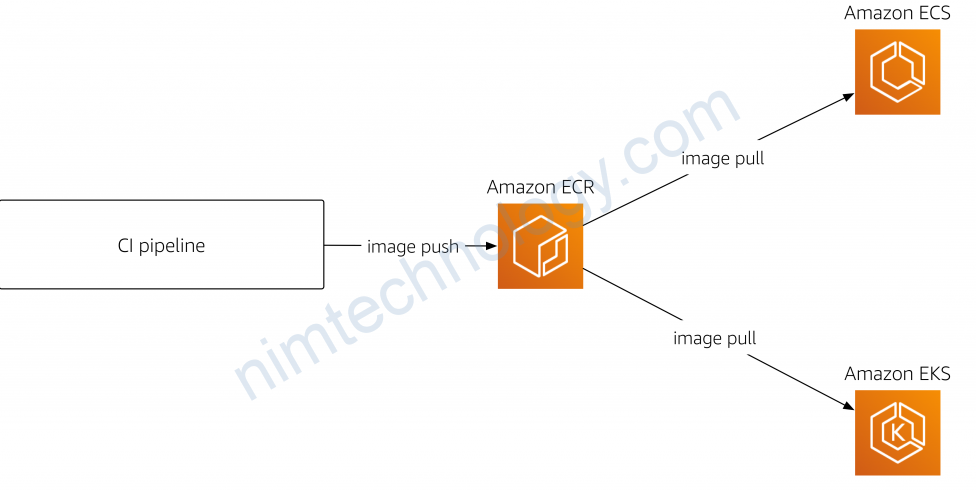
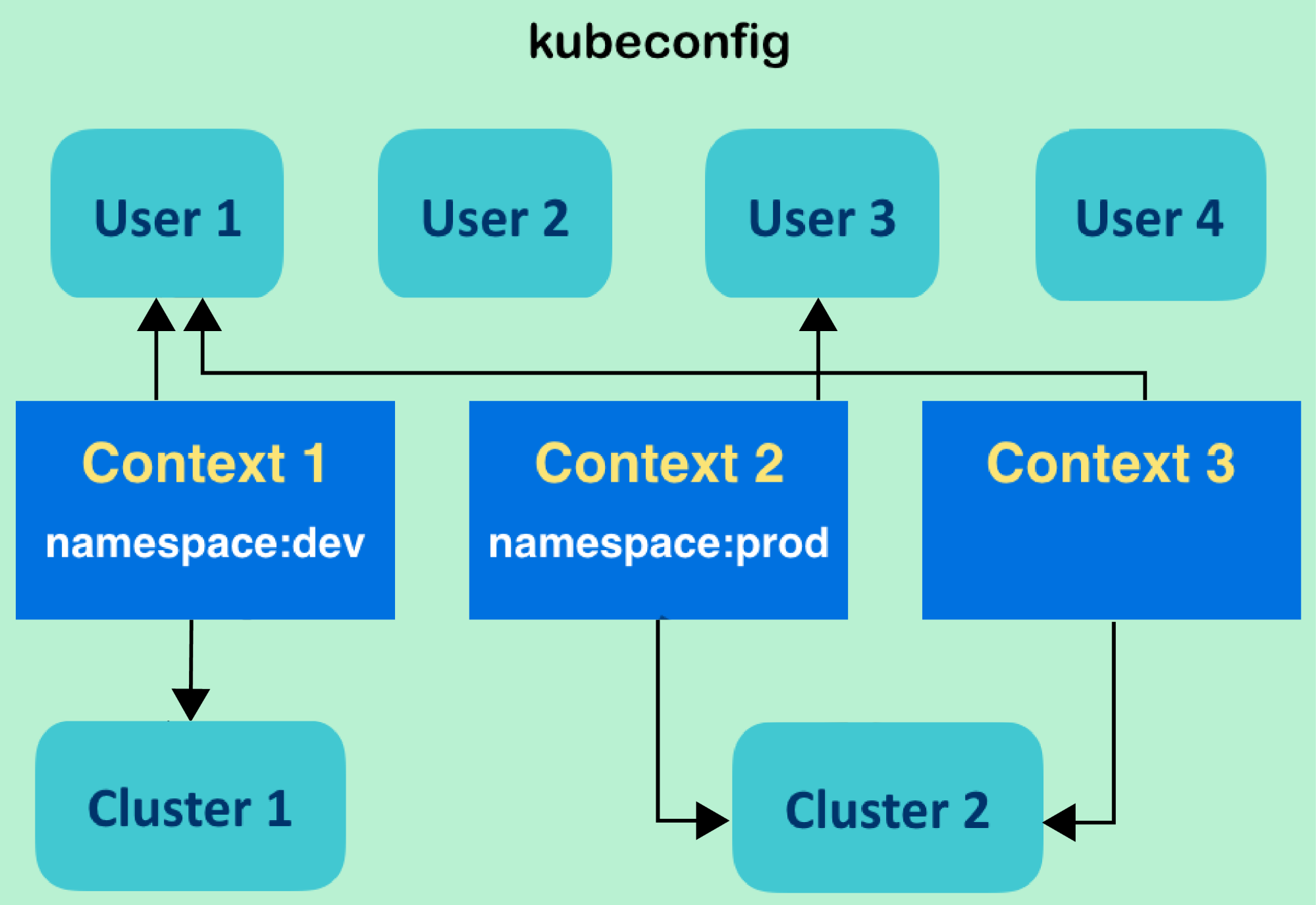
1) EKS pull image from ECR.
Chúng ta đã có 1 post hướng dẫn cài EKS thông qua terraform.
Sau khi đã cài xong EKS thì bạn kiểm tra 1 con Worker (EC2)
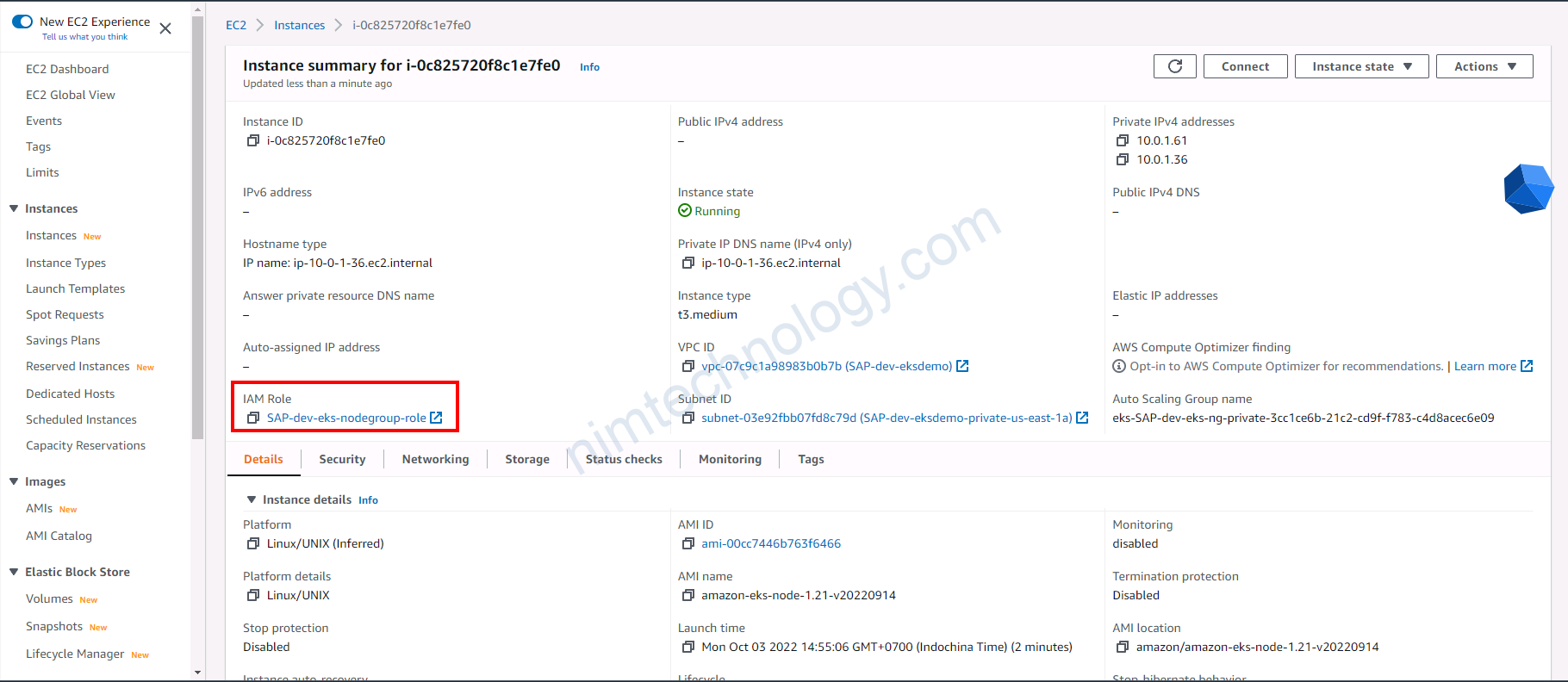
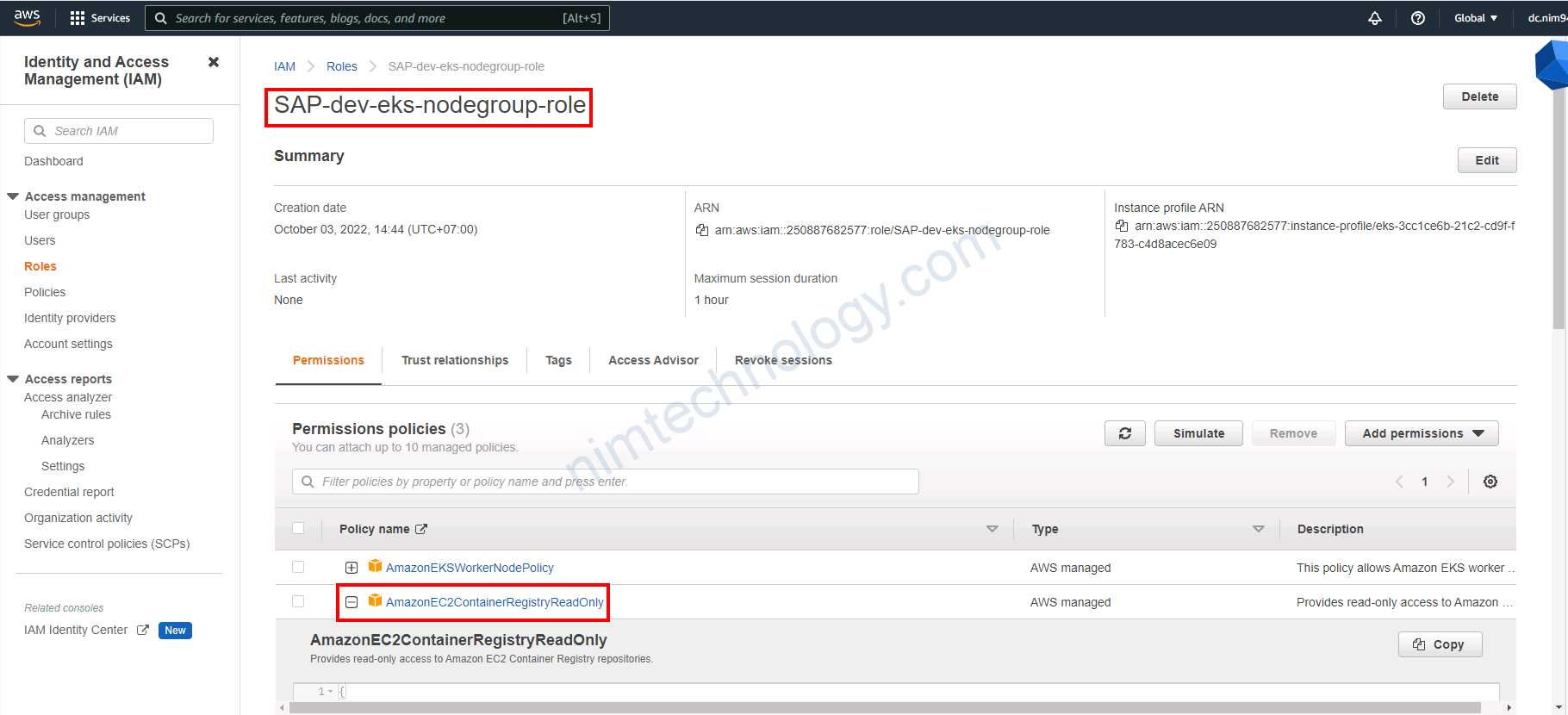
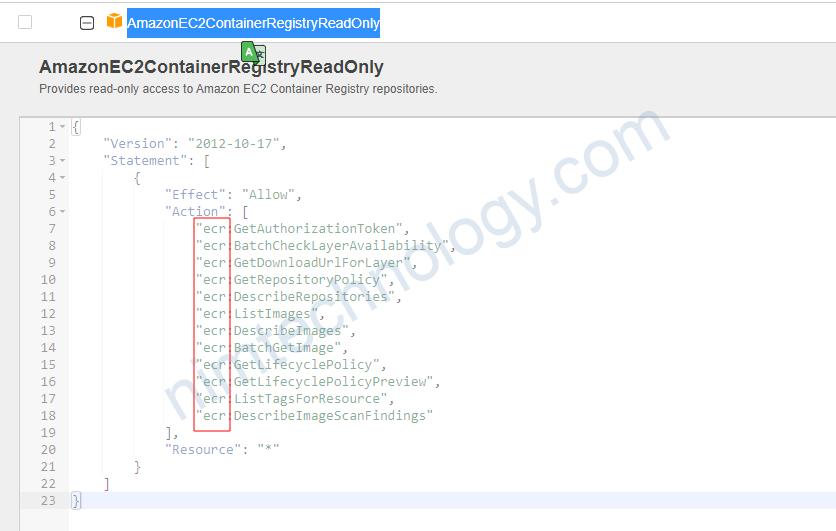
có 1 policy: AmazonEC2ContainerRegistryReadOnly
Bạn có thể tham khảo thêm link này;
https://devopstales.github.io/home/aws-eks-ecr/
Verify ECR Access to EKS Worker Nodes
- Go to Services -> EC2 -> Running Instances > Select a Worker Node -> Description Tab
- Click on value in
IAM Rolefield Role name - In IAM on that
specific role, verifypermissionstab - Policy with name
AmazonEC2ContainerRegistryReadOnly,AmazonEC2ContainerRegistryPowerUsershould be associated
2) Using imagePullSecrets to pull images from ECR.
https://skryvets.com/blog/2021/03/15/kubernetes-pull-image-from-private-ecr-registry/
Bạn có thẻ gen thử secret “docker-registry” để test thử imagePullSecrets
kubectl create secret docker-registry regcred \ --docker-server=250887682577.dkr.ecr.us-east-1.amazonaws.com \ --docker-username=AWS \ --docker-password=$(aws ecr get-login-password) \ --namespace=default kubectl create secret docker-registry regcred \ --docker-server=250887682577.dkr.ecr.us-east-1.amazonaws.com \ --docker-username=AWS \ --docker-password=$(cat token-ecr) \ --namespace=default
Giờ cần tạo ra crontab trên k8s để auto renew token
root@k8s-master:~/ecr# cat rotate-token-ecr.yaml
apiVersion: v1
kind: Secret
metadata:
name: ecr-registry-helper-secrets
namespace: production ## <<<< Change it
stringData:
AWS_SECRET_ACCESS_KEY: "ctR4JSP1rQR7JuTYDd9zLTqlMWSAEBPxQANiL+5s" ## <<<< Change it
AWS_ACCESS_KEY_ID: "AKIATU2QSHIIZQC525JS" ## <<<< Change it
AWS_ACCOUNT: "250887682577" ## <<<< Change it
---
apiVersion: v1
kind: ConfigMap
metadata:
name: ecr-registry-helper-cm
namespace: production ## <<<< Change it
data:
AWS_REGION: "us-east-1" ## <<<< Change it
DOCKER_SECRET_NAME: regcred
---
apiVersion: batch/v1beta1
kind: CronJob
metadata:
name: ecr-registry-helper
namespace: production ## <<<< Change it
spec:
schedule: "0 */10 * * *"
successfulJobsHistoryLimit: 3
suspend: false
jobTemplate:
spec:
template:
spec:
serviceAccountName: sa-production ## <<<< Change it
containers:
- name: ecr-registry-helper
image: odaniait/aws-kubectl:latest
imagePullPolicy: IfNotPresent
envFrom:
- secretRef:
name: ecr-registry-helper-secrets
- configMapRef:
name: ecr-registry-helper-cm
command:
- /bin/sh
- -c
- |-
ECR_TOKEN=`aws ecr get-login-password --region ${AWS_REGION}`
NAMESPACE_NAME=production ## <<<< Change it
kubectl delete secret --ignore-not-found $DOCKER_SECRET_NAME -n $NAMESPACE_NAME
kubectl create secret docker-registry $DOCKER_SECRET_NAME \
--docker-server=https://${AWS_ACCOUNT}.dkr.ecr.${AWS_REGION}.amazonaws.com \
--docker-username=AWS \
--docker-password="${ECR_TOKEN}" \
--namespace=$NAMESPACE_NAME
echo "Secret was successfully updated at $(date)"
restartPolicy: Never
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa-production ## <<<< Change it
namespace: production ## <<<< Change it
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: production ## <<<< Change it
name: role-full-access-to-secrets
rules:
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["regcred"]
verbs: ["delete"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: production-role-binding ## <<<< Change it
namespace: production ## <<<< Change it
subjects:
- kind: ServiceAccount
name: sa-production ## <<<< Change it
namespace: production ## <<<< Change it
apiGroup: ""
roleRef:
kind: Role
name: role-full-access-to-secrets
apiGroup: ""
---