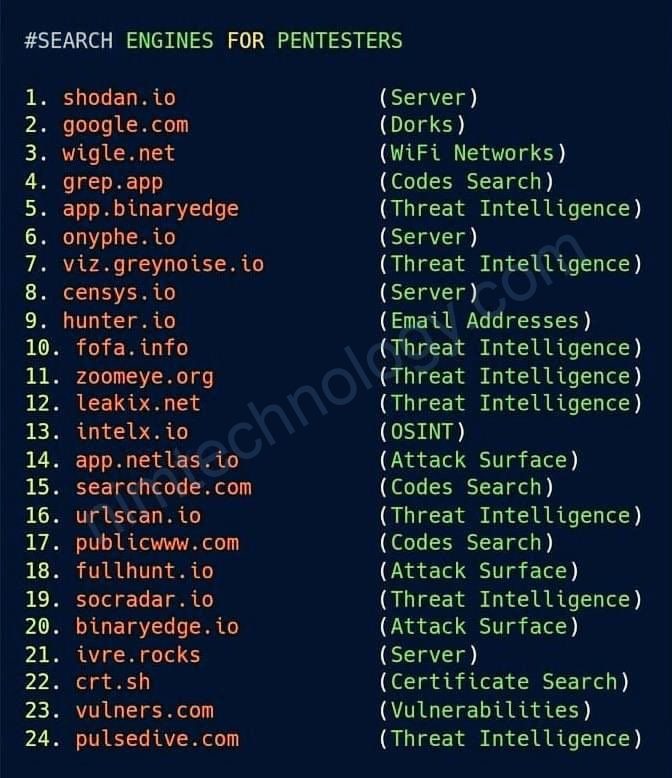
Dynamic Application Security Testing
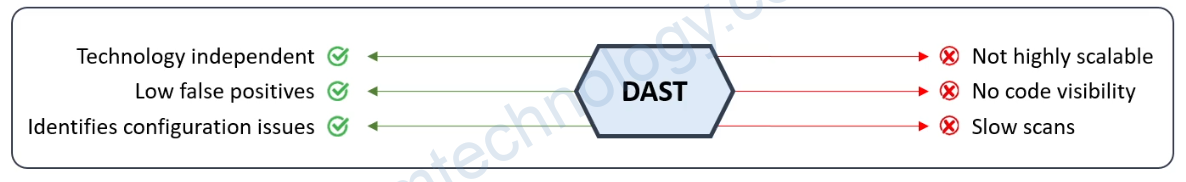
DAST looks for security vulnerabilities by simulating external attacks on an application while the application is running.
DAST test is performed in a dynamic environment.
SAST scans an application’s code line by line when the application is at rest. (SonarQube)
DAST has no access to an application’s source code, it detects security vulnerabilities by attacking the application externally.
DAST can be used in production, testing usually is carried out in a QA environment.
DAST is extremely good at finding externally visible issues and vulnerabilities. This includes a number of security risks from OWASP’s top ten, such as
– cross-site scripting, ·
– injection errors like SQL injection or command injection,
– path traversal, and ·
– insecure server configuration
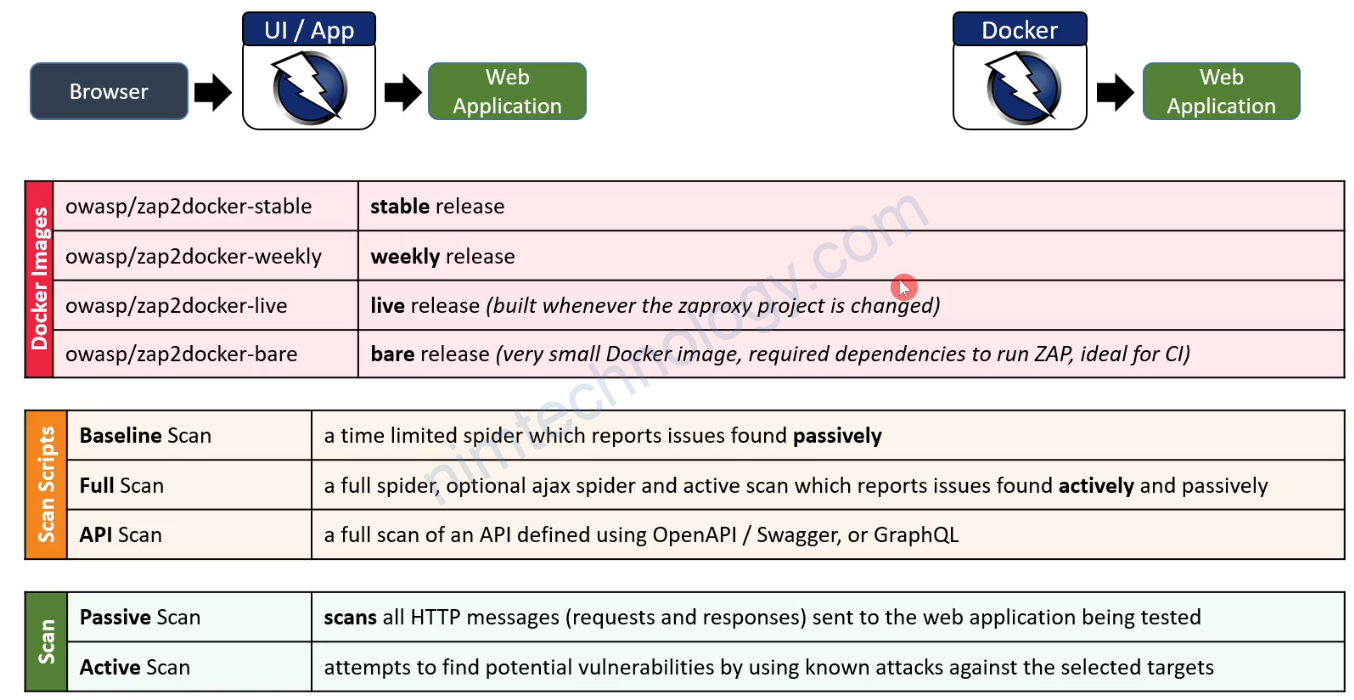
OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner.
ZAP is designed specifically for testing web applications. ZAP is what is known as a “man-in-the-middle proxy.
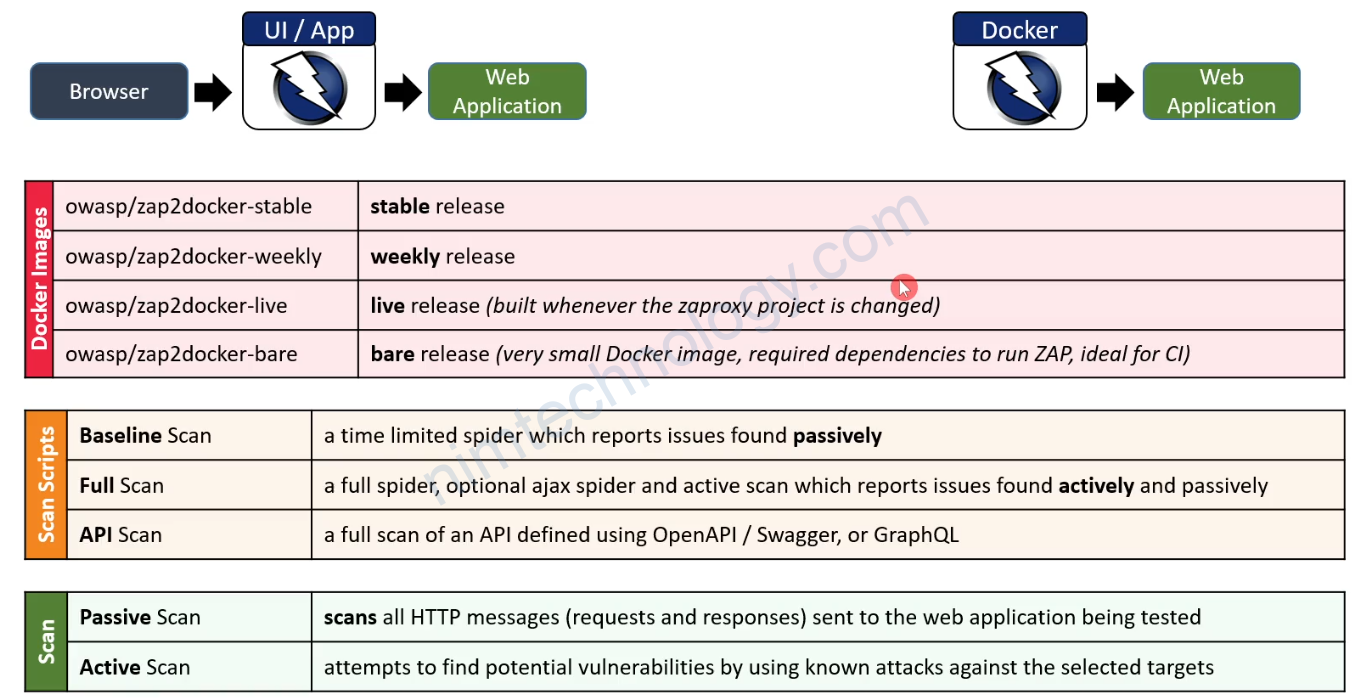
ZAP API Scan
It is tuned for performing scans against APIs defined by OpenAPI, SOAP, or GraphQL via either a local file or a URL.
It imports the definition that you specify and then runs an Active Scan against the URLs found.
The Active Scan is tuned to APIs, so it doesn’t bother looking for things like XSSS (Cross Site Scripting).
It also includes 2 scripts that:
– Raise alerts for any HTTP Server Error response codes.
– Raise alerts for any URLs that return content types that are not usually associated with APIs
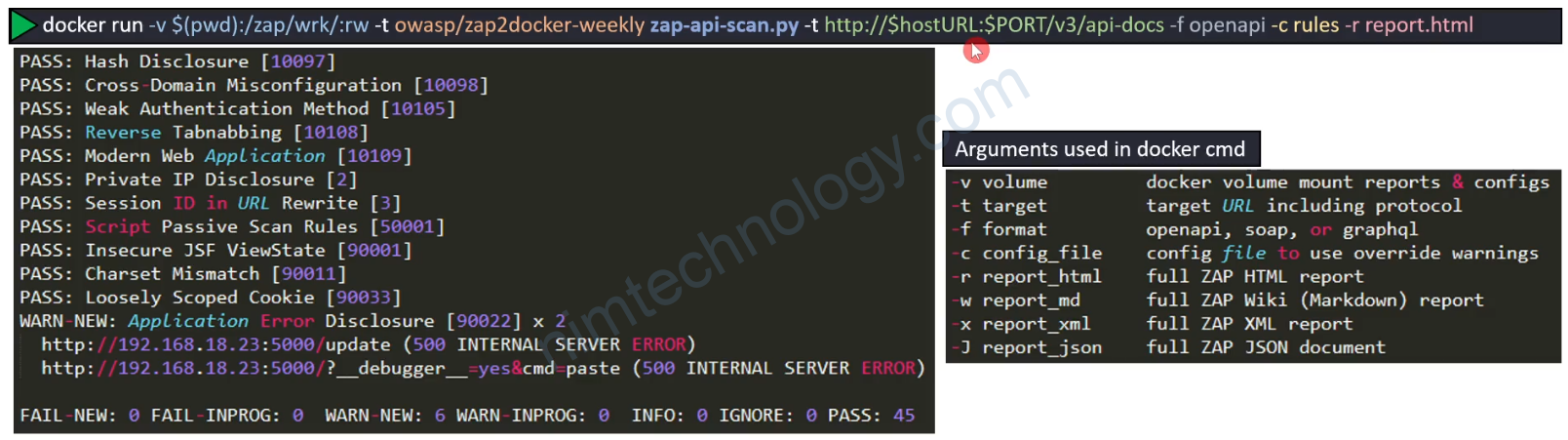
Anh em can test
chmod 777 $(pwd)/owasp
sudo docker run -t -v $(pwd)/owasp/:/zap/wrk/:rw -u zap owasp/zap2docker-weekly zap-baseline.py -t https://tiki.vn -g gen.conf -r tiki_report.html
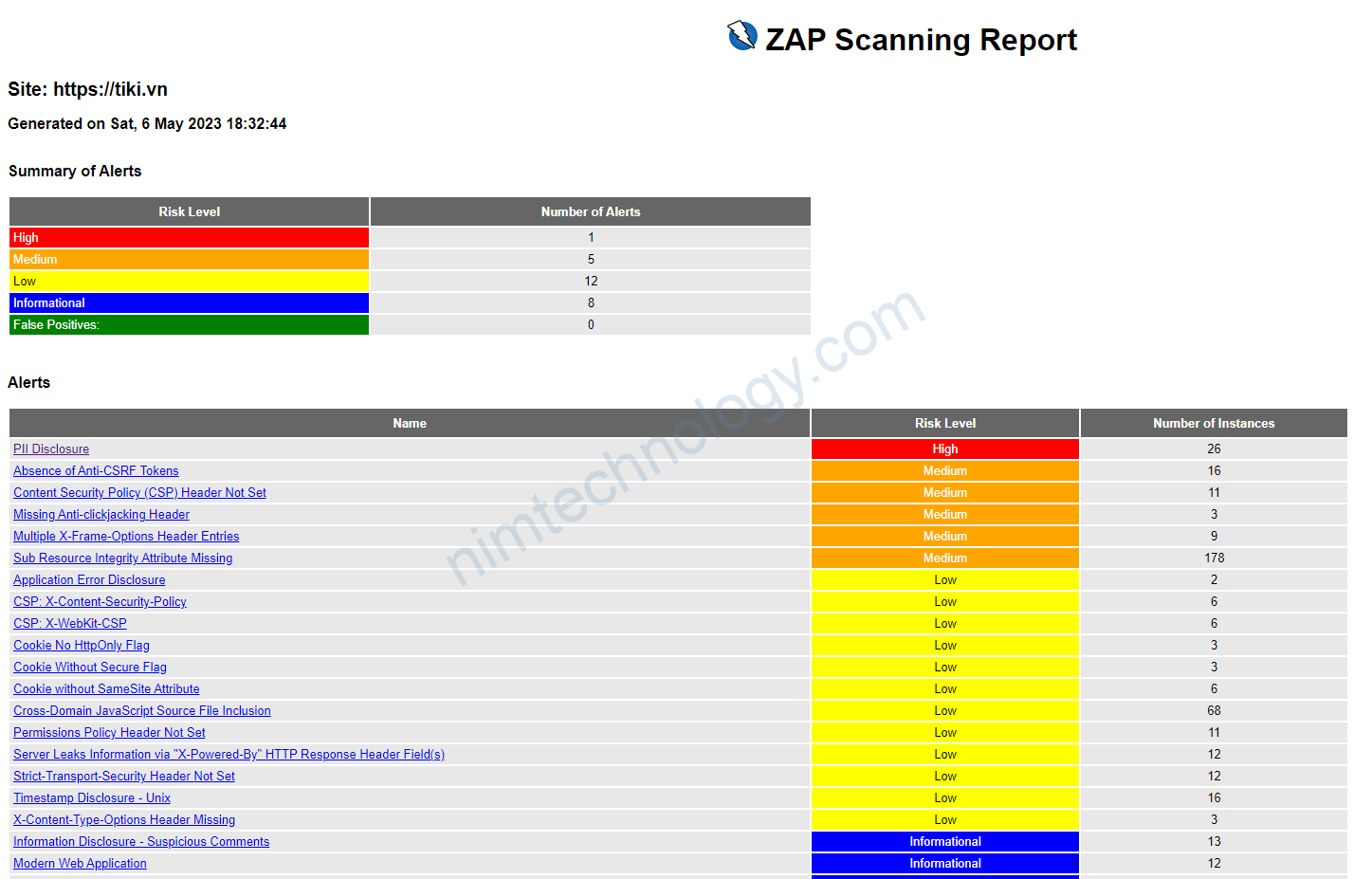
zap-baseline.py is a script provided by the OWASP ZAP project to run a baseline scan on a target web application. A baseline scan is a quick and simple scan that checks for common security vulnerabilities without performing any actual attacks. The purpose of the baseline scan is to provide a general overview of a web application’s security posture, rather than a comprehensive assessment.
Regarding other files, the OWASP ZAP project offers multiple scripts and tools to help you perform different types of scans and generate reports. Some of these include:
zap-full-scan.py: A script for running a more comprehensive, full scan on a web application. This script takes longer to run and may be more intrusive than a baseline scan.zap-api-scan.py: A script for scanning web APIs for security vulnerabilities.zap_common.py: A common library used by other ZAP Python scripts.
You can find these scripts, along with additional documentation, in the OWASP ZAP GitHub repository. The repository also contains a variety of other resources, such as plugins, extensions, and sample configurations, to help you customize and enhance your ZAP experience.
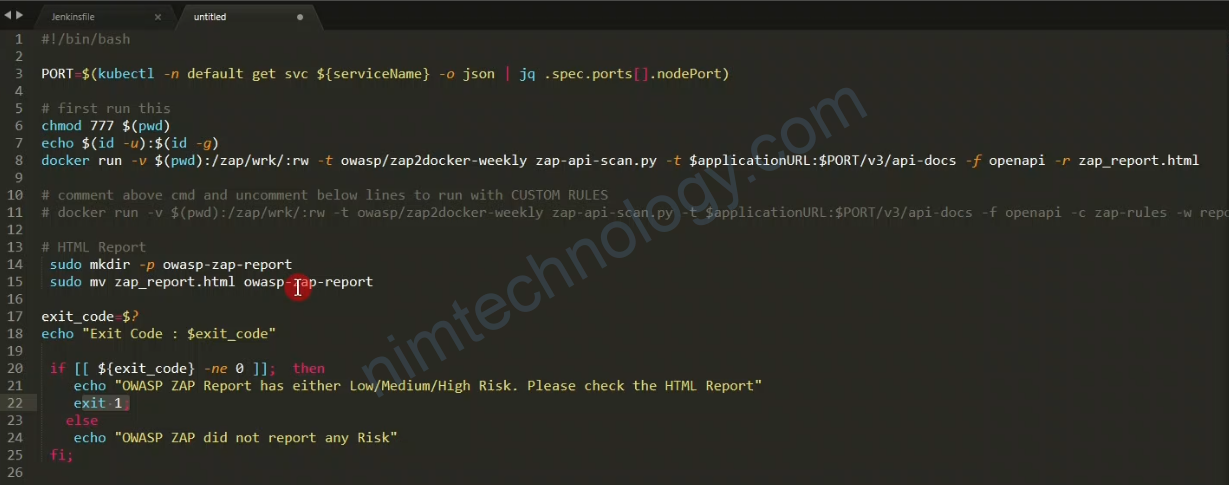
ZAP – Ignore Content-type Warning.
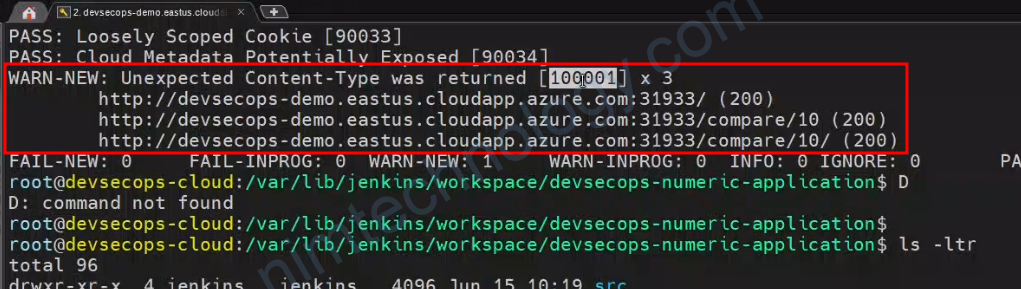
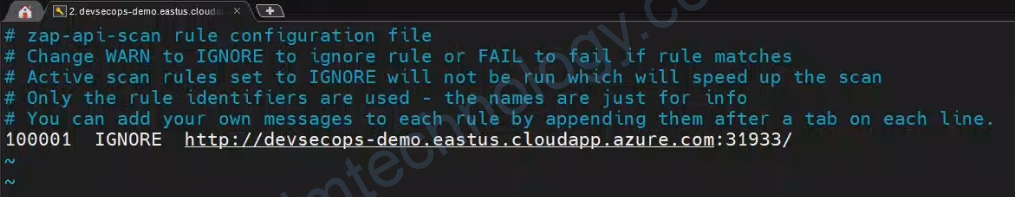
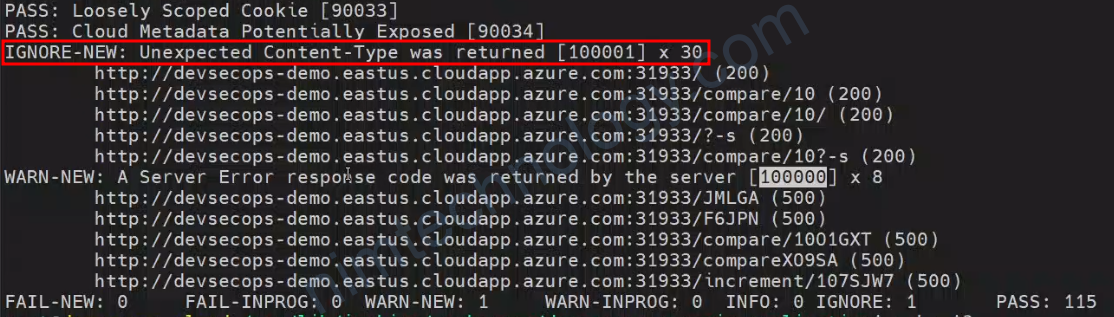
Lần đâu tiên bạn chạy
sudo docker run -t -v $(pwd)/owasp/:/zap/wrk/:rw -u zap owasp/zap2docker-weekly zap-baseline.py -t https://hao-fe-to-do-app.devops-training.nimtechnology.com/ -g gen.conf -r devops-training.html
sẽ bị báo lỗi như sau:
WARN-NEW: Missing Anti-clickjacking Header [10020] x 1
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
WARN-NEW: X-Content-Type-Options Header Missing [10021] x 8
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/robots.txt (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/static/css/main.5f361e03.chunk.css (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/manifest.json (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/logo192.png (200 OK)
WARN-NEW: Strict-Transport-Security Header Not Set [10035] x 9
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/sitemap.xml (404 Not Found)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/robots.txt (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/static/css/main.5f361e03.chunk.css (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/manifest.json (200 OK)
WARN-NEW: Server Leaks Version Information via "Server" HTTP Response Header Field [10036] x 9
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/sitemap.xml (404 Not Found)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/static/css/main.5f361e03.chunk.css (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/robots.txt (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/manifest.json (200 OK)
WARN-NEW: Content Security Policy (CSP) Header Not Set [10038] x 1
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
WARN-NEW: Permissions Policy Header Not Set [10063] x 3
https://hao-fe-to-do-app.devops-training.nimtechnology.com/ (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/static/js/main.5cd4fcef.chunk.js (200 OK)
https://hao-fe-to-do-app.devops-training.nimtechnology.com/static/js/2.2bb5c0f4.chunk.js (200 OK)
tiếp theo là bạn muốn ignore các warning trên:
Bước 1 bạn để ý nó generate 1 tên là: gen.conf
Bước 2 bạn copy file đó thành file ignore.conf
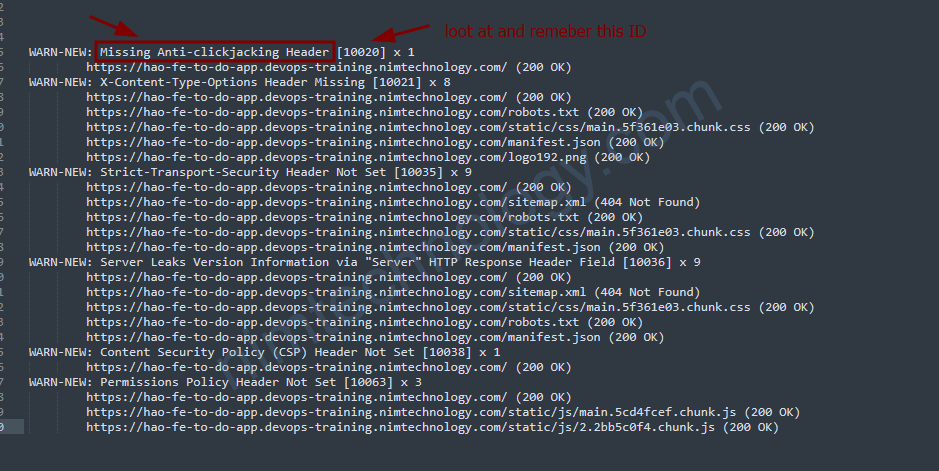
bạn muốn ignore Missing Anti-clickjacking Header có ID là: [10020]
Bạn Vi ignore.conf và tìm đến line có ID là 10020, sau đó chuyển chữ WARN sang IGNORE
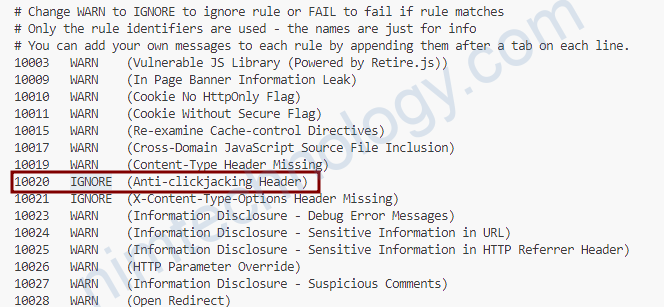
rồi chạy lệnh:
sudo docker run -t -v $(pwd)/owasp/:/zap/wrk/:rw -u zap owasp/zap2docker-weekly zap-baseline.py -t https://hao-fe-to-do-app.devops-training.nim.com/ -g gen.conf -c ignore.conf -r devops-training.htmlNGoài ra bạn còn 1 sự lựa chọn nữa là Arachni (Dynamic Analysis)