ChatGPT:
When an Amazon EC2 instance needs to access Amazon S3, the traffic will typically stay within the internal AWS network rather than going out to the public internet. This is because Amazon S3 and Amazon EC2 are both services provided by AWS, and AWS provides private connectivity between these services through its Virtual Private Cloud (VPC) networking feature.
By default, when you launch an EC2 instance within a VPC, the instance is assigned a private IP address within the VPC’s IP address range. The VPC’s routing tables are then configured to route traffic between the EC2 instance and other services within the VPC, such as Amazon S3.
This means that if you configure your EC2 instance to access S3 using the S3 API or CLI, the traffic will be routed through the internal AWS network rather than going out to the public internet. This provides better performance, security, and reliability compared to accessing S3 over the public internet.
Does traffic between Amazon EC2 and Amazon S3 really go over the internet?
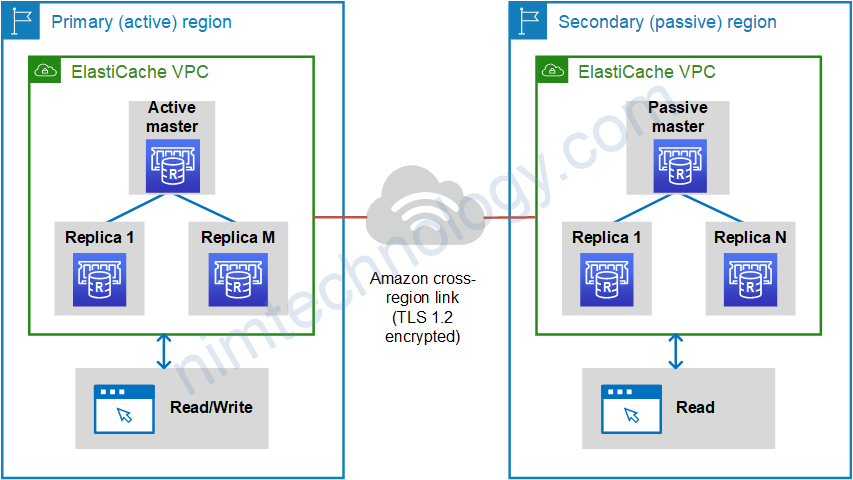
No, even if your AWS resources communicate with each other in the same AWS Region, the network traffic doesn’t go over the internet. However, you do need to use resources such as a NAT Gateway (which incurs additional costs), and an internet gateway (IGW) to make VPC go over the internet. Even traffic between two AWS Regions (such as from your Amazon EC2 instance with a public IP address to an S3 bucket in another commercial Region) will go over AWS Global Backbone. From Building a Scalable and Secure Multi-VPC AWS Network Infrastructure whitepaper:
All network traffic between regions is encrypted, stays on the AWS global network backbone, and never traverses the public internet, thereby reducing threat vectors, such as common exploits and DDoS attacks.
To avoid using an IGW, consider using a VPC endpoint.