1) Bacsic Trivy
Trivy is a simple and comprehensive vulnerability scanner for containers and other artifacts.


docker run --rm -v $WORKSPACE:/root/.cache/ aquasec/trivy:0.17.2 --exit-code 0 --severity HIGH nginxWhen you use --exit-code 0, you are telling Trivy to always return an exit code of 0, regardless of whether vulnerabilities are found or not. This means that even if Trivy detects vulnerabilities that match the specified severity, the command will still be considered successful.
If you want Trivy to return a non-zero exit code when vulnerabilities are found, you can either remove the --exit-code flag or set it to a non-zero value (e.g., --exit-code 1). This way, when vulnerabilities are found during the scan, Trivy will return a non-zero exit code, indicating that there is an issue that needs to be addressed.
docker run --rm -v $WORKSPACE:/root/.cache/ aquasec/trivy:0.17.2 --exit-code 1 --severity HIGH nginx–format value : format (table, json, template) (default: “table”)
–exit-code value : Exit code when vulnerabilities were found (default: 0)
–list-all-pkgs : enabling the option will output all packages regardless of vulnerability
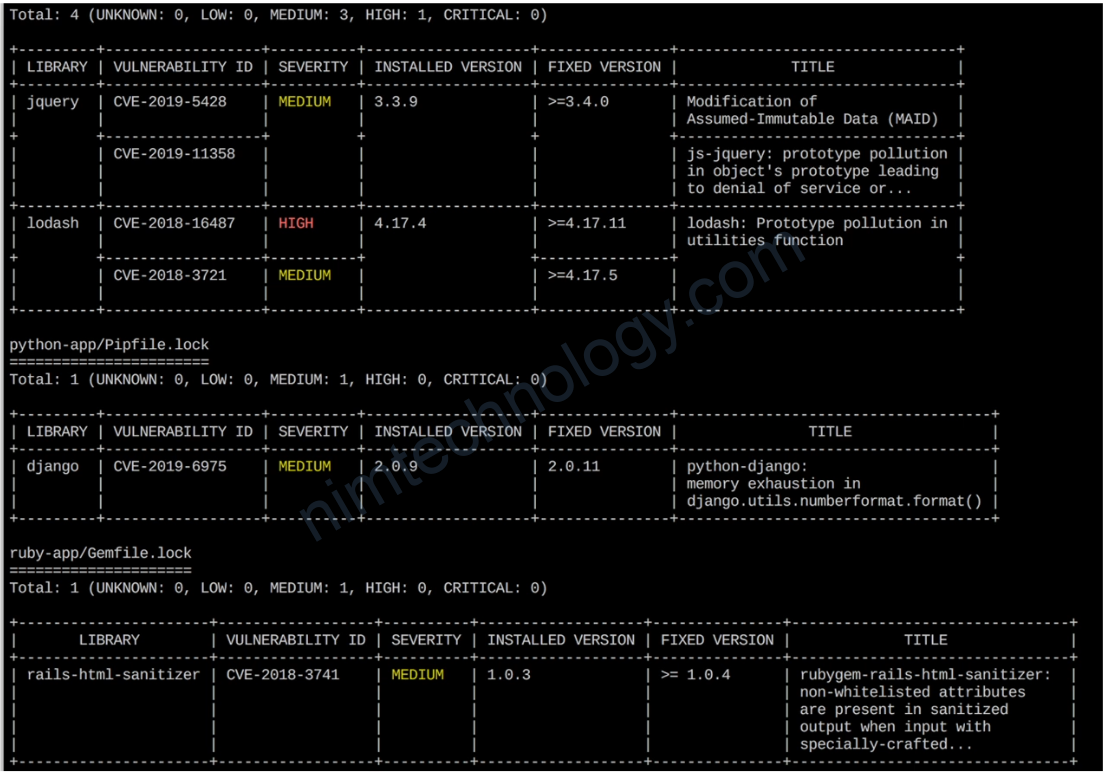
Sample Trivy Scan Table Report

2) Handons with Trivy
2.1) Trivy Image Scan – Docker
Ta sẽ run trivy via container và trivy sẽ đi scan public image python:3.4-alpine
docker run -v /var/run/docker.sock:/var/run/docker.sock -v $HOME/Library/Caches:/root/.cache/ aquasec/trivy:0.41.0 image python:3.4-alpine


Tiện mình cũng kiểm tra luôn là exit-code cho lần run này là bao nhiêu thì nó echo $? là 0
Và nếu run như này thì trên pipeline nó sẽ không bị dừng lại hay report là pipeline failed.
Nếu bạn chỉ cần report các severity is CRITICAL
docker run -v /var/run/docker.sock:/var/run/docker.sock -v $HOME/Library/Caches:/root/.cache/ aquasec/trivy:0.41.0 image python:3.4-alpine --exit-code 1 --severity CRITICALVà đây là report:
python:3.4-alpine (alpine 3.9.2)
================================
Total: 4 (CRITICAL: 4)
┌─────────────┬────────────────┬──────────┬───────────────────┬───────────────┬──────────────────────────────────────────────────────────┐
│ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title
│
├─────────────┼────────────────┼──────────┼───────────────────┼───────────────┼──────────────────────────────────────────────────────────┤
│ libbz2 │ CVE-2019-12900 │ CRITICAL │ 1.0.6-r6 │ 1.0.6-r7 │ bzip2: out-of-bounds write in function BZ2_decompress │
│ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2019-12900 │
├─────────────┼────────────────┤ ├───────────────────┼───────────────┼──────────────────────────────────────────────────────────┤
│ musl │ CVE-2019-14697 │ │ 1.1.20-r4 │ 1.1.20-r5 │ musl libc through 1.1.23 has an x87 floating-point stack │
│ │ │ │ │ │ adjustment im ......
│
│ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2019-14697 │
├─────────────┤ │ │ │ │
│
│ musl-utils │ │ │ │ │
│
│ │ │ │ │ │
│
│ │ │ │ │ │
├─────────────┼────────────────┤ ├───────────────────┼───────────────┼──────────────────────────────────────────────────────────┤
│ sqlite-libs │ CVE-2019-8457 │ │ 3.26.0-r3 │ 3.28.0-r0 │ sqlite: heap out-of-bound read in function rtreenode() │
│ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2019-8457 │
└─────────────┴────────────────┴──────────┴───────────────────┴───────────────┴──────────────────────────────────────────────────────────┘
root@LP11-D7891:~# echo $?
1
Bạn sẽ thấy chúng ta run exit-code được report là 1.
nếu bạn chạy pipeline thì khả năng cao là pipeline sẽ dùng lại.


--light: This flag enables the “light mode” for the vulnerability database. In light mode, Trivy downloads a smaller database with less detailed vulnerability information, which is faster and uses less disk space.
Bạn có thể bắt trước file .sh này để design scan cho project của bạn.


2.2) Scan application packages
Bạn cũng có thể scan application packages.

3) Using Trivy ignore.
Nếu có 1 số lỗi và bạn muốn Trivy ignore thì có thể sài cách sau:
Mình gặp lỗi sau:
/go/pkg/mod/github.com/aws/aws-sdk-go-v2/service/sts@v1.21.5/api_op_GetAccessKeyInfo.go (secrets) ================================================================================================= Total: 1 (CRITICAL: 1) CRITICAL: AWS (aws-access-key-id) ════════════════════════════════════════ AWS Access Key ID ──────────────────────────────────────── /go/pkg/mod/github.com/aws/aws-sdk-go-v2/service/sts@v1.21.5/api_op_GetAccessKeyInfo.go:19 (added by 'RUN /bin/sh -c go mod download # buildki') ──────────────────────────────────────── 17 18 // Returns the account identifier for the specified access key ID. Access keys 19 [ // consist of two parts: an access key ID (for example, ******************** ) and 20 // a secret access key (for example, wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY ).
Lỗi trên là lib của aws người ta có bỏ aws key example.
Và trivy bắt lỗi trên.
Sau khi nghiên cứu trivy action của github thì mình nhận ra rằng
đầu tiên bạn tạo 1 file bất kì trong.

Mình tạo 1 file request-trivy-ignore.txt

Bạn sử dụng trivyIgnores: ‘request-trivy-ignore.txt’
- name: Run Trivy vulnerability scanner (CRITICAL)
uses: aquasecurity/trivy-action@master
with:
image-ref: ${{ secrets.DOCKER_HUB_USERNAME }}/zeus-rotations:${{ env.RELEASE_VERSION }}
format: 'table'
exit-code: '1'
severity: 'CRITICAL'
trivyIgnores: 'request-trivy-ignore.txt'
#https://github.com/aquasecurity/trivy/issues/4826
#skip-files: '/go/pkg/mod/github.com/aws/aws-sdk-go-v2/service/sts@v1.21.4/api_op_GetAccessKeyInfo.go'
#skip-dirs: '/go/pkg/mod/github.com/aws/aws-sdk-go-v2/service'