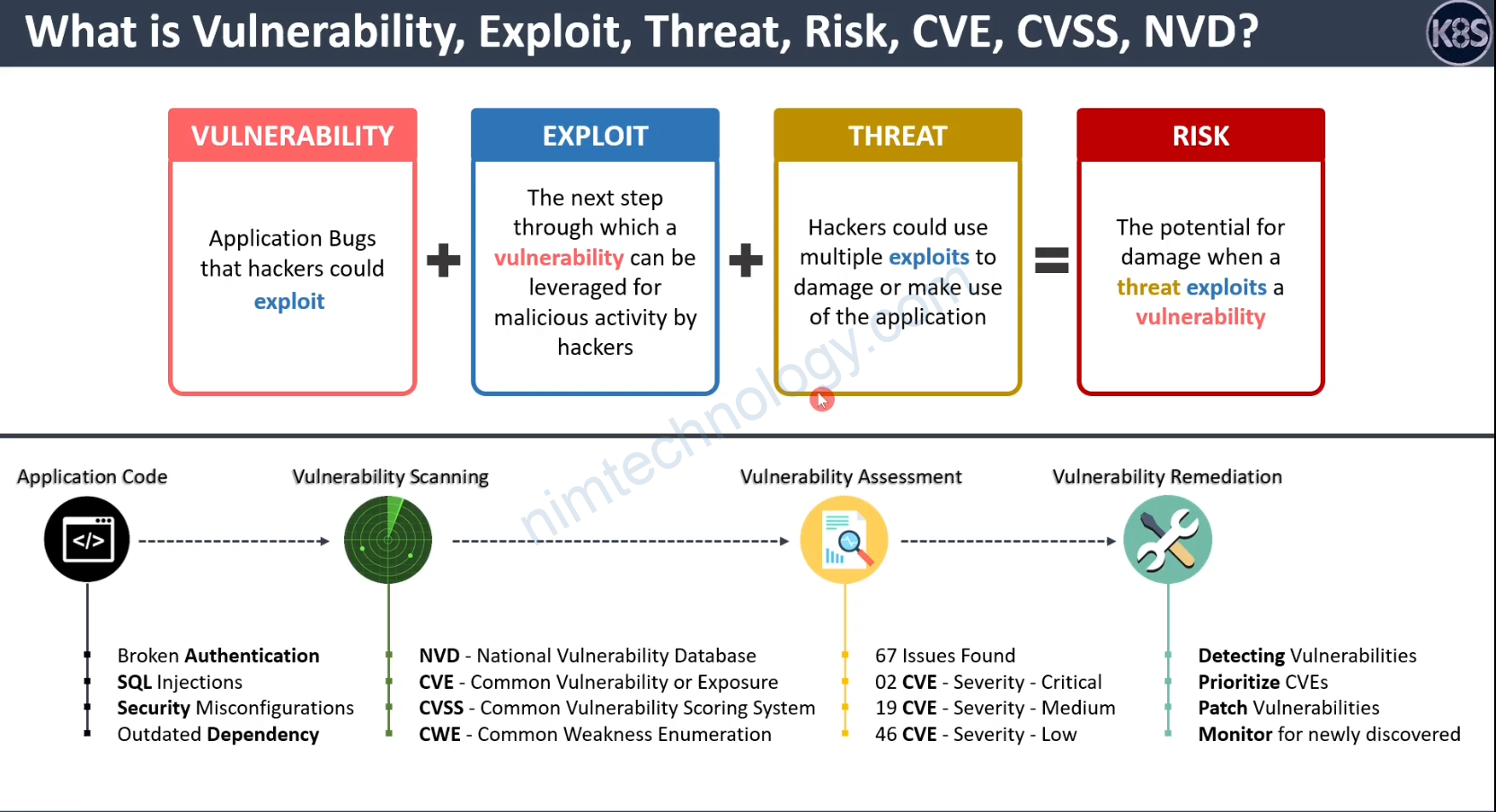
NVD: National Vulnerability Database
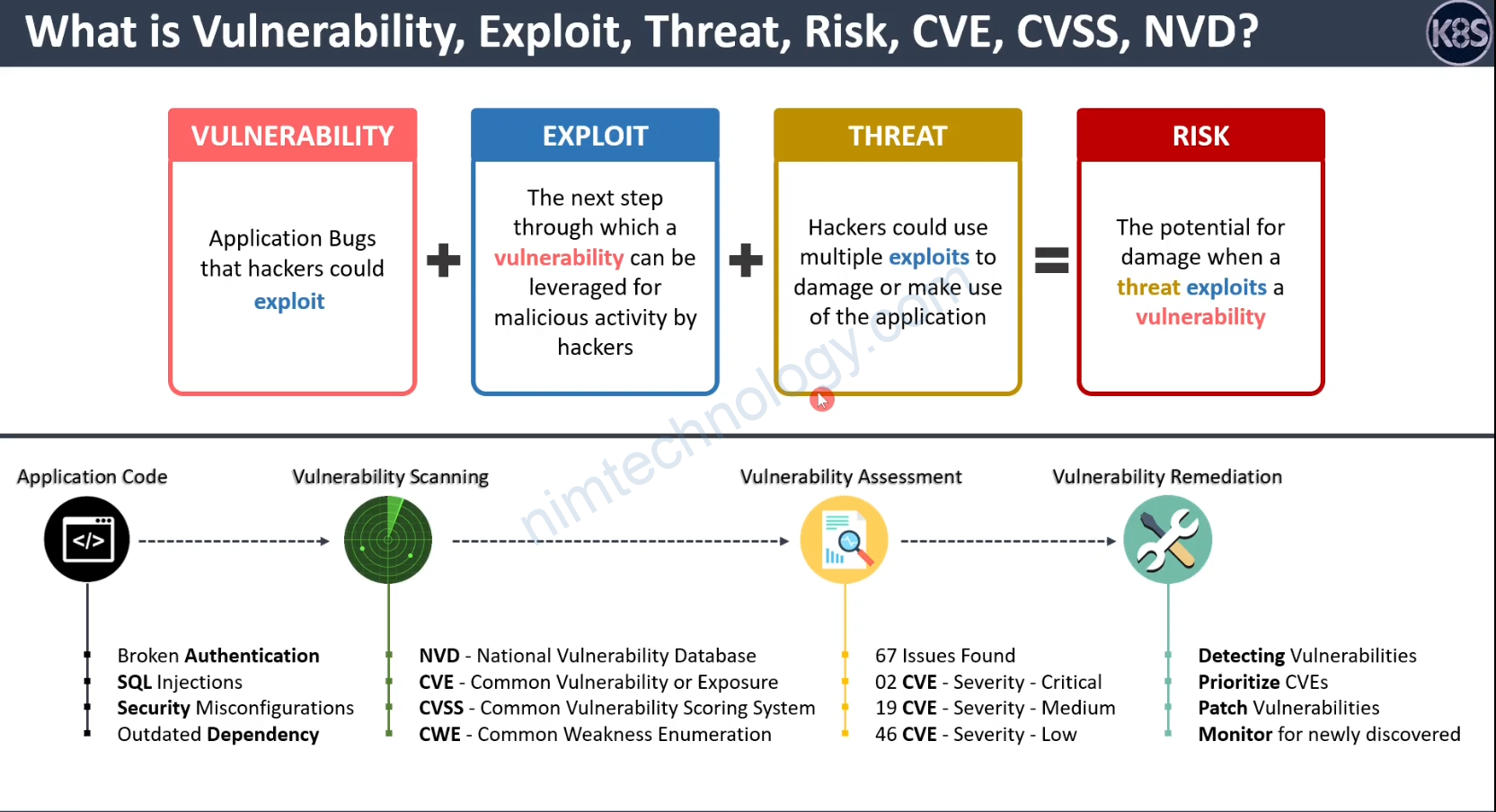
Imagine NVD as the ultimate library of computer vulnerabilities. It’s like Wikipedia, but for all the bad stuff that can happen to your computer. If a hacker finds a way to mess with a system, the NVD is where you’ll find all the deets.
CVE: Common Vulnerabilities and Exposures
CVE is like the Dewey Decimal System for that library. Each vulnerability gets a unique CVE number so that everyone can find, discuss, and fix it without confusion. It’s like the ID badge for a vulnerability.
CVSS: Common Vulnerability Scoring System
CVSS is the rating system. It tells you how bad a vulnerability is, on a scale from 0 to 10. Think of it like the spiciness level on a hot sauce bottle. The higher the number, the more you should be sweating!
CWE: Common Weakness Enumeration
CWE is like the genre section in the library. It categorizes the type of weakness that led to the vulnerability. Was it a romance gone wrong, a comedy of errors, or a full-on horror show? CWE tells you!
NVD: National Vulnerability Database
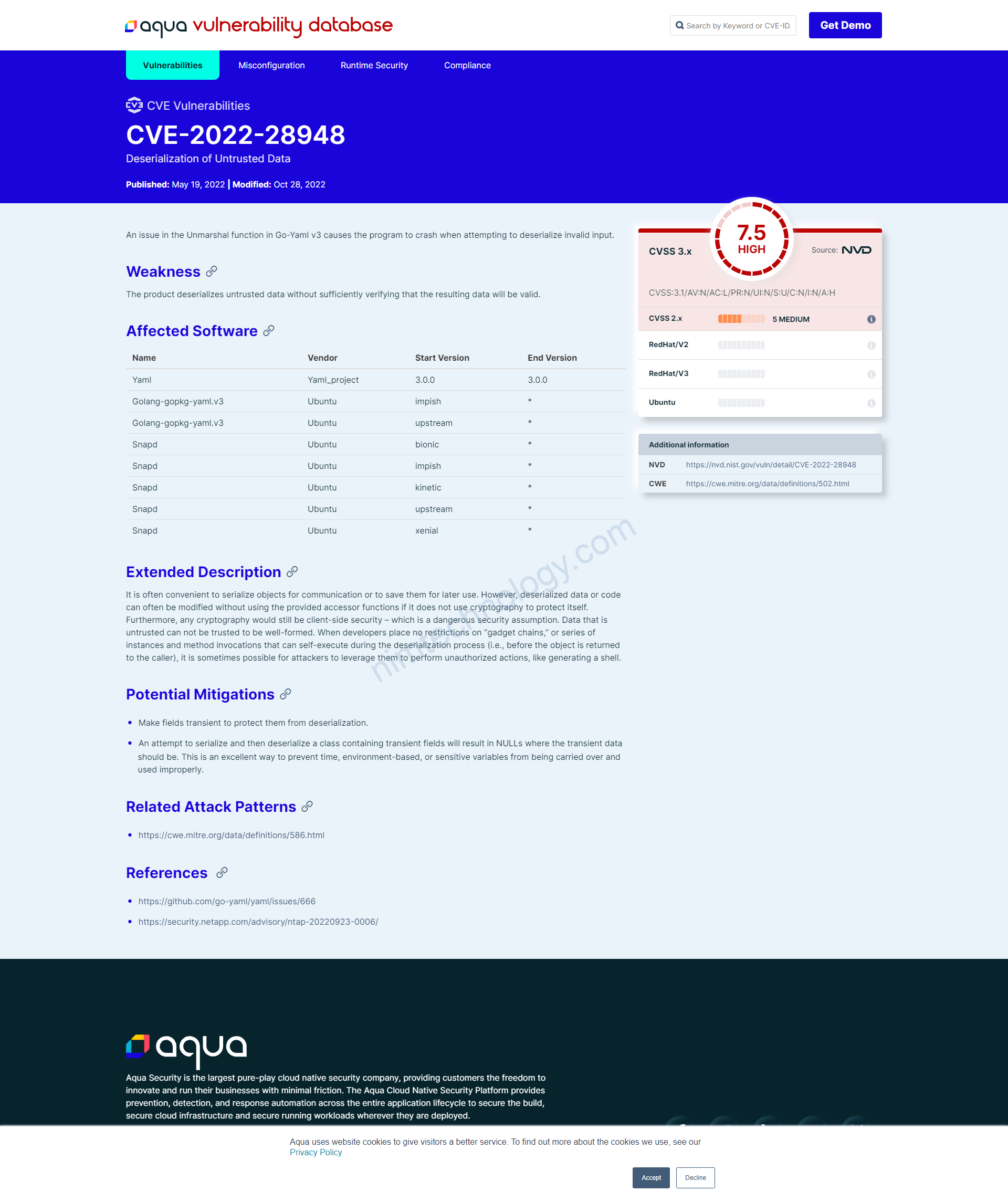
Example: You’re a developer using Go-Yaml v3 for your project. You hear about a new vulnerability and decide to check the NVD. You find CVE-2022-28948 listed there, alerting you to an issue in the Unmarshal function that can crash your program.
CVE: Common Vulnerabilities and Exposures
Example: You find that the Chrome vulnerability has a CVE identifier like “CVE-2021-12345.” This unique code helps you track discussions and fixes related to this specific issue.
CVSS: Common Vulnerability Scoring System
Example: Let’s assume this vulnerability has a CVSS score of 7.5 (hypothetical, as I can’t browse the web for real-time data). This indicates that the issue is quite severe and should be addressed promptly.
CWE: Common Weakness Enumeration
Example: The vulnerability is due to an issue in the Unmarshal function. While the specific CWE category isn’t provided in the brief description, it’s likely related to data deserialization issues.
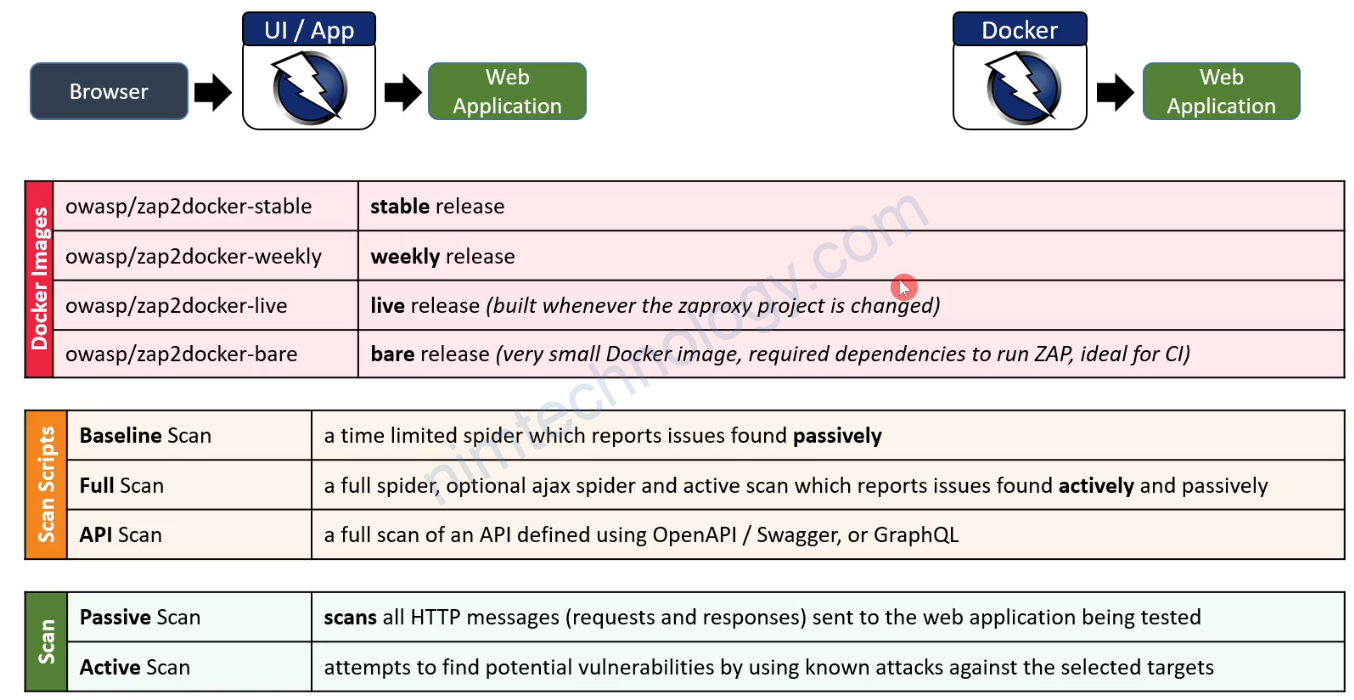
Dependency Check Basics
Dependency-Check primarily focused on Java and .NET applications.
What?
Dependency-check is an open source project created by OWASP
It is a software composition analysis tool that identifies project dependencies on open-source code and checks if there are known vulnerabilities associated with that code.
Problem?
Our products include open-source dependencies, many of which have known vulnerabilities.
In order to ensure that you are releasing secure products, you must have a solution in place that evaluates these dependencies and provides actionable information on fixes.
Solution?
Dependency-Check gathers the information from the pom.xml and packages.
The evidence gathered is used to identify the Common Platform Enumeration (CPE) of the dependency.
CPE is a standardized name given to software versions for universal identification.
Once the CPE is identified, it is stored in an index and compared to a list of Common Vulnerability and Exposure (CVE) entries.
Dependency-Check uses the list of CVE entries present in the National Vulnerability Database(NVD).
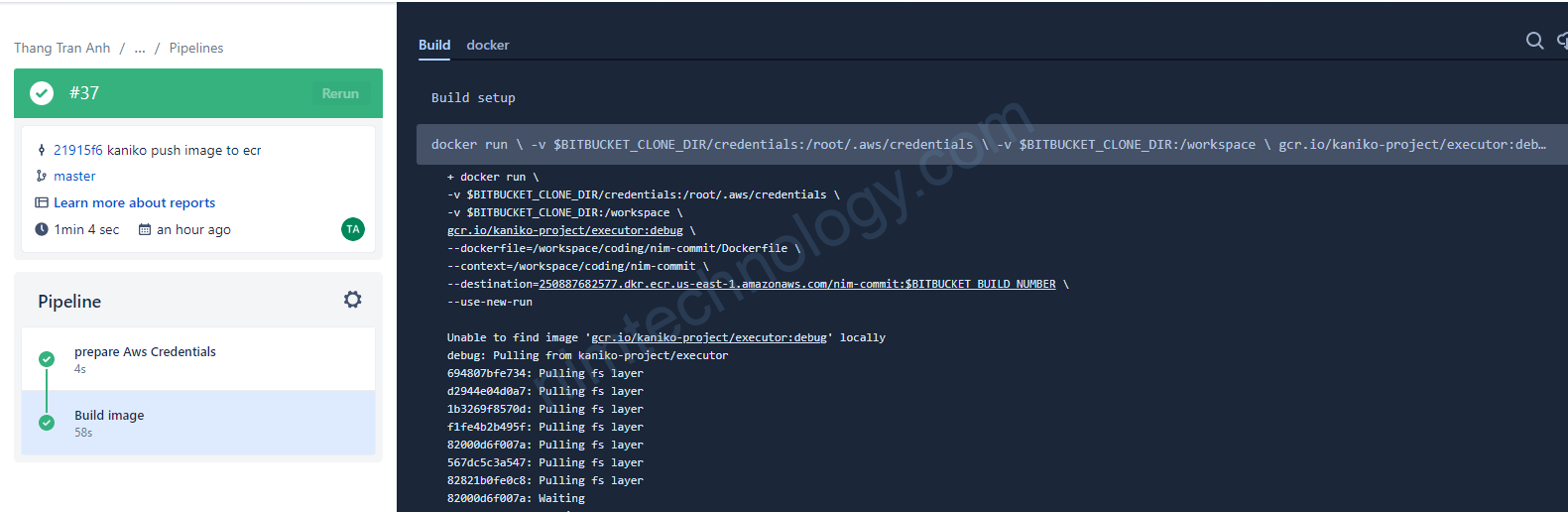
Use Dependency-check on Jenkins
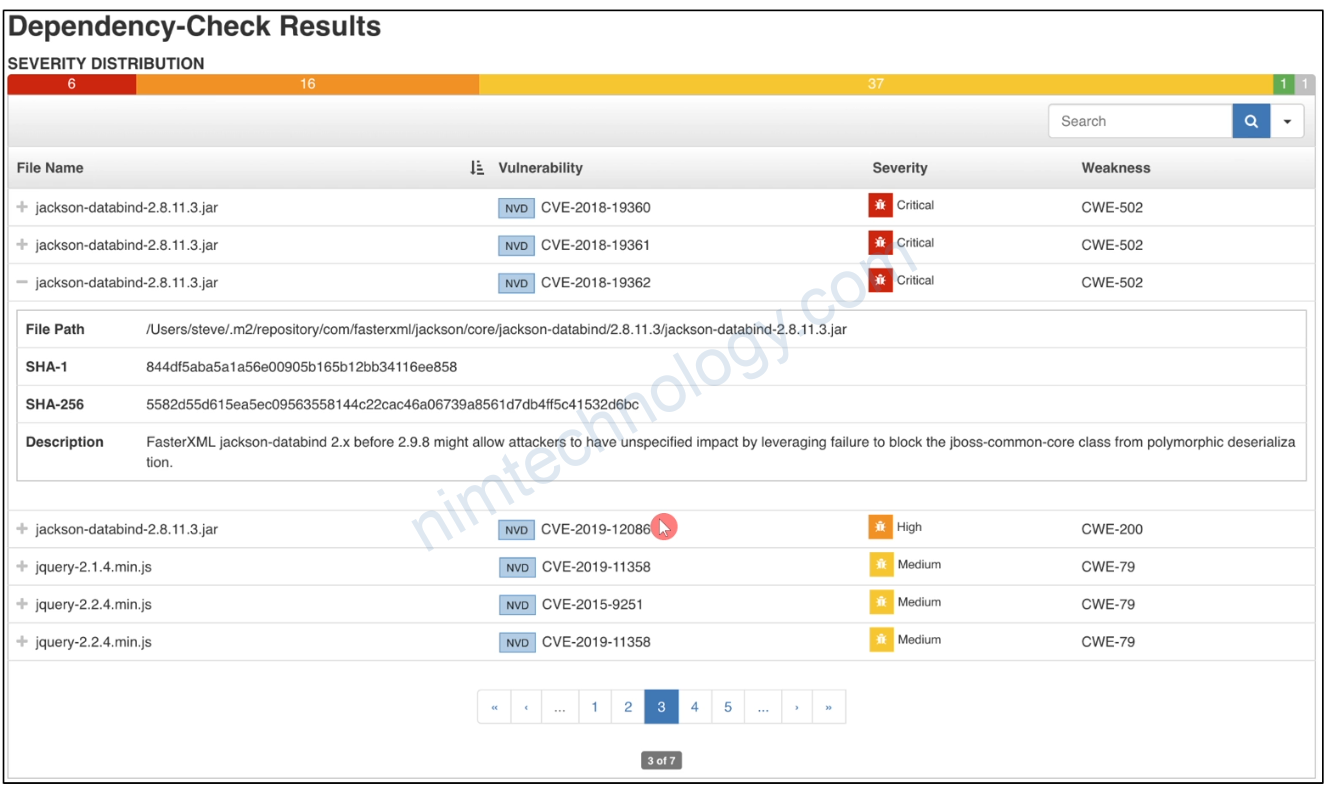
Install Dependency-Check on linux.
https://www.youtube.com/watch?v=DF22sTpcE6w
https://www.youtube.com/watch?v=X47ZkdYnGZI
Install Dependency-Check docker.
docker run --rm -v $(pwd):/src -w /src owasp/dependency-check:latest --scan . --format "ALL" --project "YourProjectName" --out /reporthttps://github.com/dependency-check/DependencyCheck_Builder
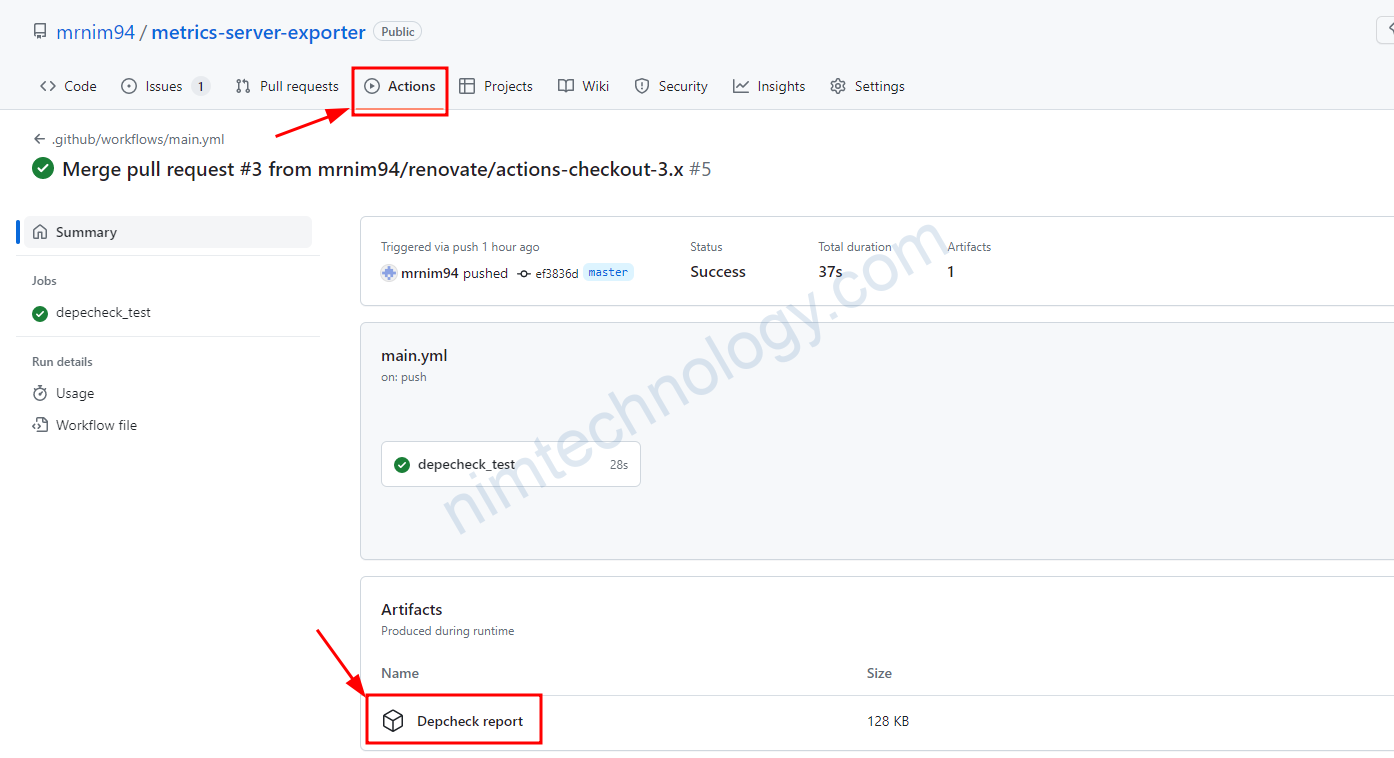
Github Action:
on: [push]
jobs:
depchecktest:
runs-on: ubuntu-latest
name: depecheck_test
steps:
- name: Checkout
uses: actions/checkout@v3
- name: Depcheck
uses: dependency-check/Dependency-Check_Action@main
id: Depcheck
with:
project: 'test'
path: '.'
format: 'HTML'
out: 'reports' # this is the default, no need to specify unless you wish to override it
args: >
--failOnCVSS 7
--enableRetired
- name: Upload Test results
uses: actions/upload-artifact@master
with:
name: Depcheck report
path: ${{github.workspace}}/reports
--failOnCVSS 7: Đối số này chỉ định mức độ CVSS (Common Vulnerability Scoring System) tối thiểu để công việc bị coi là thất bại. CVSS là một hệ thống chấm điểm tiêu chuẩn dùng để đánh giá mức độ nghiêm trọng của các lỗ hổng bảo mật. Điểm số CVSS nằm trong khoảng từ 0 đến 10, với 10 là mức độ nghiêm trọng nhất. Khi sử dụng--failOnCVSS 7, nếu có bất kỳ mối đe dọa nào có điểm CVSS lớn hơn hoặc bằng 7, công việc sẽ bị coi là thất bại và quá trình kiểm tra sẽ dừng lại.
https://jeremylong.github.io/DependencyCheck/dependency-check-cli/arguments.html--enableRetired: Đối số này khi được sử dụng sẽ cho phép Dependency-Check kiểm tra và báo cáo các lỗ hổng bảo mật đã được đánh dấu là “retired” (đã ngừng hoạt động). Điều này giúp đảm bảo rằng mã nguồn không chứa các lỗ hổng bảo mật cũ, ngay cả khi chúng không còn được coi là mối đe dọa hiện tại.Upload Test results: Sử dụng actionactions/upload-artifact@masterđể tải lên báo cáo kết quả kiểm tra vào phần “Artifacts” của GitHub Actions, với tênDepcheck reportvà đường dẫn là${{github.workspace}}/reports.