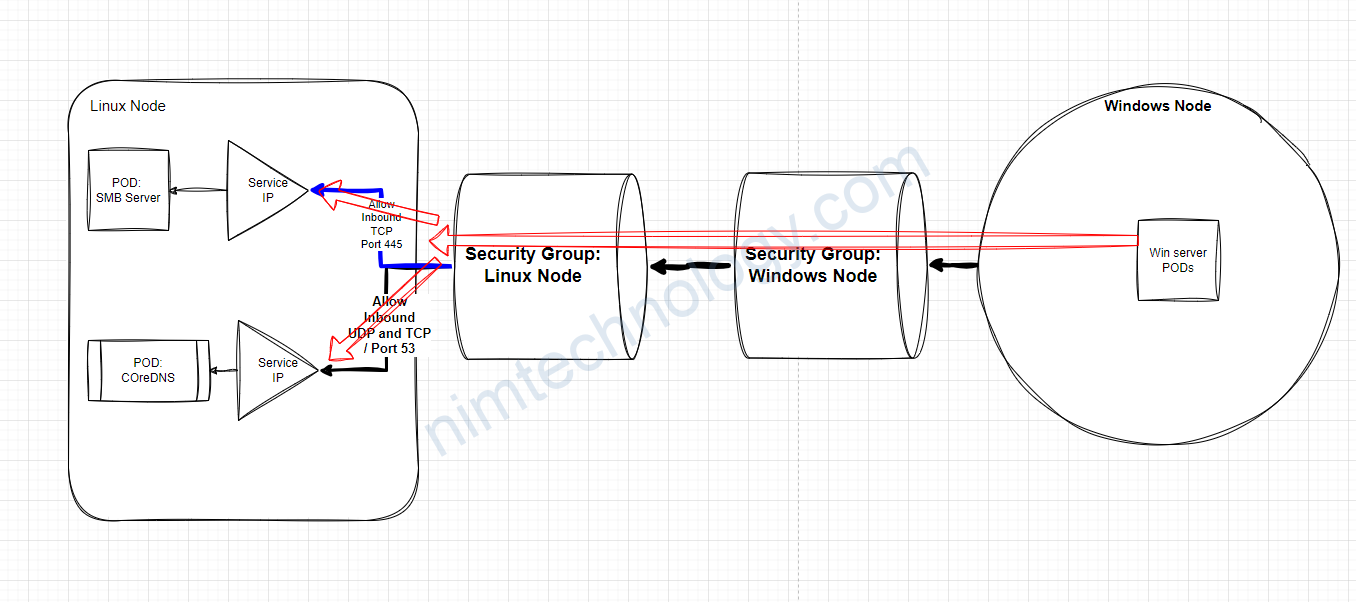
Bạn có thể hiểu như hình:
Và mình đã chọn 1 các dễ dàng là allow all traffic luôn
Tóm lại là bạn sẽ cần cấu hình trong Aditional Security Group cho phép các con windows connect thông qua các điều kiện sau:
protocol: ALL TCP and UDP.
Range port: all port
Source: Security Group is attached to Windows instances, VPC cidr, or subnet cidr.
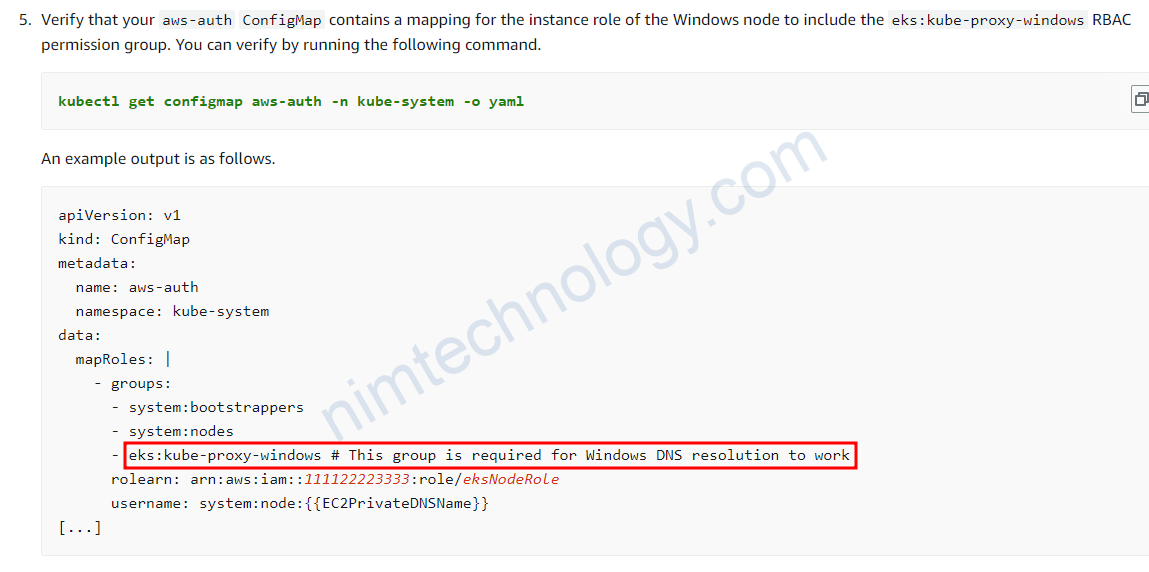
Re-check IAM access entries and aws-auth config map in K8S
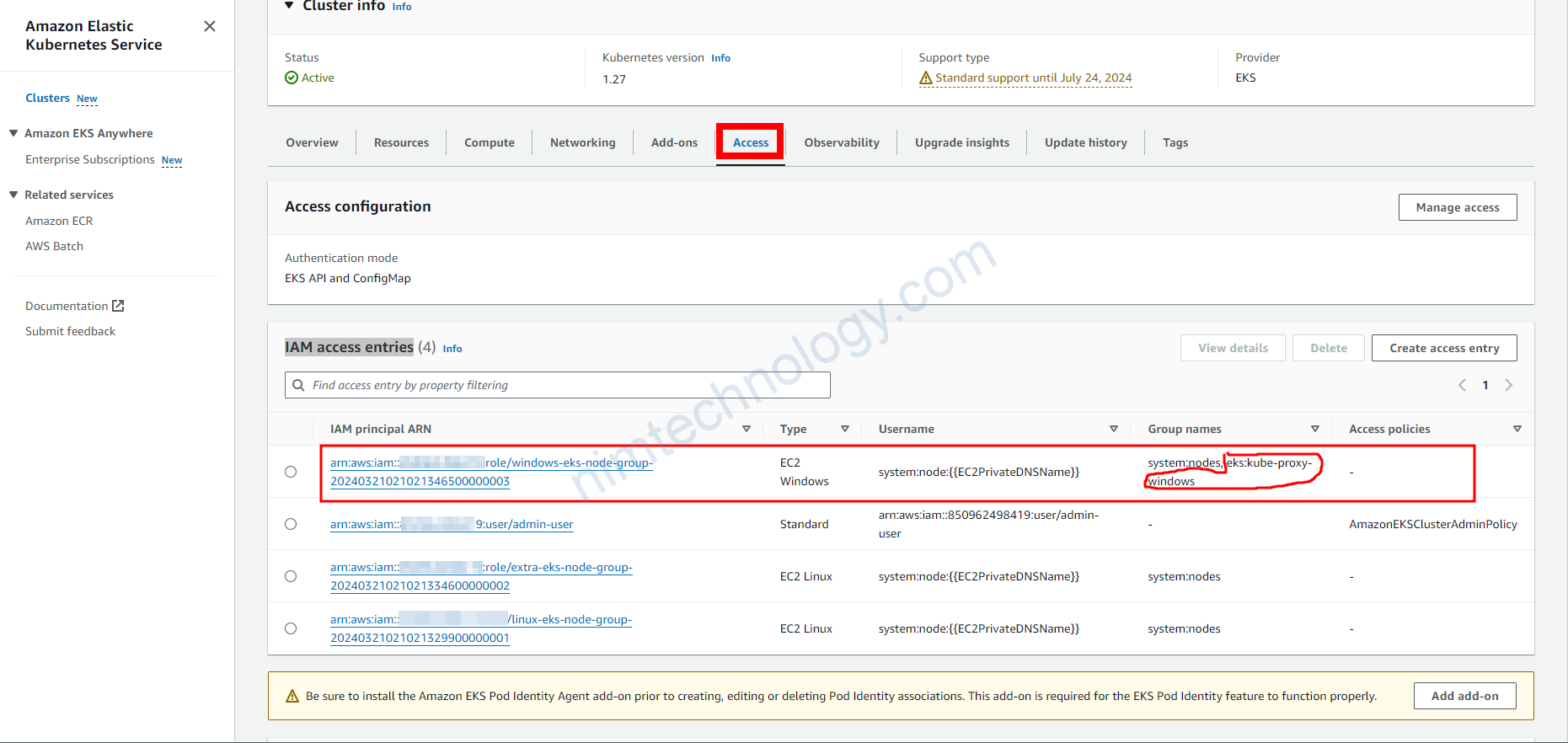
Bạn cần kiêm tra access entries thì ARN windows -> Group name: is there the "eks:kube-proxy-windows"
và config map của k8s có tương ứng như vậy không?
https://docs.aws.amazon.com/eks/latest/userguide/windows-support.html
Windows pods are assigned IPs.
Đầu tiên bạn cần check là các on pod hay deployment, ect đã được attached “” No selector Windows hay chưa?
dnsPolicy: ClusterFirst
########################
nodeSelector:
kubernetes.io/os: windows
##############################
priorityClassName: system-node-critical
enable-windows-ipam: “true” is declared in amazon-vpc-cni ConfigMap?
apiVersion: v1 kind: ConfigMap metadata: name: amazon-vpc-cni namespace: kube-system data: enable-windows-ipam: "true"
User Data of Windows nodes:
I see that terraform-aws-eks creates use_data based on my pre_bootstrap_user_data.
Next, it is merged with any user_data(*) that has a configuration to access the EKS controller created by EKS controller AWS.
Windows user data uses PowerShell commands. When creating a managed node group, your custom user data combines with Amazon EKS managed user data. Your PowerShell commands come first, followed by the managed user data commands, all within one <powershell></powershell> tag.
When no AMI ID is specified in the launch template, don’t use the Windows Amazon EKS Bootstrap script in user data to configure Amazon EKS.
Example user data is as follows.
<powershell> Write-Host "Running custom user data script" </powershell>
refer to:
https://docs.aws.amazon.com/eks/latest/userguide/launch-templates.html#launch-template-user-data
EKS windows with Manage node Group:
Bạn có thể sử dụng module eks-windows with version greater 3.0.5