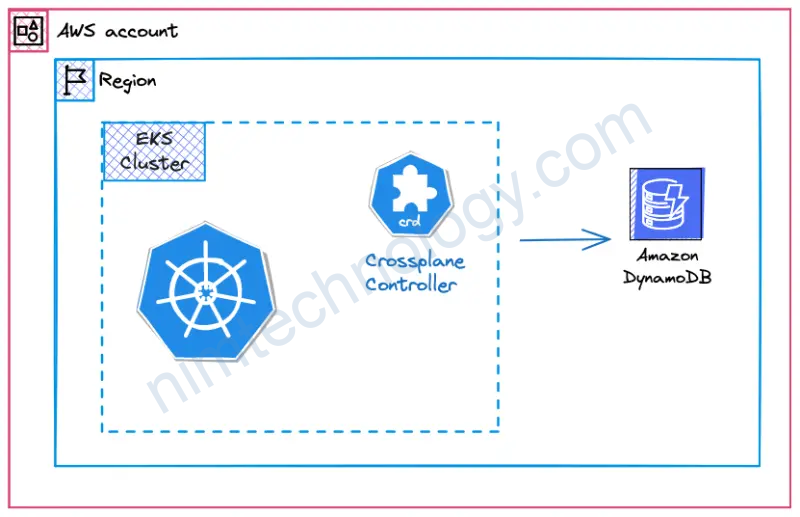
Creator: https://github.com/trungvo11
Crossplane is an open-source project in the Cloud Native Computing Foundation (CNCF) that transforms your Kubernetes cluster into a universal control plane. It enables platform teams to assemble infrastructure from multiple vendors and expose higher-level self-service APIs for application teams to consume, without writing any code.
Crossplane extends your Kubernetes cluster to support orchestrating any infrastructure or managed service. It allows you to compose Crossplane’s granular resources into higher-level abstractions that can be versioned, managed, deployed, and consumed using your favorite tools and existing processes.
Crossplane Docs · master · Install Crossplane
upbound/provider-family-aws@v1.20.1 | Upbound Marketplace
GitHub – crossplane-contrib/provider-upjet-aws: AWS Provider for Crossplane.
crossplane/cluster/charts/crossplane at main · crossplane/crossplane
provider-aws/examples/ec2 at master · crossplane-contrib/provider-aws
Steps
- Provision the EKS Cluster
- Install Crossplane Using Helm
Add the Crossplane Helm repository and install Crossplane.
helm repo add crossplane-stable https://charts.crossplane.io/stable
helm repo update
helm install crossplane crossplane-stable/crossplane --namespace crossplane-system --create-namespace
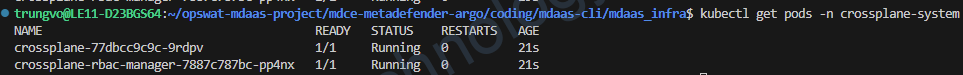
3. Verify Crossplane Installation
kubectl get pods -n crossplane-system
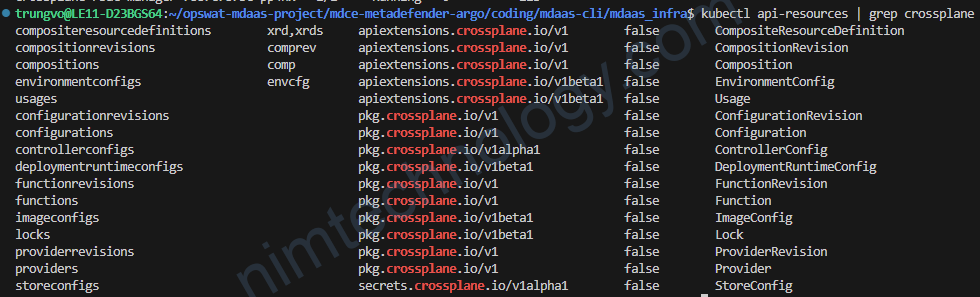
kubectl api-resources | grep crossplane
4. Install AWS Provider for Crossplane
https://marketplace.upbound.io/providers/upbound/provider-family-aws/v1.20.1
apiVersion: pkg.crossplane.io/v1
kind: Provider
metadata:
name: provider-aws-docdb
spec:
package: xpkg.upbound.io/upbound/provider-aws-docdb:v1
---
apiVersion: pkg.crossplane.io/v1
kind: Provider
metadata:
name: provider-aws-ec2
spec:
package: xpkg.upbound.io/upbound/provider-aws-ec2:v1
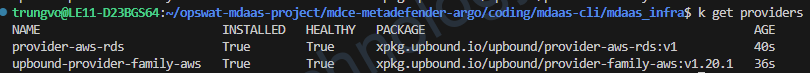
5. Verify Provider Installation
kubectl get providers
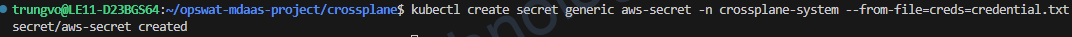
6. Create a Kubernetes secret for AWS
credentials.txt
aws_access_key_id = YOUR_ACCESS_KEY_ID
aws_secret_access_key = YOUR_SECRET_ACCESS_KEY
kubectl create secret generic aws-secret -n crossplane-system --from-file=creds=credential.txt
7. Create a ProviderConfig
apiVersion: aws.upbound.io/v1beta1
kind: ProviderConfig
metadata:
name: default
spec:
credentials:
source: Secret
secretRef:
namespace: crossplane-system
name: aws-secret
key: creds

8. Create a managed resource in AWS
# Security Group
apiVersion: ec2.aws.upbound.io/v1beta1
kind: SecurityGroup
metadata:
name: documentdb-security-group
spec:
forProvider:
region: ap-southeast-1
vpcId: vpc-076d9083e381d0fb7
description: Enable documentdb access
providerConfigRef:
name: default
---
# Ingress Rule
apiVersion: ec2.aws.upbound.io/v1beta1
kind: SecurityGroupRule
metadata:
name: documentdb-ingress
spec:
forProvider:
region: ap-southeast-1
type: ingress
fromPort: 27017
toPort: 27017
protocol: "tcp"
cidrBlocks:
- "10.0.0.0/8"
securityGroupIdRef:
name: documentdb-security-group
providerConfigRef:
name: default
---
# Egress Rule
apiVersion: ec2.aws.upbound.io/v1beta1
kind: SecurityGroupRule
metadata:
name: documentdb-egress
spec:
forProvider:
region: ap-southeast-1
type: egress
fromPort: -1
toPort: -1
protocol: "-1"
cidrBlocks:
- "0.0.0.0/0"
securityGroupIdRef:
name: documentdb-security-group
providerConfigRef:
name: default
9. Get buckets created using Crossplane
kubectl get SecurityGroup
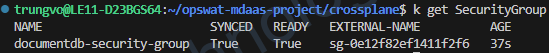
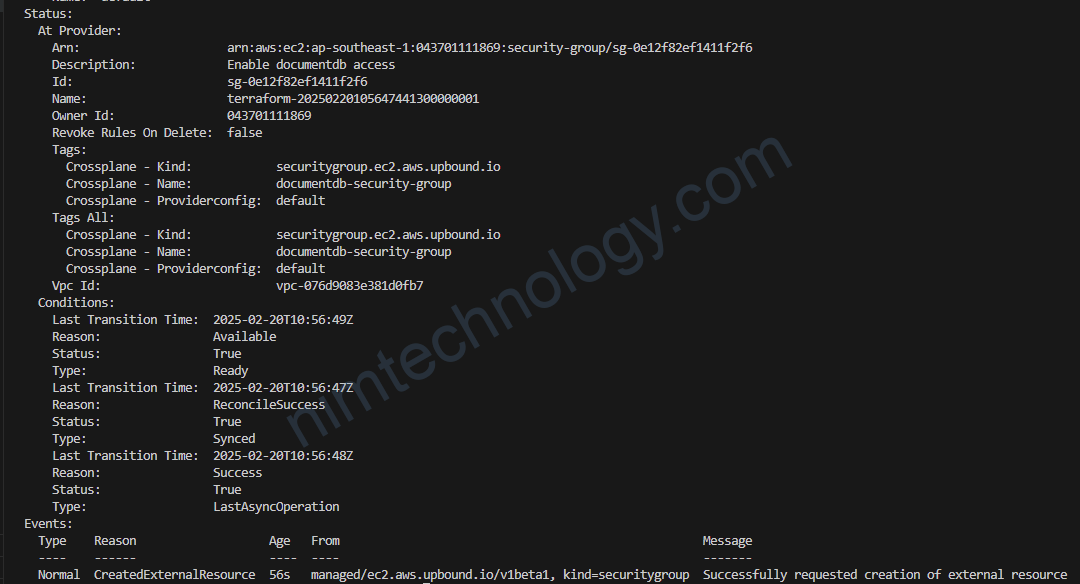
kubectl describe SecurityGroup
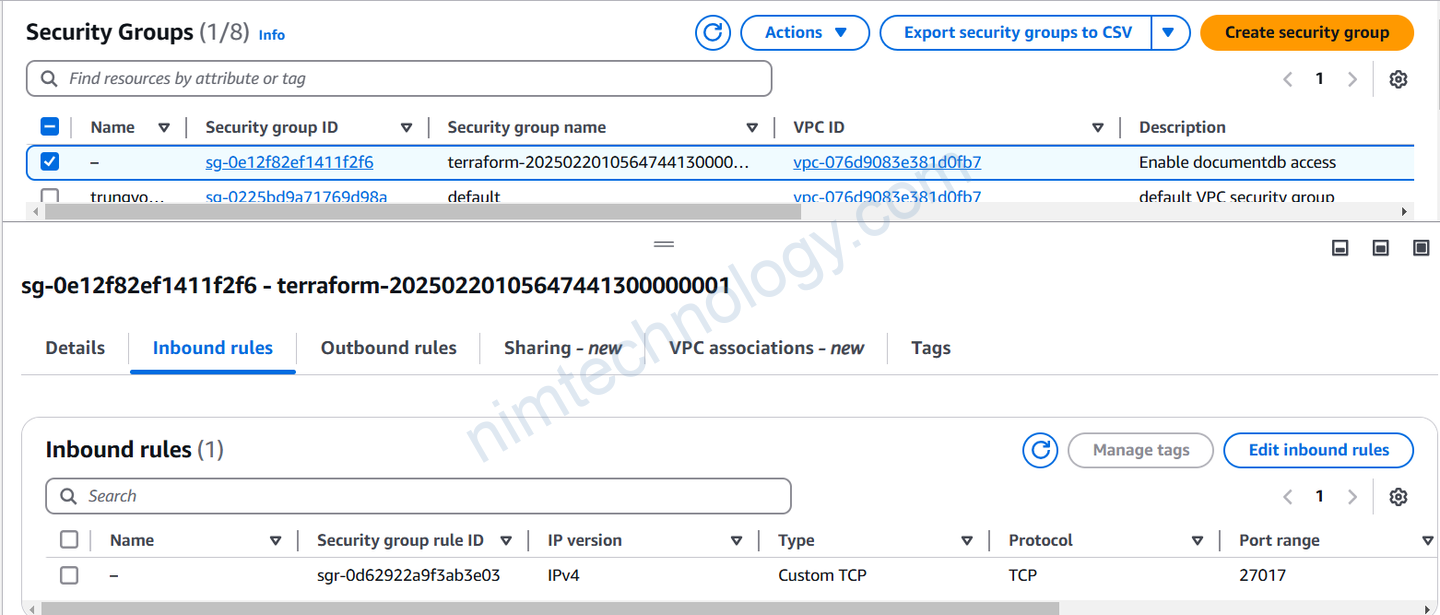
10. Delete managed resource from AWS
kubectl delete ...