Mình cũng đã có 1 vài bài nói về kaniko và run kaniko trên k8s để build image
Hôm này chúng ta sẽ đến 1 bài là:
CI bằng bitbucket-pipeline
Build image bằng Kaniko
Sau đó push image lên ECR của AWS.
1) design bitbucket-pipelines
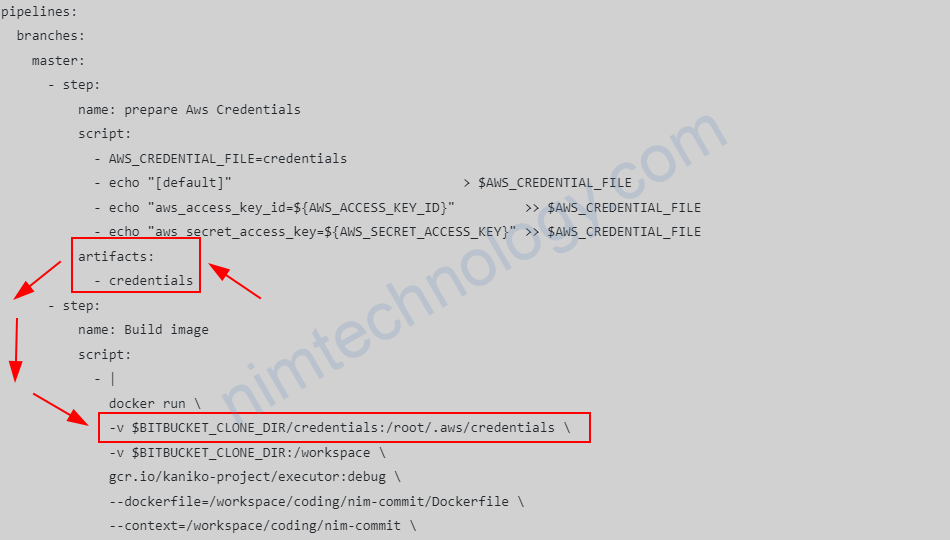
Đầu tiên mình có file bitbucket-pipelines.yml
pipelines:
branches:
master:
- step:
name: prepare Aws Credentials
script:
- AWS_CREDENTIAL_FILE=credentials
- echo "[default]" > $AWS_CREDENTIAL_FILE
- echo "aws_access_key_id=${AWS_ACCESS_KEY_ID}" >> $AWS_CREDENTIAL_FILE
- echo "aws_secret_access_key=${AWS_SECRET_ACCESS_KEY}" >> $AWS_CREDENTIAL_FILE
artifacts:
- credentials
- step:
name: Build image
script:
- |
docker run \
-v $BITBUCKET_CLONE_DIR/credentials:/root/.aws/credentials \
-v $BITBUCKET_CLONE_DIR:/workspace \
gcr.io/kaniko-project/executor:debug \
--dockerfile=/workspace/coding/nim-commit/Dockerfile \
--context=/workspace/coding/nim-commit \
--destination=250887682577.dkr.ecr.us-east-1.amazonaws.com/nim-commit:$BITBUCKET_BUILD_NUMBER \
--use-new-run
services:
- docker
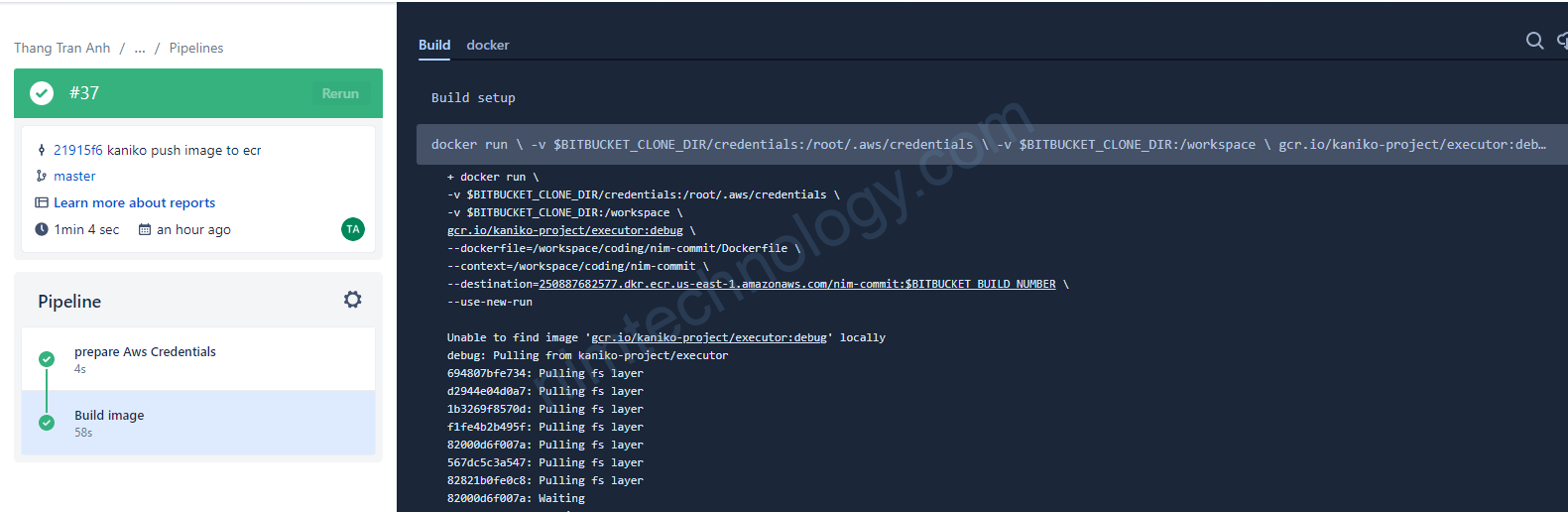
2) Kaniko push image to ECR
Đầu tiền mình sẽ cần phải nắm được làm sao để kaniko có thể push lên ECR:
https://github.com/GoogleContainerTools/kaniko#pushing-to-amazon-ecr
Mình chọn cách là tạo file credentials và mount nó vào folder /root/.aws/
Tiếp theo mình dụng artifacts của bitbucket-pipeline để sử dụng nó ở nhiều steps
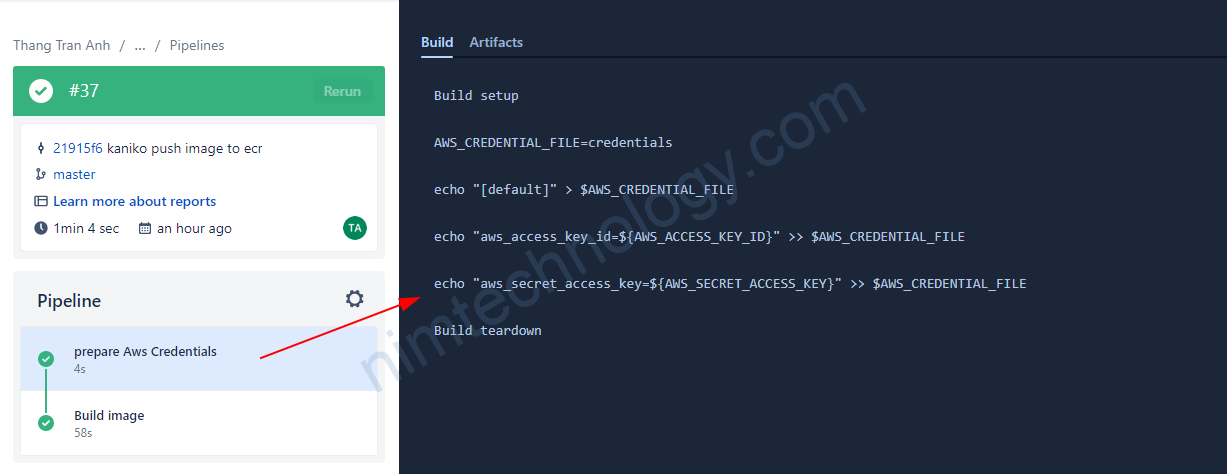
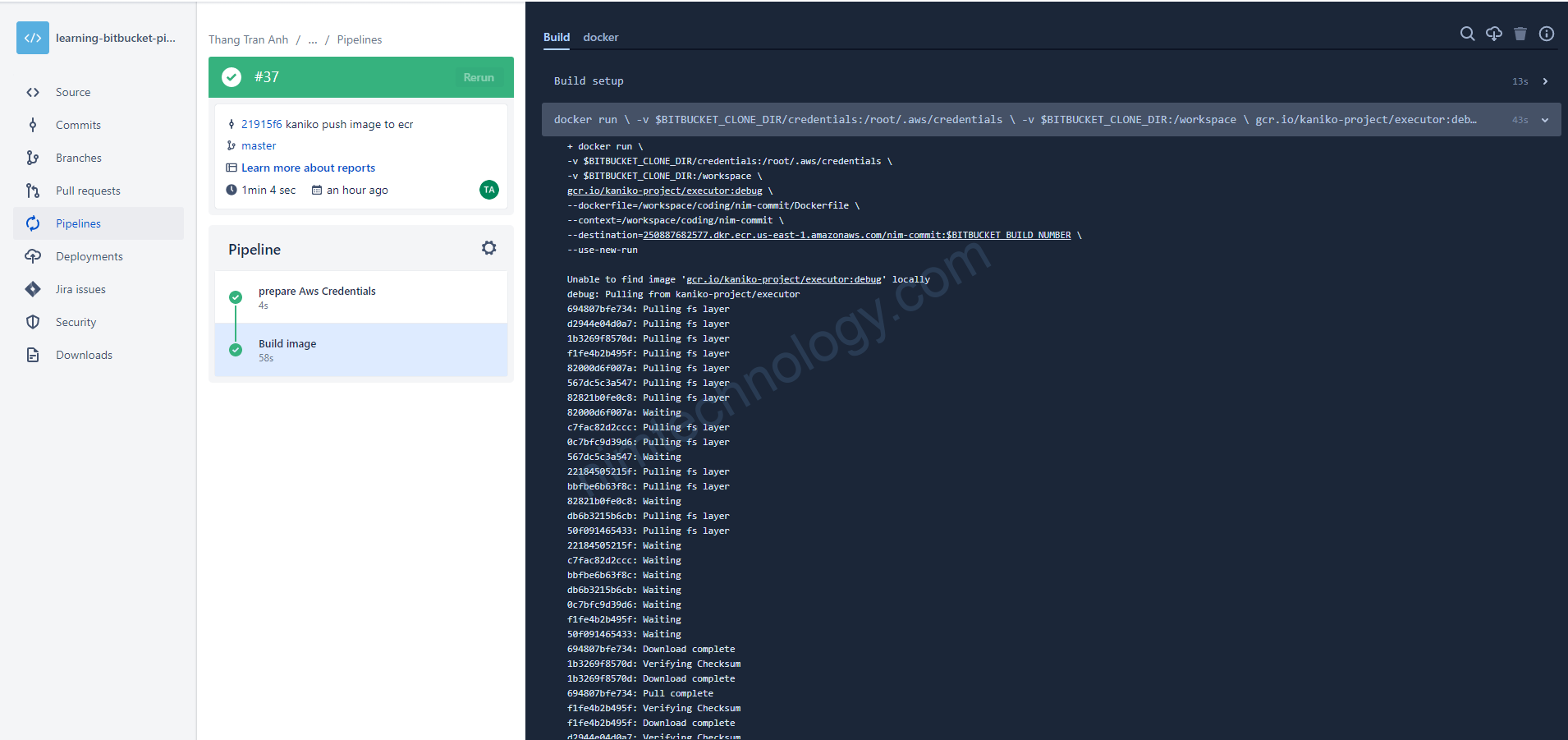
phần sau là push code lên và bitbucket sẽ build cho cúng ta.
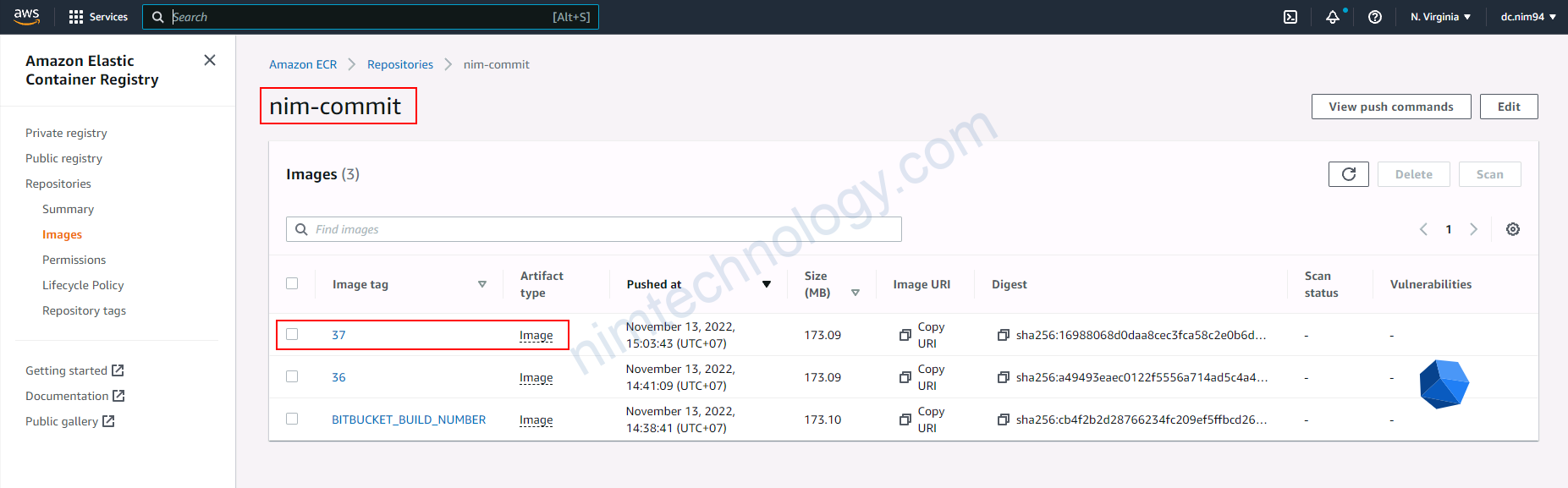
OK giở recheck là image đã được push lên ecr chưa?
3) Kaniko push image to Dockerhub or Harbor.
bạn đi vào project và tạo account robot
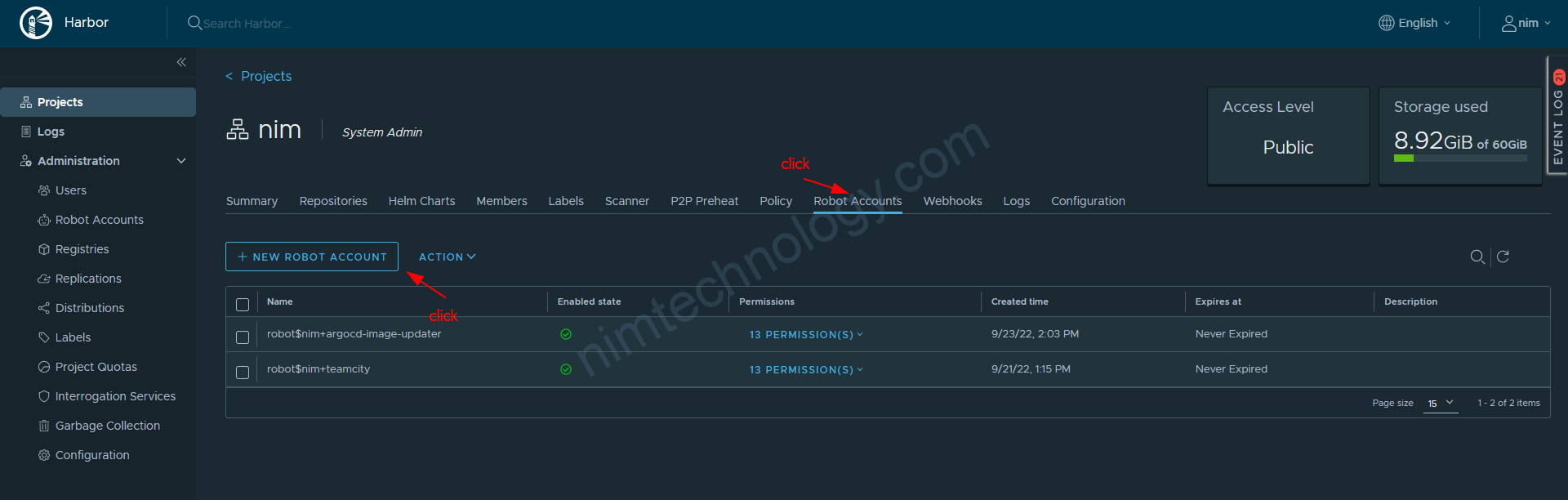

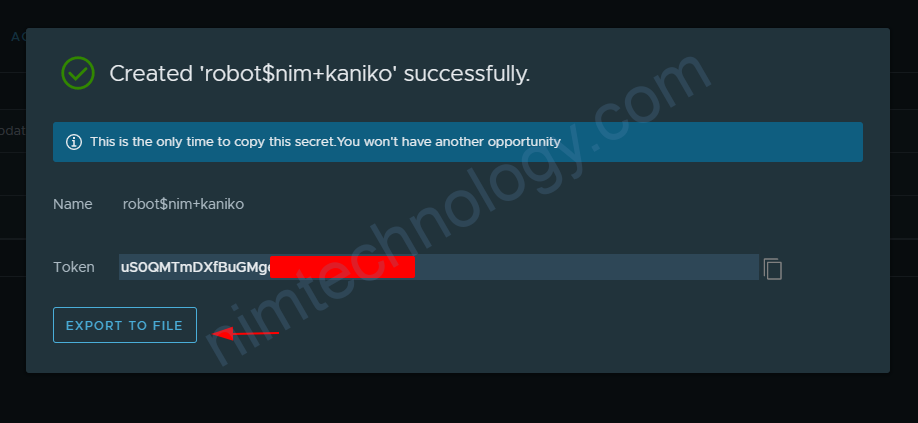
echo -n 'USER_NAME:PASS_WORD' | base64 echo -n 'robot$nim+kaniko:uS0QMTmDXfBuGMgecExxxxxxxxxx' | base64 cm9ib3Qra2FuaWtvOnVTMFFNVG1EWGZCdUdNZ2VjRTdwxxxxxxxx==
encode base64 hay encrypt base64

Hoặc cách khác là bạn login rồi copy nội dụng trong file .docker/config.json
Sau khi có tocken thì bạn tạo content cho file config.json
config.json
>>>>>>
{
"auths": {
"docker.nimtechnology.com": {
"auth": "cm9ib3QkbmltK2thbmlrbzp1UzBRTVRtRFhmQnVHTWdlY0U3cGFxxxxxxxxxxxxxxxxx=="
}
}
}
giờ bạn tạo file bitbucket-pipelines.yml
pipelines:
branches:
master:
- step:
name: prepare Harbor Credentials
script:
- HARBOR_CREDENTIAL_FILE=config.json
- echo "${HARBOR_CREDENTIAL}" > $HARBOR_CREDENTIAL_FILE
artifacts:
- config.json
- step:
name: Build image
script:
- cat $BITBUCKET_CLONE_DIR/config.json
- |
docker run \
-v $BITBUCKET_CLONE_DIR/config.json:/kaniko/.docker/config.json:ro \
-v $BITBUCKET_CLONE_DIR:/workspace \
gcr.io/kaniko-project/executor:debug \
--dockerfile=/workspace/coding/nim-commit/Dockerfile \
--context=/workspace/coding/nim-commit \
--destination=docker.nimtechnology.com/nim/nim-commit:$BITBUCKET_BUILD_NUMBER \
--use-new-run
services:
- docker
4) Review and consult the bitbucket-pipe.yaml from a branch to fetch code for development on a different branch.
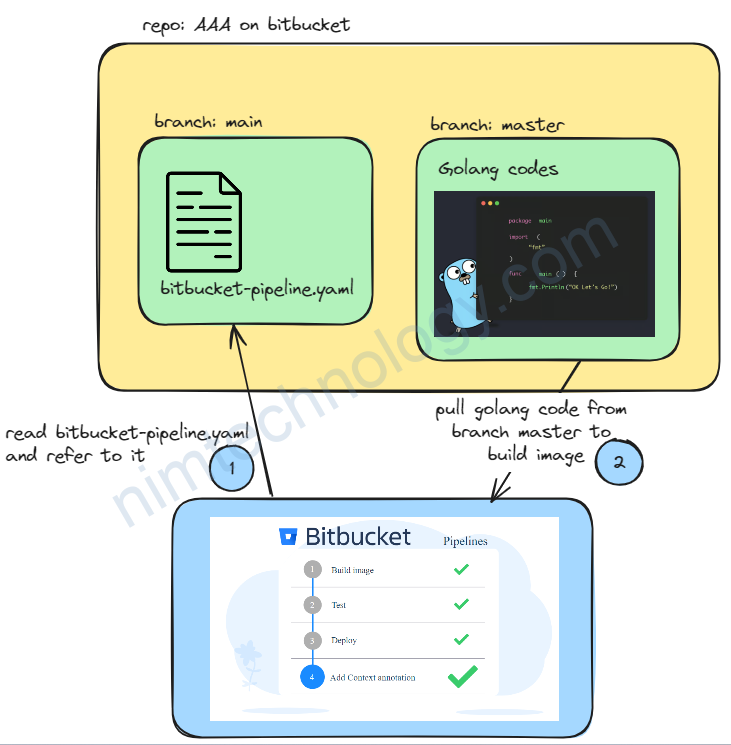
Mình đọc file bitbucket-pipe.yaml từ branch main. Nhưng nó pull code từ branch master để build.
image: atlassian/default-image:2
pipelines:
custom:
build-image:
- step:
name: prepare Aws Credentials Dev
deployment: 0437011XXXXXX-dev
script:
- AWS_CREDENTIAL_FILE=credentials_dev
- echo "[default]" > $AWS_CREDENTIAL_FILE
- echo "aws_access_key_id=${AWS_ACCESS_KEY_ID}" >> $AWS_CREDENTIAL_FILE
- echo "aws_secret_access_key=${AWS_SECRET_ACCESS_KEY}" >> $AWS_CREDENTIAL_FILE
artifacts:
- credentials_dev
- step:
name: Build image Dev
script:
- |
apt-get update && apt-get install -y git jq
# Clone GitHub repo
git clone https://$BITBUCKET_USERNAME:$BITBUCKET_APP_PASSWORD@bitbucket.org/nim/rotation-key.git
cd rotation-key
git checkout master
cd ..
docker run \
-v $BITBUCKET_CLONE_DIR/credentials_dev:/root/.aws/credentials \
-v $BITBUCKET_CLONE_DIR/rotation-key:/workspace \
gcr.io/kaniko-project/executor:debug \
--dockerfile=Dockerfile \
--context=/workspace \
--destination=043701111869.dkr.ecr.us-west-2.amazonaws.com/rotation-key:$BITBUCKET_BUILD_NUMBER \
--use-new-run
services:
- docker
Ngoài ra nếu bạn có thể apply to build image via session token.
Bạn sẽ cần setup environments cho pipeline:
pipelines:
branches:
kang-tva:
- step:
name: prepare Aws Credentials Dev
deployment: 0000000000-nim-dev
script:
# Authenticate and generate Docker config file for ECR
- aws ecr get-login-password --region us-west-2 | docker login --username AWS --password-stdin 0000000000.dkr.ecr.us-west-2.amazonaws.com
# - mkdir -p /root/.docker
- cat ~/.docker/config.json > docker_config.json # Save Docker config as an artifact
artifacts:
- docker_config.json
- step:
name: Build image Dev
script:
- |
docker run \
-v $BITBUCKET_CLONE_DIR/docker_config.json:/kaniko/.docker/config.json:ro \
-v $BITBUCKET_CLONE_DIR:/workspace \
gcr.io/kaniko-project/executor:debug \
--dockerfile=/workspace/coding/kang-tva/src/Dockerfile \
--context=/workspace/coding/kang-tva/src \
--destination=0000000000.dkr.ecr.us-west-2.amazonaws.com/devops/kang-tva:$BITBUCKET_BUILD_NUMBER \
--use-new-run
docker run \
-v $BITBUCKET_CLONE_DIR/docker_config.json:/kaniko/.docker/config.json:ro \
-v $BITBUCKET_CLONE_DIR:/workspace \
gcr.io/kaniko-project/executor:debug \
--dockerfile=/workspace/coding/kang-tva/src/Dockerfile \
--context=/workspace/coding/kang-tva/src \
--destination=0000000000.dkr.ecr.us-west-2.amazonaws.com/devops/kang-tva:latest \
--use-new-run
services:
- docker
Bước 1 sẽ generate file ~/.docker/config.json và mình thực hiện mount file này vào kaniko container.