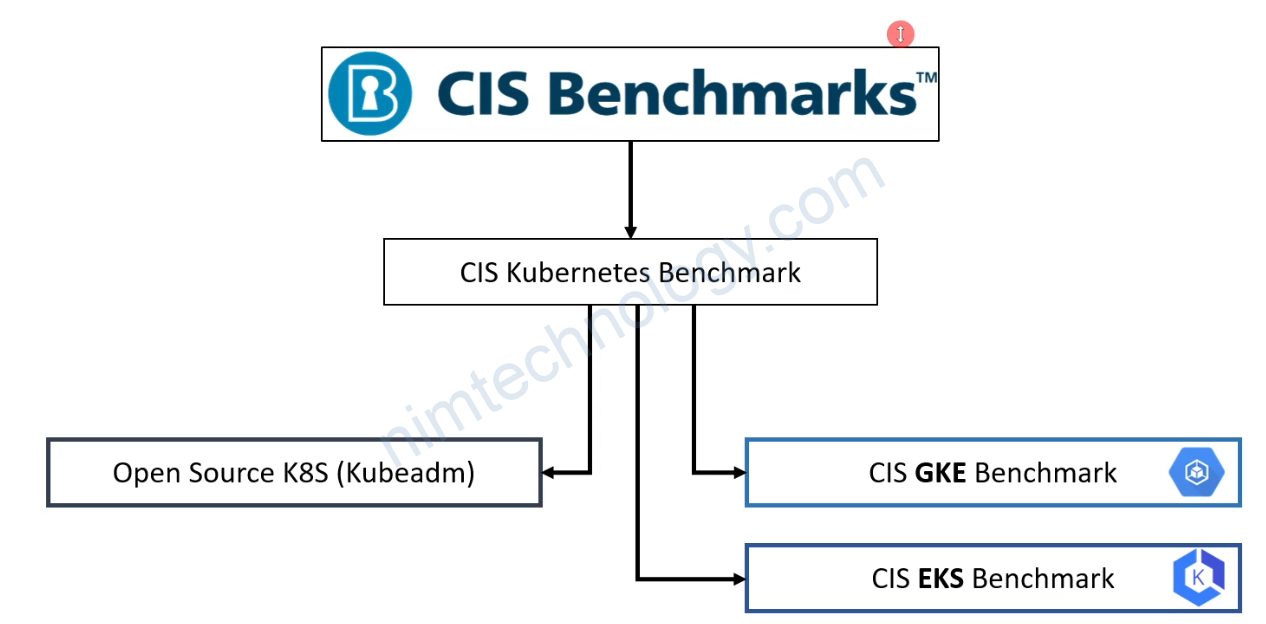
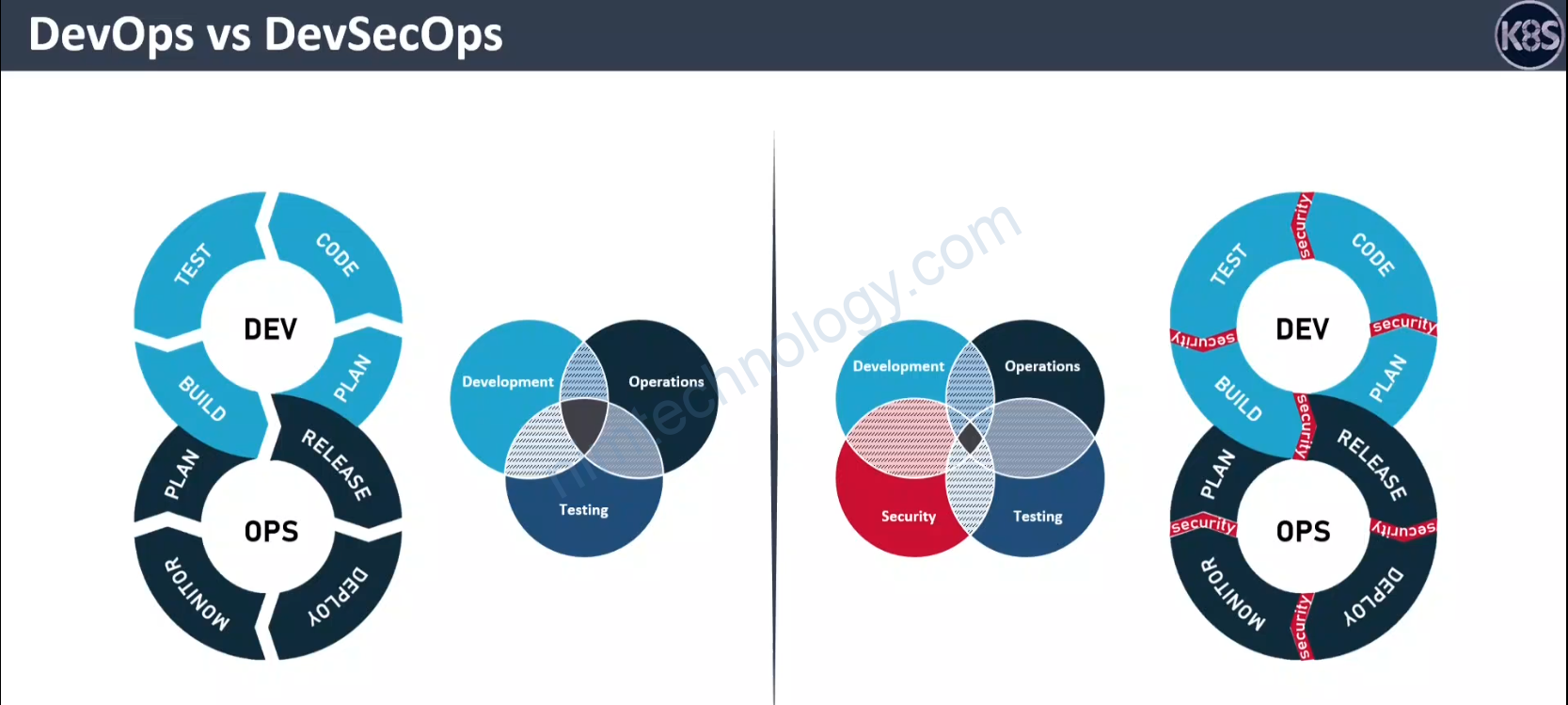
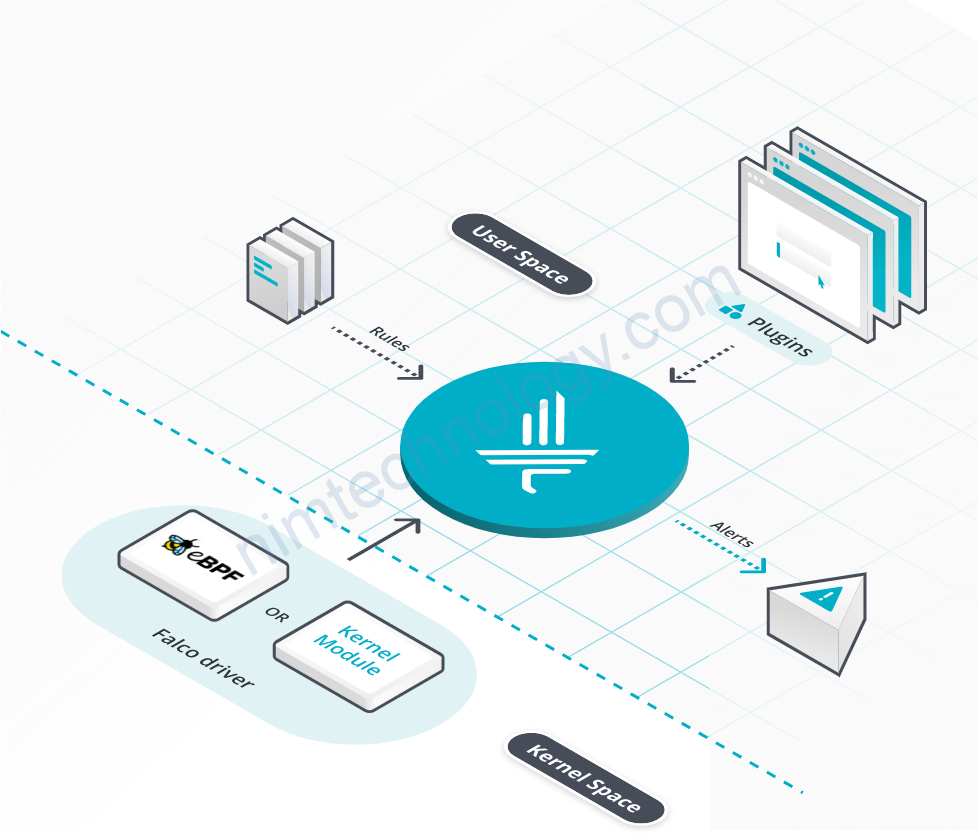
Bài này hay quá nên là mình đã lưu lại.
Link bài gốc ở đây: https://systemweakness.com/k8s-runtime-attack-scenarios-2f12816a400b
Hello, I created this article to collect my articles about Container Runtime Attack scenarios that I created for K8s and similar environments. You can think of this article as a kind of starting point for other articles. If you don’t want to reading the details of blog and want to see directly attack scenario, you can quickly go over the 4 items. Otherwise i shared below the motivation for creating such a series.
If I need to talk briefly, I wanted to create such an article series because I saw that when we use these scenarios with my consultancy work experience, my current company and my friends working in corporate companies, it was very useful for us to understand the security of the current environment (K8s and similar) and the capability of the PoC Container Security product.
1. Why

I can say that the first reason I want to create such a series is because the security of Kubernetes and similar environments is discussed theoretically in the blogs I read on Container Runtime Attack scenarios, but the practical side of the business is not addressed. My second reason is to show the problems that may occur as a result of the companies that have the orchestration environment not making the necessary security hardenning or incomplete configurations.
My purpose here is not only to produce a technical content, but beyond that I thought that the scenarios I will share, will provide you with similar benefits, as I mentioned above, as they help us measure the maturity of the orchestration solution in different business environments and control the rules of the security products running on it 🙂
When I deal with this and other details, I thought that it would be useful for those who will follow this series of articles, and I wanted to get a motivation from here and share the scenarios that I have created and will create in the future.
2. About Attack
Above, I talked about why I created the content in general and its benefits. Here, I would like to share with you my thoughts and setup in a little more detail about attack scenarios.

- In each attack scenario I will share, my goal will be to perform a specific attack.
- I will use the vulnerable images that I created and deliberately left on them while preparing the attack environment.
- There will be no content to bypass any WAF, Firewall, etc. security products.
- While one of the container images I created has web security vulnerabilities, the other one will have some useful tools found in Kali. In this way, I will be able to produce more than one attack scenario.
- I will not aim to tell you about Blacbox Pentest and its steps in attack scenarios. As a person who knows the environment and how to exploit the related vulnerabilities, I will try to create my articles, show you how the related attacks are made, and create a guide that will allow you to do the same.
- I created attack scenarios using my knowledge and experience in Web, Network, Container and Kubernetes security.
- At the end of the day, I would like to reiterate that my main goal is to provide content that will help you while measuring the safety of your environment and to write a guide that shows you how to do them.
3. Preparing the Environment
If you want to try the attack scenarios I have described in a test environment, I have briefly mentioned the installation steps below. If you want to proceed without installation, you can skip to the “Attack Lab Setup” heading.
Kubectl setup
First of all, the kubectl tool must be installed on the machine you will work on. This tool simplifies the communication between the Client and Kubernetes (you can think of it as a Docker client). Since I used MacOS while preparing this series, I shared the installation command on MacOS below, but you can check and install it on other platforms via the link.
brew install kubectl
Minikube setup
I will use a tool called Minikube to quickly create a test environment. You can run it quickly with a few commands and create a K8s Cluster on the machine you are using.
If you run a command like below, Minikube will present you an environment on Docker. If you want to work on Docker, I recommend you to install Docker first, otherwise you will get an error.
minikube start
The following command can be used to set up a more efficient environment. After this command, Controlplane + 1 Worker node will be installed in your environment.
minikube start --cpus 4 --memory 4096 --nodes 2
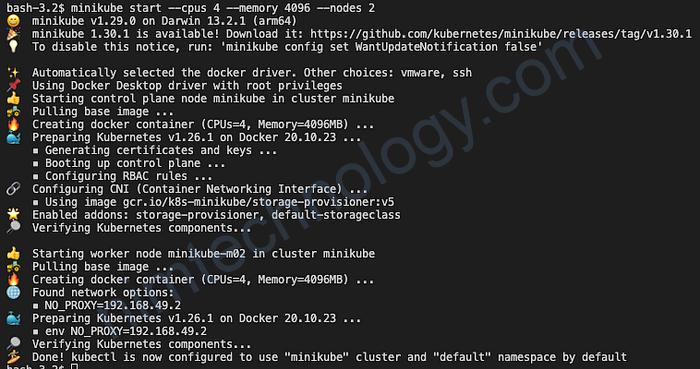
If everything is fine until this step, you will get an output like the one above. With the help of the command below, we check your Cluster environment and whether the kubectl command is working properly.
kubectl get node
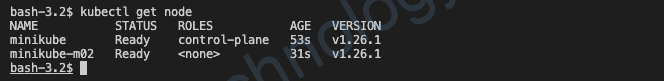
If you have received similar outputs so far, congratulations K8s is working in your environment in a healthy way.
Attack Lab Setup
Lab Info
I thought it was more efficient to use Medium just for setting up the environment and showing attack scenarios. I decided to keep the necessary information for the environment setup in the Github Repo that I shared below.
GitHub – Erdemstar/K8s-Runtime-Attack-Scenario: This repository is prepared for the personal who…
This repository is prepared for the personal who want to attack kubernetes and similar environments and see the…
When you click on the link and look at the Repository, you will see something like the following. Here there will be folders for each attack scenario.
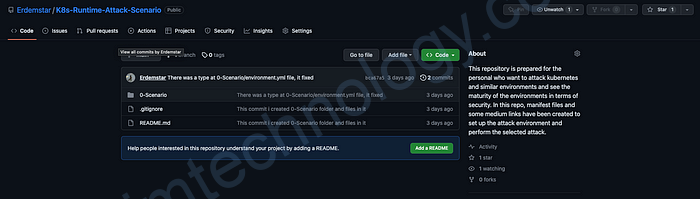
When you click on a scenario you have chosen, a screen like the one below will appear. In this screen, you will see both the manifest file for the relevant attack scenario and a Readme.md file describing the content of the manifest file.
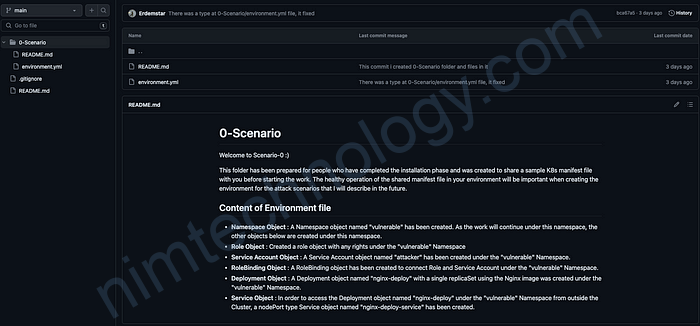
Thus, you will be able to see the file that will create the lab, and you will know what the objects in your environment are in the relevant file.
Lab Setup
I have shared a sample lab setup command for you below.
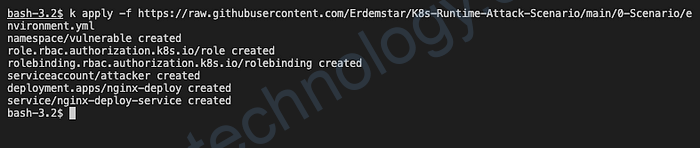
kubectl apply -f https://raw.githubusercontent.com/Erdemstar/K8s-Runtime-Attack-Scenario/main/0-Scenario/environment.yml
If you run this command as follows and get a similar screenshot, the sample lab setup has been successfully created in your environment.
Afterwards, I connected to the relevant Minicube Cluster via SSH and made a curl request as below and verified whether the environment was running. You can do similar validation as follows.
curl <master/worker-node-ip>:30080
4. Attack Scenarios