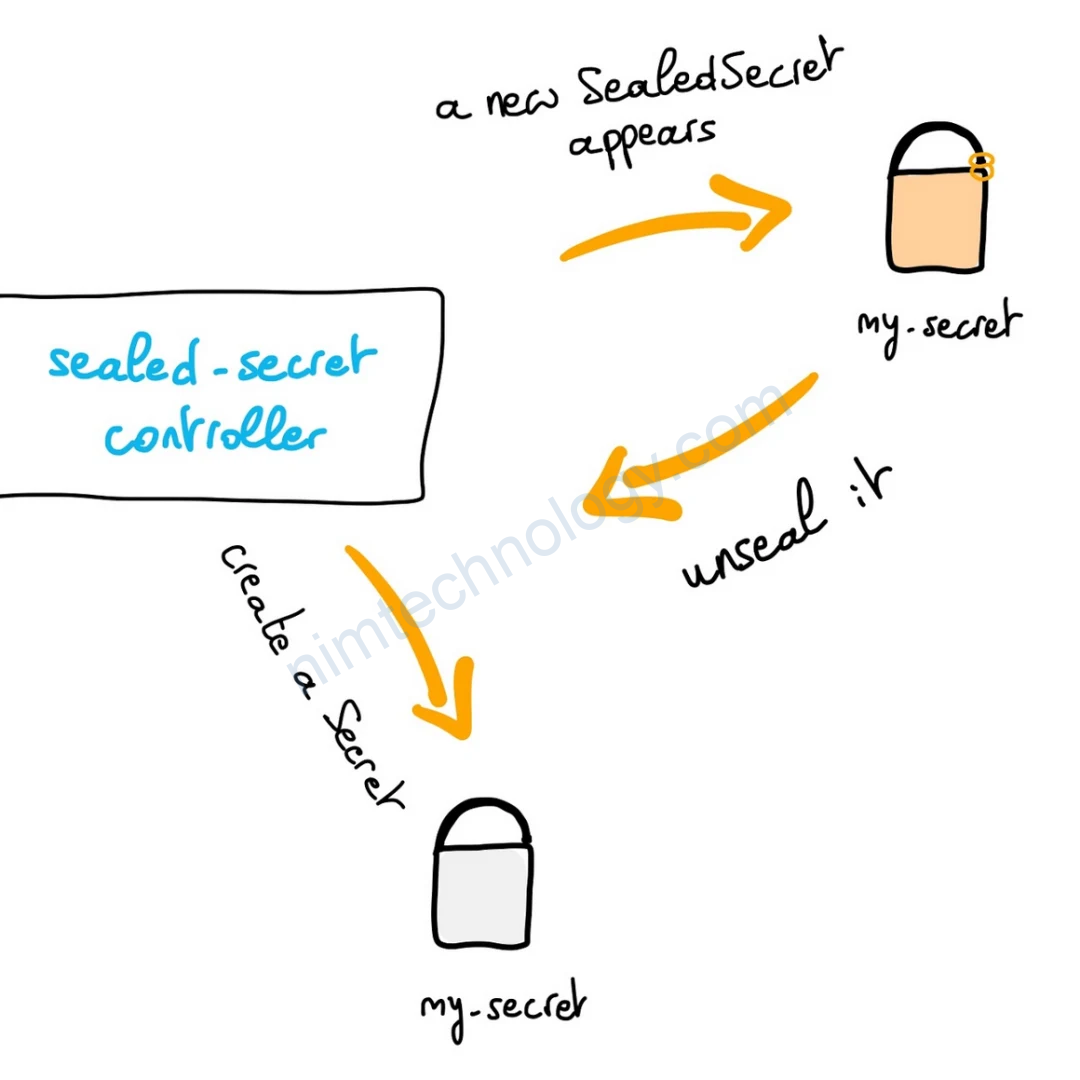
Như nhiều bài GitOps mà mình đã giới thiệu thì chúng ta sẽ cần lưu mọi template trên git, github
Nhưng chúng ta không được phép lưu secret trên k8s vậy thì phải làm sao?
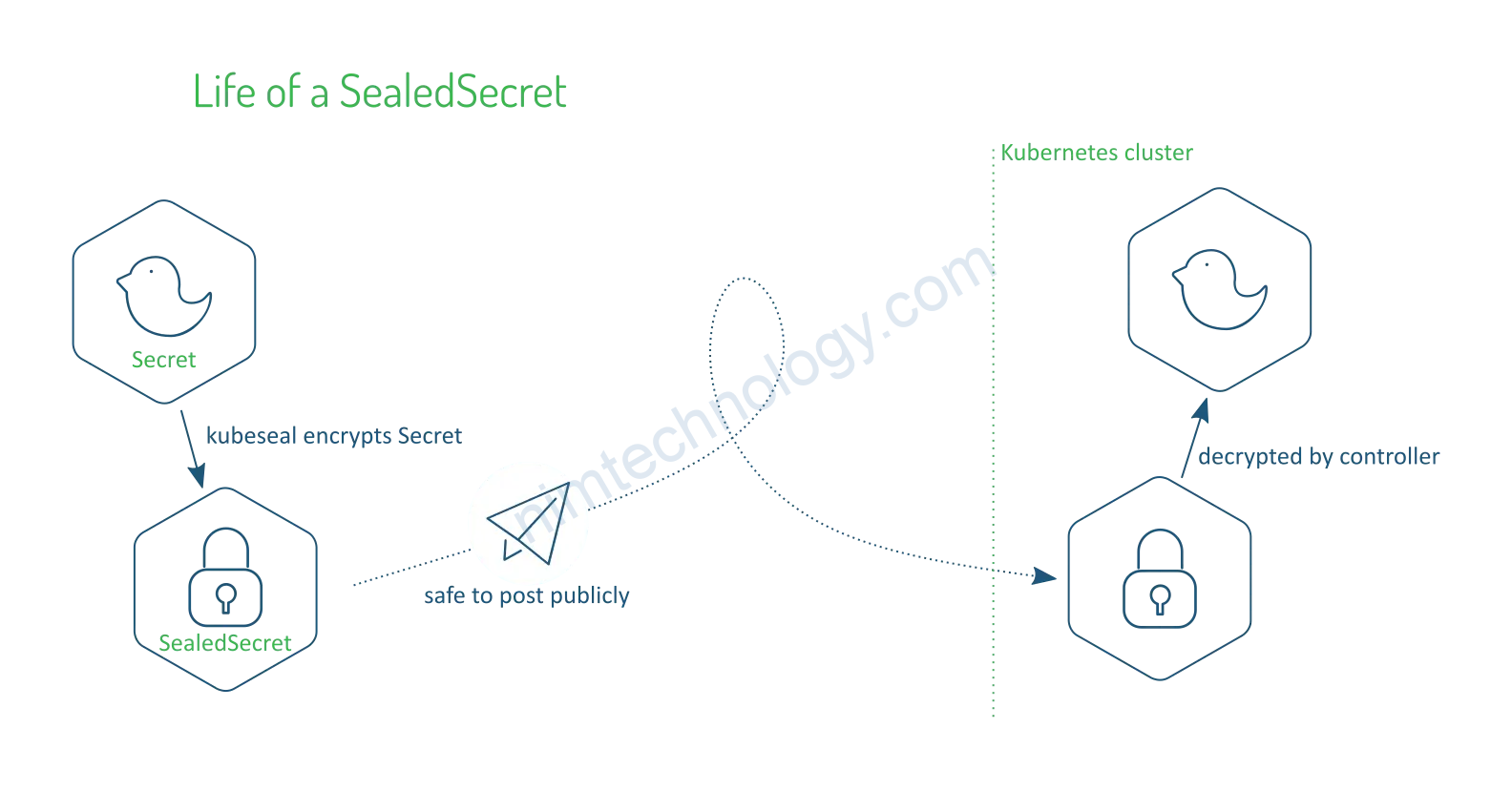
Chúng ta có 1 giải pháp của bitnami đó chính là Sealed Secrets
I) Install Sealed Secrets by helm
Đầu tiên bạn cần cài đặt Sealed Secrets trên k8s thông qua helm.
helm repo add sealed-secrets https://bitnami-labs.github.io/sealed-secrets
Thường thì bạn sẽ tạo secret trên k8s bằng cách bên dưới
kubectl --namespace default \
create secret \
generic mysecret \
--dry-run=client \
--from-literal foo=bar \
--output json
>>>>>>>>>>output
{
"kind": "Secret",
"apiVersion": "v1",
"metadata": {
"name": "mysecret",
"namespace": "default",
"creationTimestamp": null
},
"data": {
"foo": "YmFy"
}
}
Bạn sẽ thấy là value của key foo chỉ được base64 và chúng ta có thể dễ dàng decrypt được nếu bạn push lên github.
2) Install kubeseal on your laptop
Install kubeseal
bạn có thể vào link này để tìm version mới nhất.
https://github.com/bitnami-labs/sealed-secrets/releases
curl -L -o /tmp/kubeseal.tar.gz \ https://github.com/bitnami-labs/sealed-secrets/releases/download/v0.19.5/kubeseal-0.19.5-linux-amd64.tar.gz tar -xzf /tmp/kubeseal.tar.gz -C /tmp/ chmod +x /tmp/kubeseal mv /tmp/kubeseal /usr/local/bin/
3) Seal the secrets that you want.
3.1) Create and seal a secret directly.
Giờ bạn sử dụng lệnh sau:
kubectl --namespace production \ create secret \ generic mysecret \ --dry-run=client \ --from-literal foo=bar \ --output json \ | kubeseal \ --controller-name=sealed-secrets \ --controller-namespace=sealed-secrets \ | tee mysecret.yaml
Bạn để ý ở hình trên thì sẽ Sealed Secrets call vào sevice: sealed-secrets và namespace: sealed-secrets
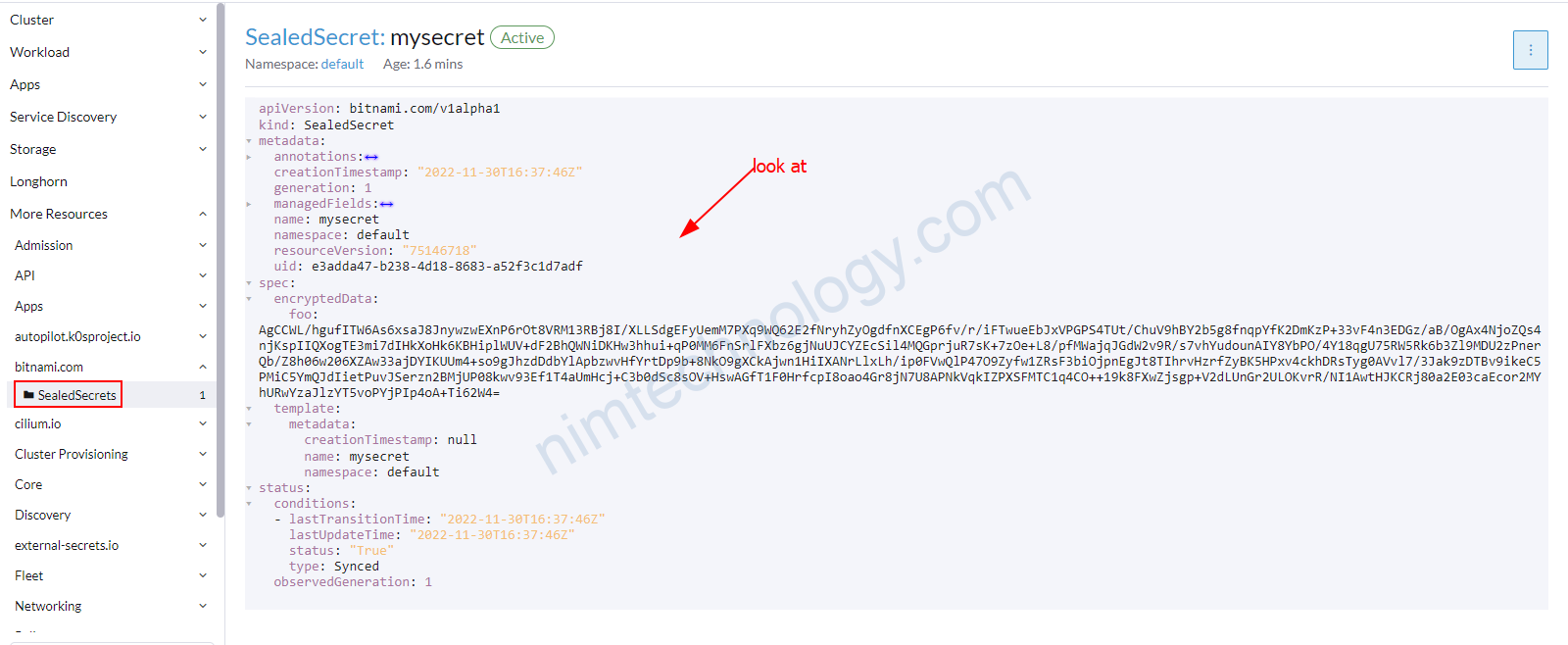
khi kiểm tra file sẽ thấy tạo có 1 kind mới là SealedSecret and data was encrypted
root@work-space-u20:~/sealed-secrets# cat mysecret.yaml
{
"kind": "SealedSecret",
"apiVersion": "bitnami.com/v1alpha1",
"metadata": {
"name": "mysecret",
"namespace": "default",
"creationTimestamp": null
},
"spec": {
"template": {
"metadata": {
"name": "mysecret",
"namespace": "default",
"creationTimestamp": null
}
},
"encryptedData": {
"foo": "AgCCWL/hgufITW6As6xsaJ8JnywzwEXnP6rOt8VRM13RBj8I/XLLSdgEFyUemM7PXq9WQ62E2fNryhZyOgdfnXCEgP6fv/r/iFTwueEbJxVPGPS4TUt/ChuV9hBY2b5g8fnqpYfK2DmKzP+33vF4n3EDGz/aB/OgAx4NjoZQs4njKspIIQXogTE3mi7dIHkXoHk6KBHiplWUV+dF2BhQWNiDKHw3hhui+qP0MM6FnSrlFXbz6gjNuUJCYZEcSil4MQGprjuR7sK+7zOe+L8/pfMWajqJGdW2v9R/s7vhYudounAIY8YbPO/4Y18qgU75RW5Rk6b3Zl9MDU2zPnerQb/Z8h06w206XZAw33ajDYIKUUm4+so9gJhzdDdbYlApbzwvHfYrtDp9b+8NkO9gXCkAjwn1HiIXANrLlxLh/ip0FVwQlP47O9Zyfw1ZRsF3biOjpnEgJt8TIhrvHzrfZyBK5HPxv4ckhDRsTyg0AVvl7/3Jak9zDTBv9ikeC5PMiC5YmQJdIietPuvJSerzn2BMjUP08kwv93Ef1T4aUmHcj+C3b0dSc8sOV+HswAGfT1F0HrfcpI8oao4Gr8jN7U8APNkVqkIZPXSFMTC1q4CO++19k8FXwZjsgp+V2dLUnGr2ULOKvrR/NI1AwtHJKCRj80a2E03caEcor2MYhURwYzaJlzYT5voPYjPIp4oA+Ti62W4="
}
}
}
Sau đó bạn chỉ cần kubectl apply -f mysecret.yaml

3.2) Seal an existing secret.
Ngoài ra bạn cũng có thể convert từ secret bình thường sang secret is sealed.
kubeseal \
--controller-name=<service_of_sealedsecret> \
--controller-namespace=<namespace_of_sealedsecret> \
-f <secret_name>.yaml -o yaml > <secret_name>-sealed.yaml3.3) Seal the secret offline
bạn thấy cách trên toàn là chúng ta cần phải kết nối đến cluster.
bạn cũng có thể gen ra 1 public key và để cho anh em trong team sử dụng public key đó để seal secret.
kubeseal \ --controller-name=sealedsecret-dev-sealed-secrets \ --controller-namespace=sealedsecret \ --fetch-cert > public-key-cert.pem kubeseal --cert=public-key-cert.pem --format=yaml < engine-logins.yaml > sealed-secret.yaml kubeseal --cert=public-key-cert.pem --format=yaml < path/secret_name.yaml > sealed-secret.yaml
chỗ <> bạn cứ để nguyên nhé
Giờ bạn có thể push file lên github òi.
4) Look up the private key pair
Để thấy được private key pair của sealed secret
Bạn vào log của con sealed-secrets-controller
kubectl logs sealed-secrets-controller-6b7dcdc847-9l8pz -n sealedsecret 2020/04/09 23:06:50 Starting sealed-secrets controller version: v0.12.1 2020/04/09 23:06:50 Searching for existing private keys 2020/04/09 23:06:53 New key written to kube-system/sealed-secrets-keyhvdtf 2020/04/09 23:06:53 Certificate is -----BEGIN CERTIFICATE----- MIIErTCCApWgAwIBAgIQILmhsVqF7t1YIRzdZp+injANBgkqhkiG9w0BAQsFADAA MB4XDTIwMDQwOTIzMDY1M1oXDTMwMDQwNzIzMDY1M1owADCCAiIwDQYJKoZIhvcN AQEBBQADggIPADCCAgoCggIBAM/LlngsOuuBtDD/9nbfjIoZ2kxgepEzzBQWmpr9 gkWpw2cqOggK3ZdEv+JYw/dxJIZ7E8G/PNiY7YzcR1JDbFxclmvzuzaGDLhUdCzQ X34ZJKOcIRAAuTYZiW60laRNVm37r68/tpok48I8+YxCD7qVtJ3y6ddRKt8iPMn2 mOZLohjy7pbZpcRp5tdS0lU8ZavdcYaUwIjxQR8XUS00nj4PIjVyKOGszjVac5bv D4HTAZcLMNpe2iECQziZ4S/HmlBTR7+4z8hF9fk+aAy9ZeCvAZMGYBY3Um+x3qqz 3cNdlA6IF9nk1aWMzXkyx9K9CE2QIblT4WQVyB7ZYxPTtlpau9XsNGjBI4DzrcHH VdDkUQEpNYwkxqpNndJlWSS5ZnglgoOwYLob4XT4hoqoqyrO5gCUKlarofmdmYm4 ELUeGPfYKlKP6rKOxQUQ0FHQL6Bvwx/Xx5wr6r1ylrC+++NFO6lMrQ0GhvYvtxN5 Ut0iy8fvXXuBP5HI8eBTEj0M7pAEZ+o/o+91N41KwuRoSBIOPD6q0e+ULBQ87Hth gpuskPmQe5lT4dv0TuSTjdJg4LQuApm+w0ta4FXX9PoXoojSaHy0EoQQvw4bAr8x 8ioz6ogmGSyFPVF/qnBnQpH5RqiWAIW1jUgt2SIluNi8Zqc4IjImIaI/ZRObElqJ qXAXAgMBAAGjIzAhMA4GA1UdDwEB/wQEAwIAATAPBgNVHRMBAf8EBTADAQH/MA0G CSqGSIb3DQEBCwUAA4ICAQBPyUeKHuk0D0XYRjiY9WQT0hEmH5ABP7Jypz9TnElz asuIorEtaUEhtzKj1L+zEkyNzZzeKurDE9PL2xQB3HR675y0bDPS1ndpLDDIU7qt 38rvhb7iHbgWPti7EeKteBaNVvcaGfwhG8vnYoKKI8KzTy04rk2/0OFQNzpXOHra Yw+mlho3MHtlT5AyTAuUqSXbRXLTMKOuXQlcGwdGAxiaV5i40AkfUICDhGZnMF8F JNujDL0kpDF04qybMrJsOlHu1ClJWKcrxQh7v/ITfFdgw3N/lnA+OBXoXOs+VL+4 s6A20IddIBAaTd04ajmIZa7FEXSj+yMA2v7+gLE8POQlQANVNH2iJ6kgePlQB2+9 gdXeQIKwWyC9cCiN/yvCWz58fb2wS5lVE0SL7Jp9A42N6C+x+Hfy4jWTSB+SAQ6F TKGWNHh9G1ghhFbq8cDShBsOr8MrBgxeWMlXG7o0yZlSbiC64FpZn2tYE3Elc8VX kyhv+WxwggBsuk8qvzBK8sPRT+VmQ1w/GUdsJXw/GWaL2m3KZZyfTka3OwM1R7tJ xgvkU74FVLk+SwcTVdCewfahSkmm43vQFr8u6EHqsYN2jY2h9ka8jTOzCof1OiPS bwMtSuxW82ty6Pu3UyskQBRLmLOAuy/nmXZKjcdtB/OLELbUO44NVgxkIhWCLrCU ew== -----END CERTIFICATE-----
Hoặc là bạn look up in secret: sealed-secrets-key
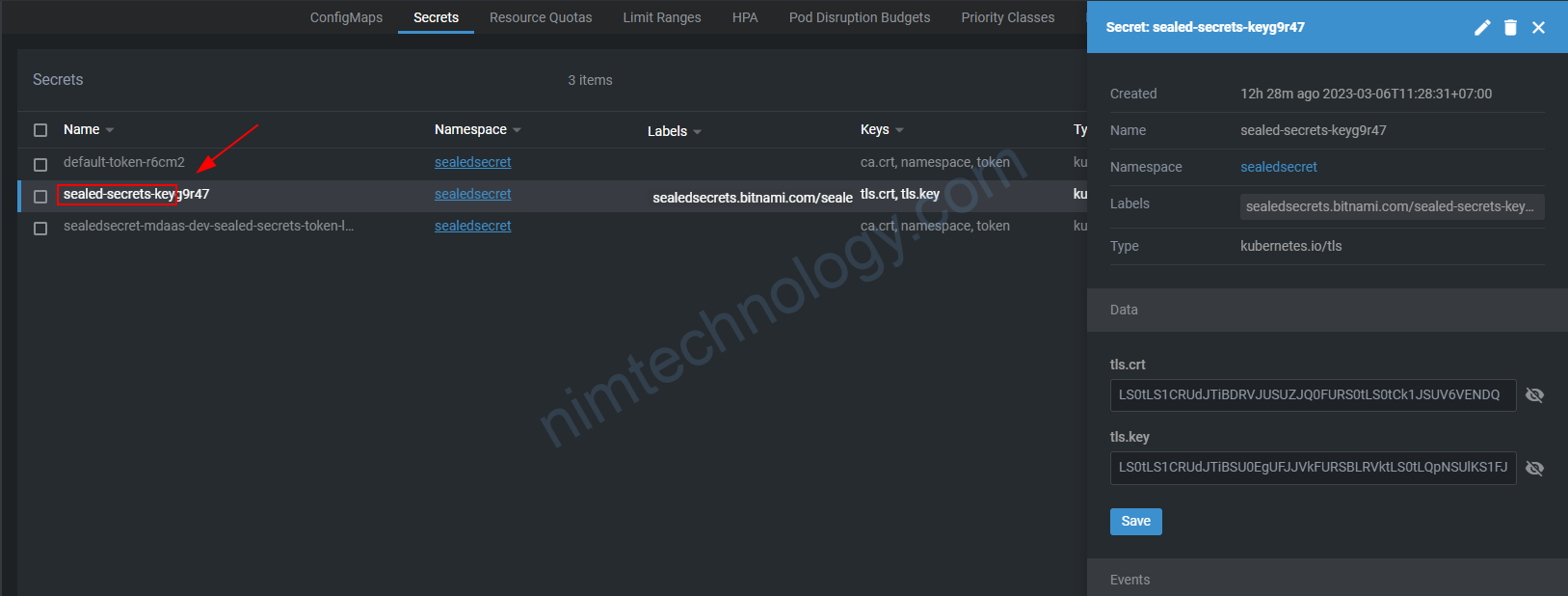
Bạn có thêm xem 2 video sau:
5) Decrypt the sealed secrets.
Nếu bạn muốn update sealed secrets thì phải làm sao?
Bước 1 là thực hiện re-encrypt seales secret.
Vì là 1 sau một thời gian thì hệ thống đã gen 1 seal key mới
kubeseal \ --controller-name=sealedsecret-nim-dev-sealed-secrets \ --controller-namespace=sealedsecret \ --re-encrypt --format=yaml < ingress-secret-sealed.yaml > ingress-secret-sealed1.yaml
Bước 2 là get key của sealed secret về máy tính.
kubectl get secret -n sealedsecret sealed-secrets-key2xpnb -o yaml >> main.keyTiếp theo là thực hiện decrypt secret
kubeseal \ --recovery-unseal --recovery-private-key main.key \ --controller-name=sealedsecret-nim-dev-sealed-secrets \ --controller-namespace=sealedsecret \ --format=yaml < ingress-secret-sealed1.yaml > engine-logins.yaml
error
Nếu bạn re-encrypt mà gặp lỗi
error: cannot re-encrypt secret: an error on the server ("") has prevented the request from succeeding (post services http:sealedsecret-XXXXX-dev-sealed-secrets:http)thì nguy cơ là key để decryt sealed secrets đã không còn. Bạn cần manual copy secret trên k8s và thực hiện sealed lại secret đó.
services “sealed-secrets-controller” not found
Nếu bị lỗi trên thì bạn tham khảo link dưới nhé!
==> https://github.com/bitnami-labs/sealed-secrets/issues/758#issuecomment-105687923
Bring your own keys and multi-cluster scenario
https://dev.to/ashokan/sealed-secrets-bring-your-own-keys-and-multi-cluster-scenario-1ee8
Rotate the controller’s sealing key
Sealing keys are automatically renewed every 30 days. This means a new sealing key is created and appended to the set of active sealing keys the controller can use to unseal SealedSecret resources.
Bạn có thể điều chỉnh deployment/sealed-secrets-controller
spec:
containers:
- command:
- controller
- --key-renew-period=5m
kubectl edit deployment/sealed-secrets-controller --namespace=kube-system
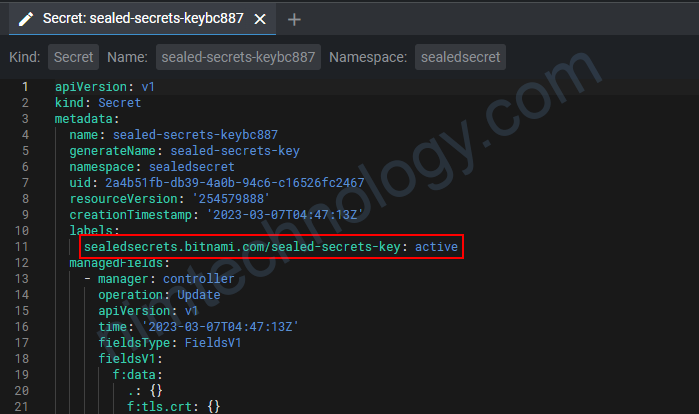
sealedsecrets.bitnami.com/sealed-secrets-key: active
We can also use kubeseal --re-encrypt to encrypt a secret again.
Let’s say we want to encrypt with the latest key.
This will re-encrypt the sealed secret without having to pull the actual secret to the client
kubeseal \ --controller-name=sealedsecret-dev-sealed-secrets \ --controller-namespace=sealedsecret \ --re-encrypt --format=yaml < engine-logins-sealed.yaml > engine-logins-sealed1.yaml cat engine-logins-sealed.yaml \ | kubeseal \ --controller-name=sealedsecret-dev-sealed-secrets \ --controller-namespace=sealedsecret \ --re-encrypt -o yaml