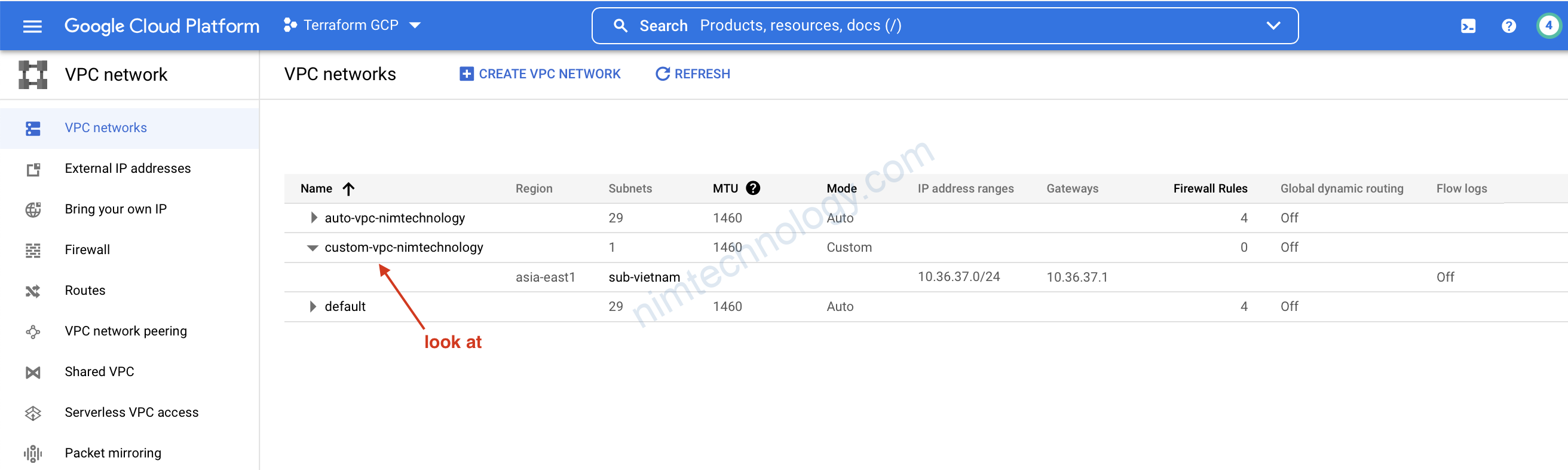
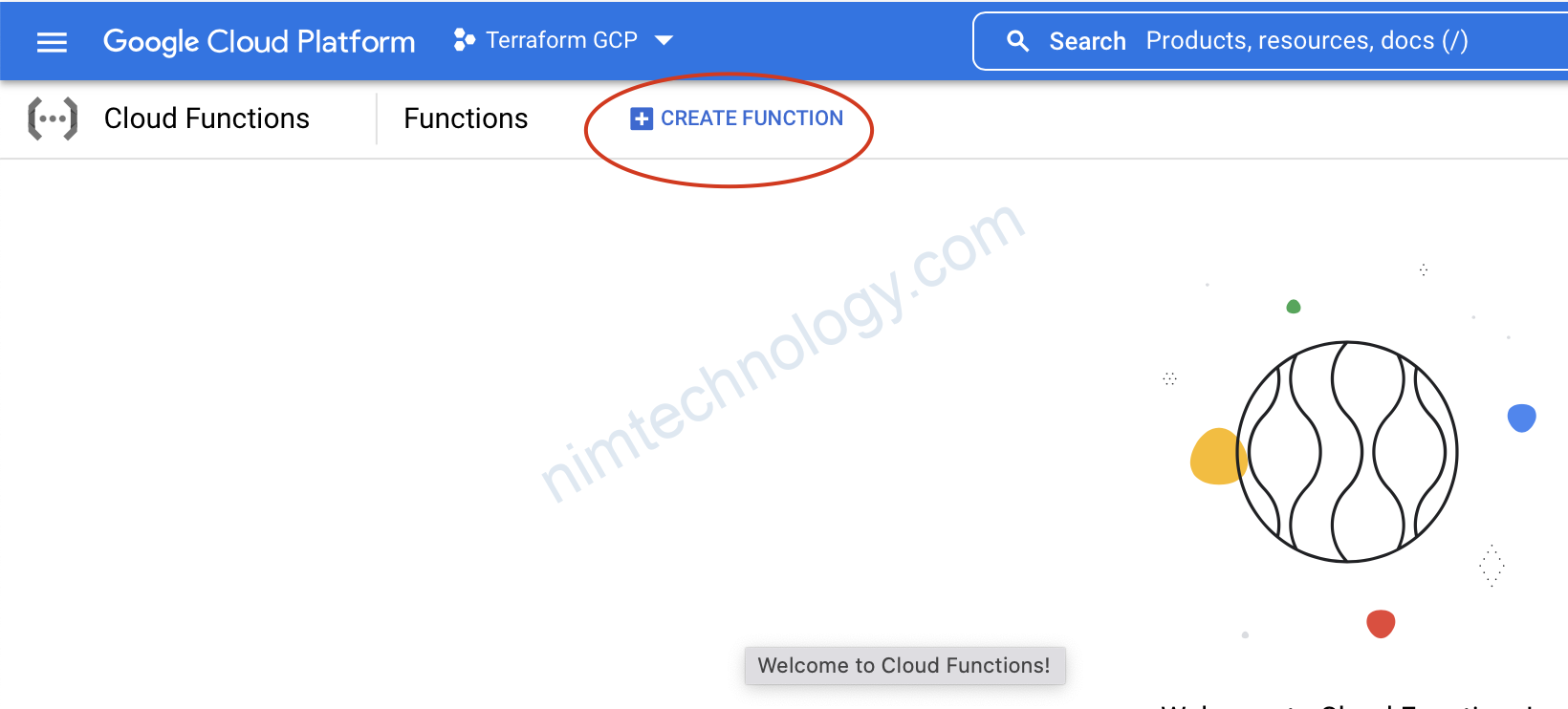
1) Deploy Cloud Function – Console
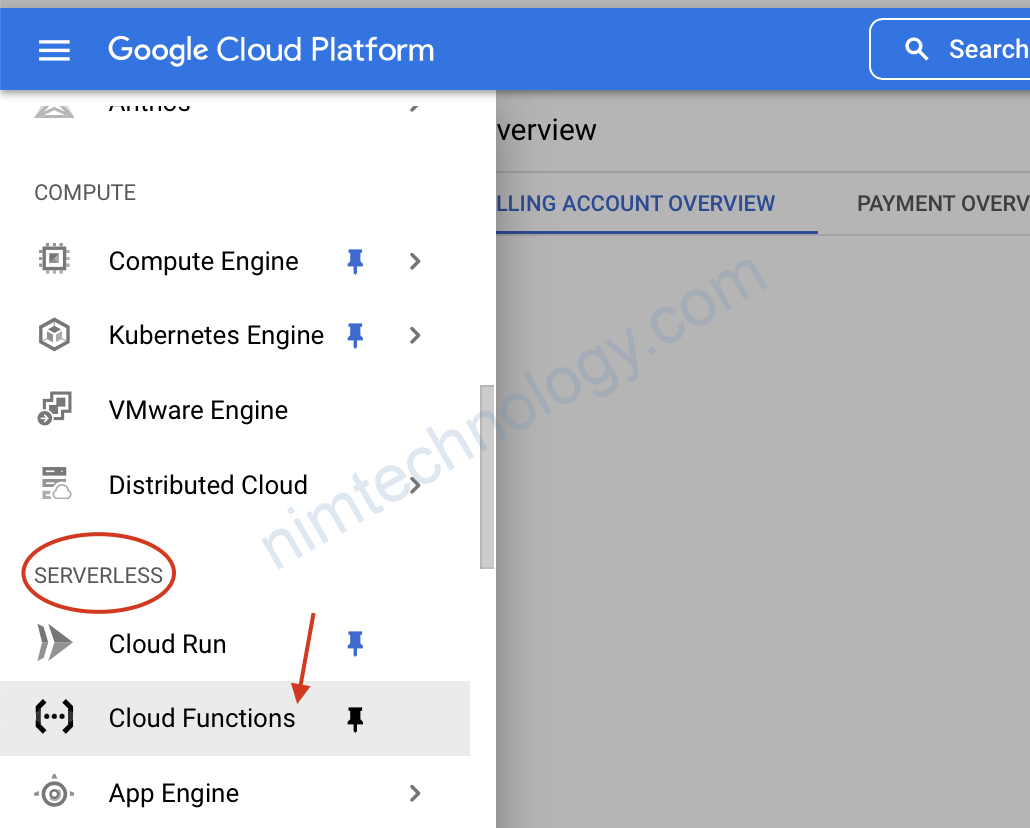
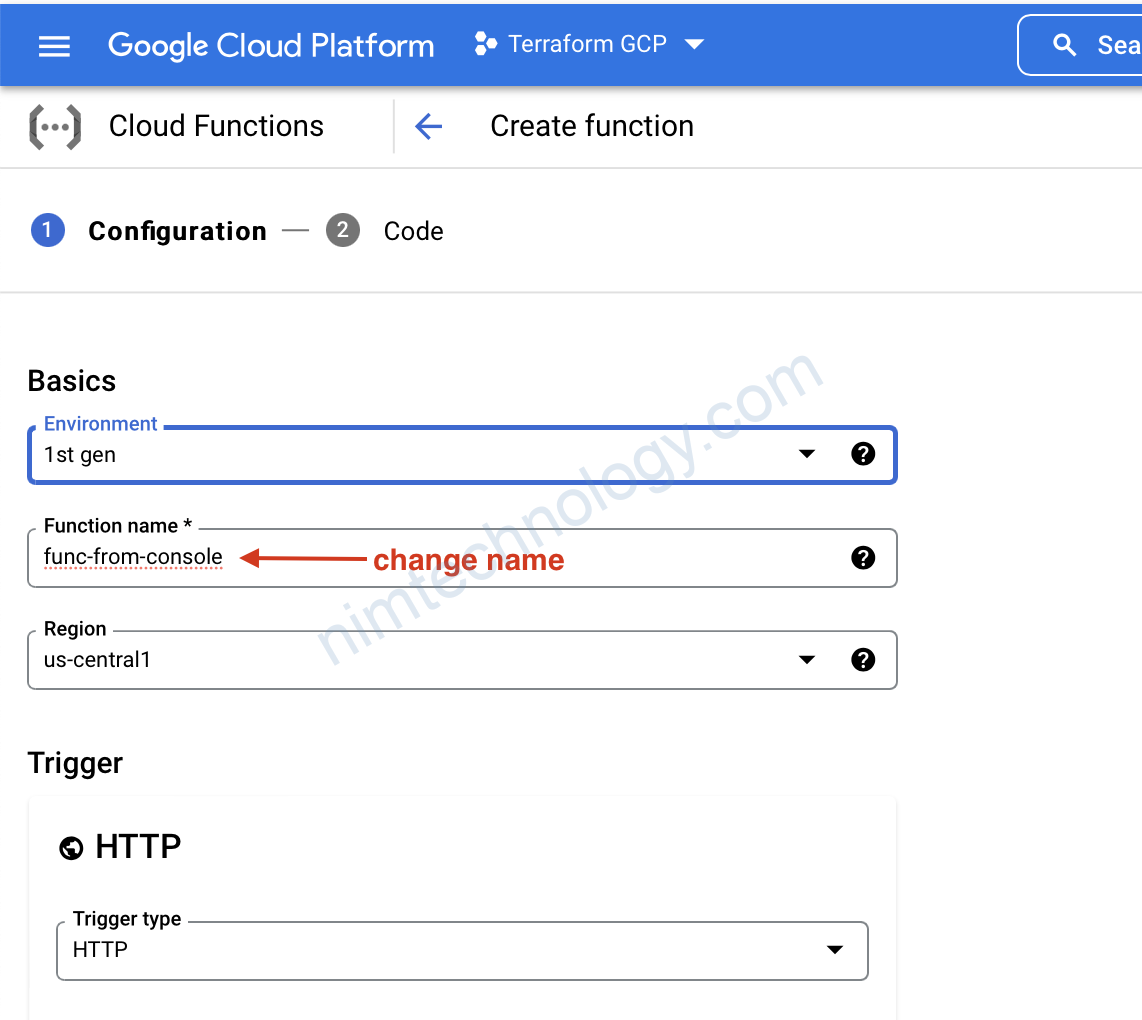
bạn có thể đổi region nếu muốn.
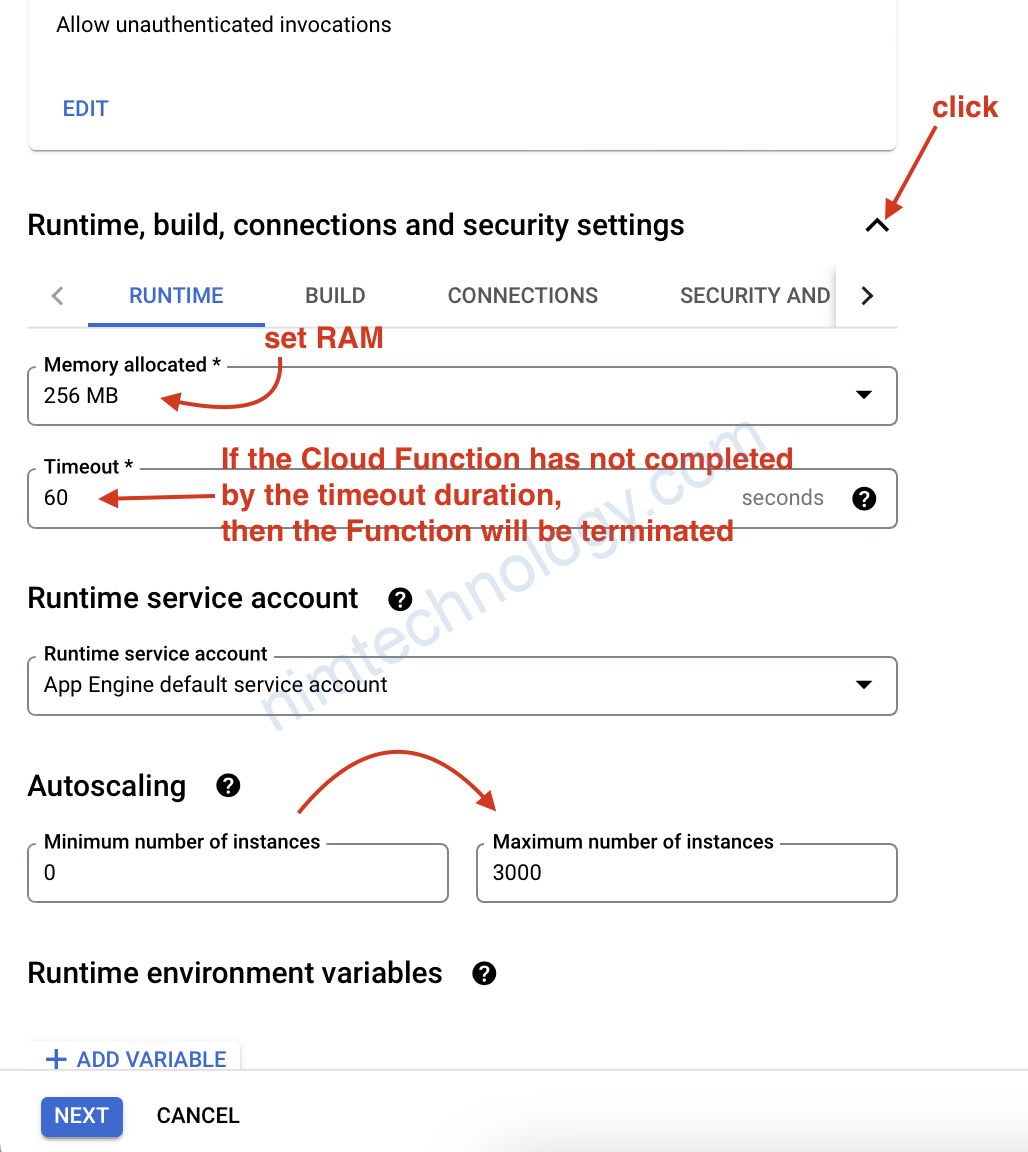
bạn set RAM, thời gian timeout, auto scale luôn.
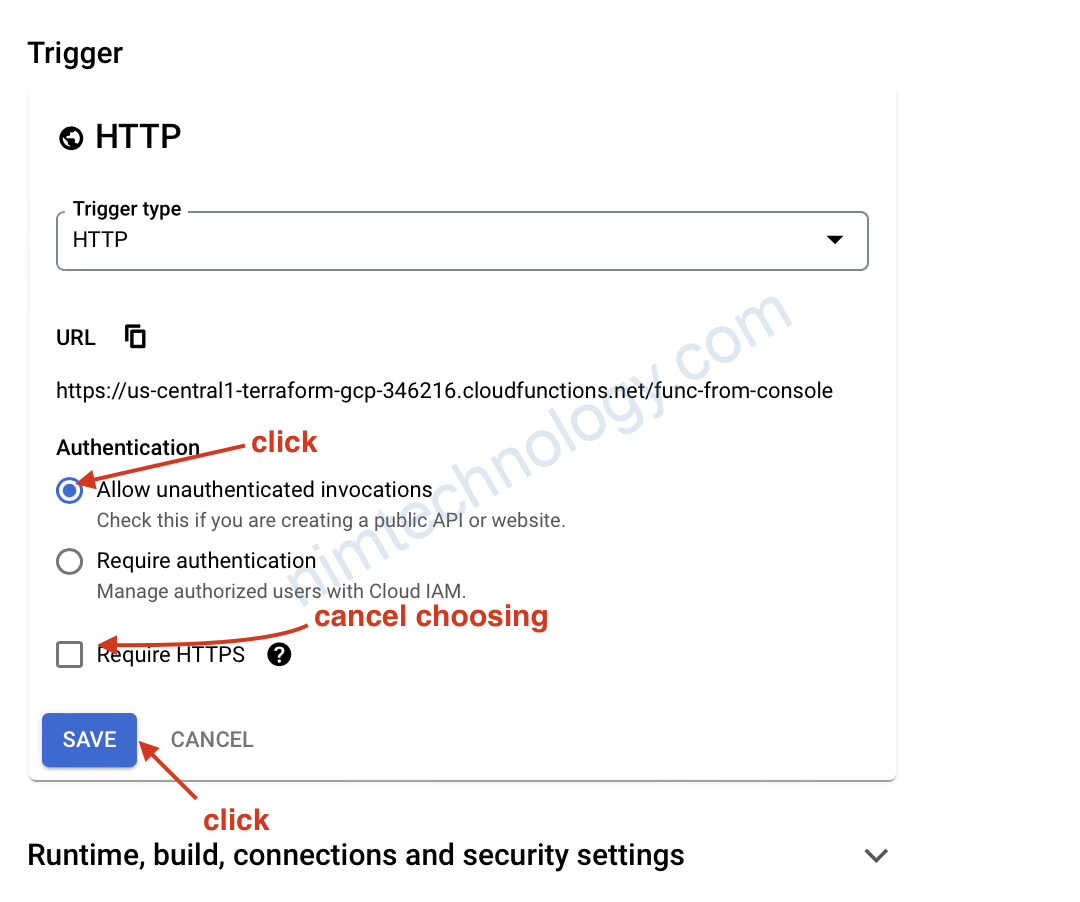
KHi xong thì anh em nhấn NEXT
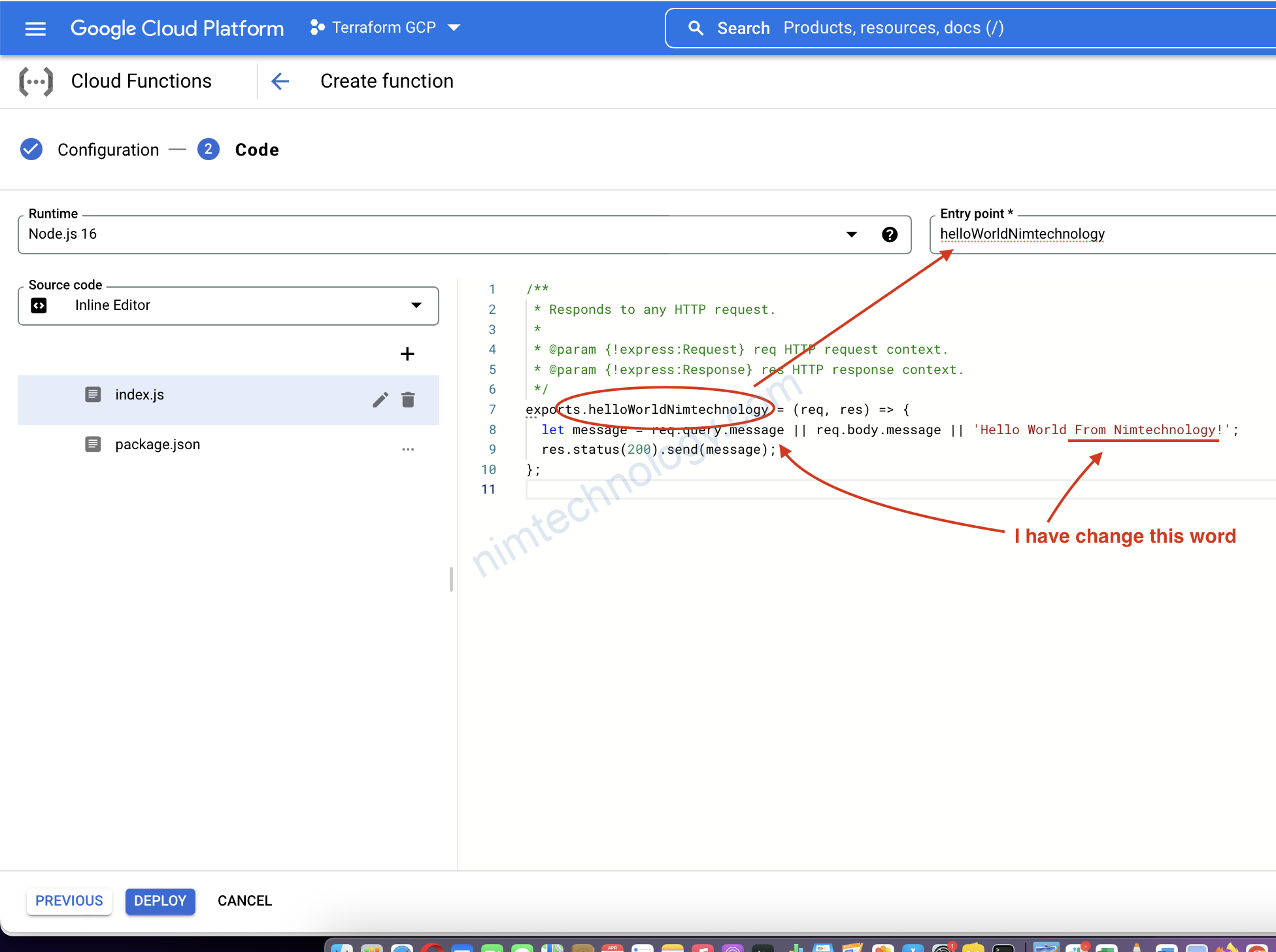
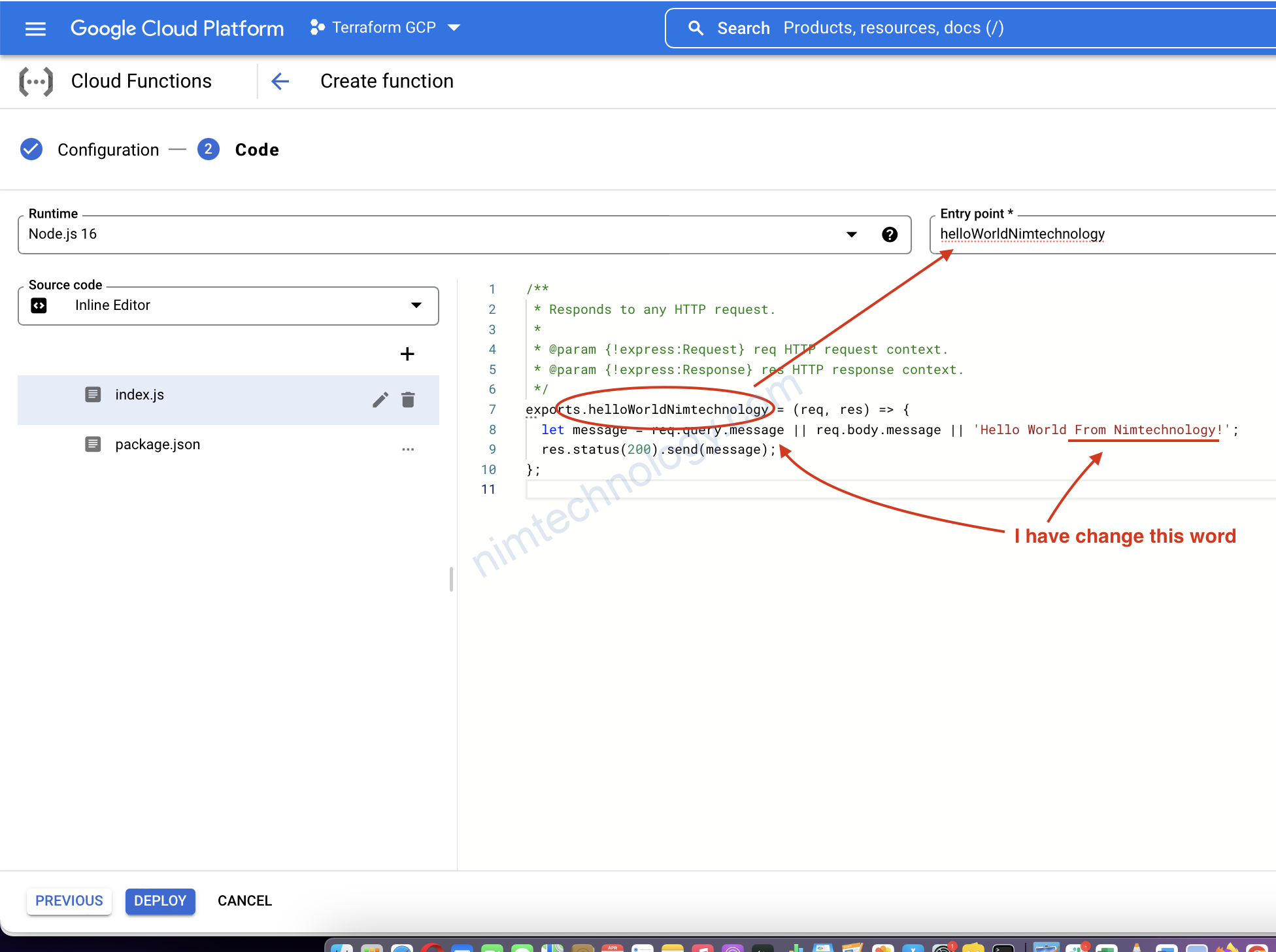
mình sài Inline Code có sẵn
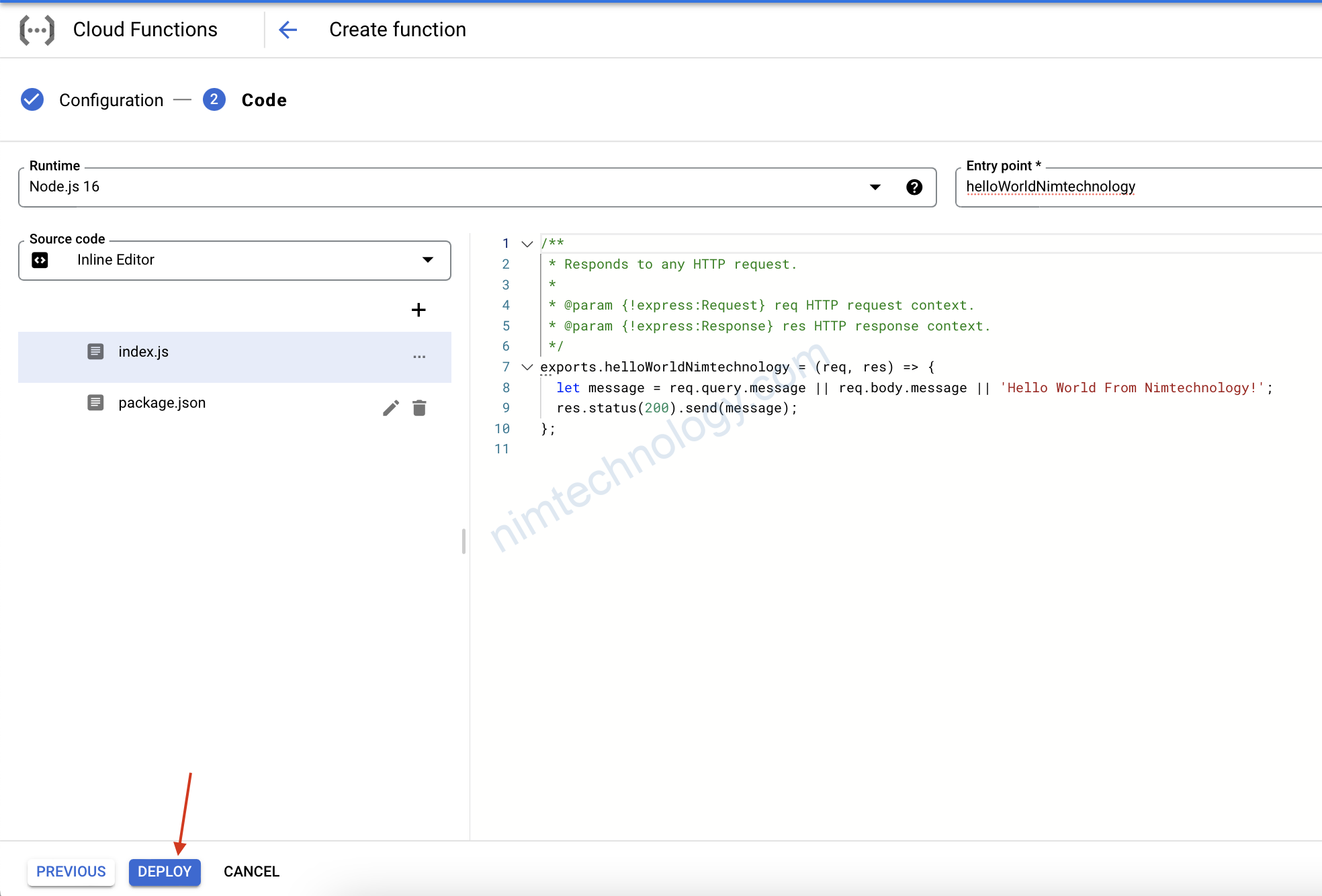
file: index.js
/**
* Responds to any HTTP request.
*
* @param {!express:Request} req HTTP request context.
* @param {!express:Response} res HTTP response context.
*/
exports.helloWorldNimtechnology = (req, res) => {
let message = req.query.message || req.body.message || 'Hello World From Nimtechnology!';
res.status(200).send(message);
};
file package.json
{
"name": "sample-http",
"version": "0.0.1"
}
Giờ các bạn ấn deploy luôn nhé
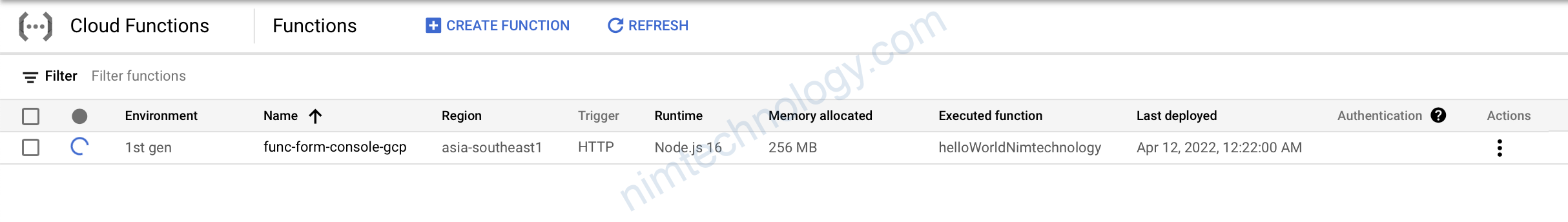
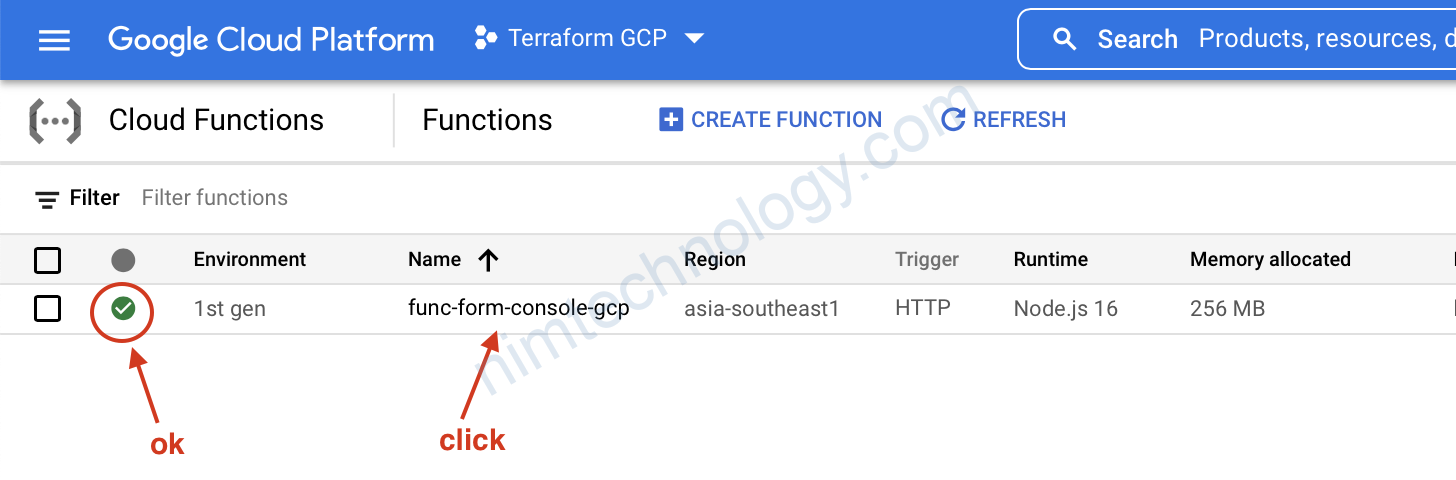
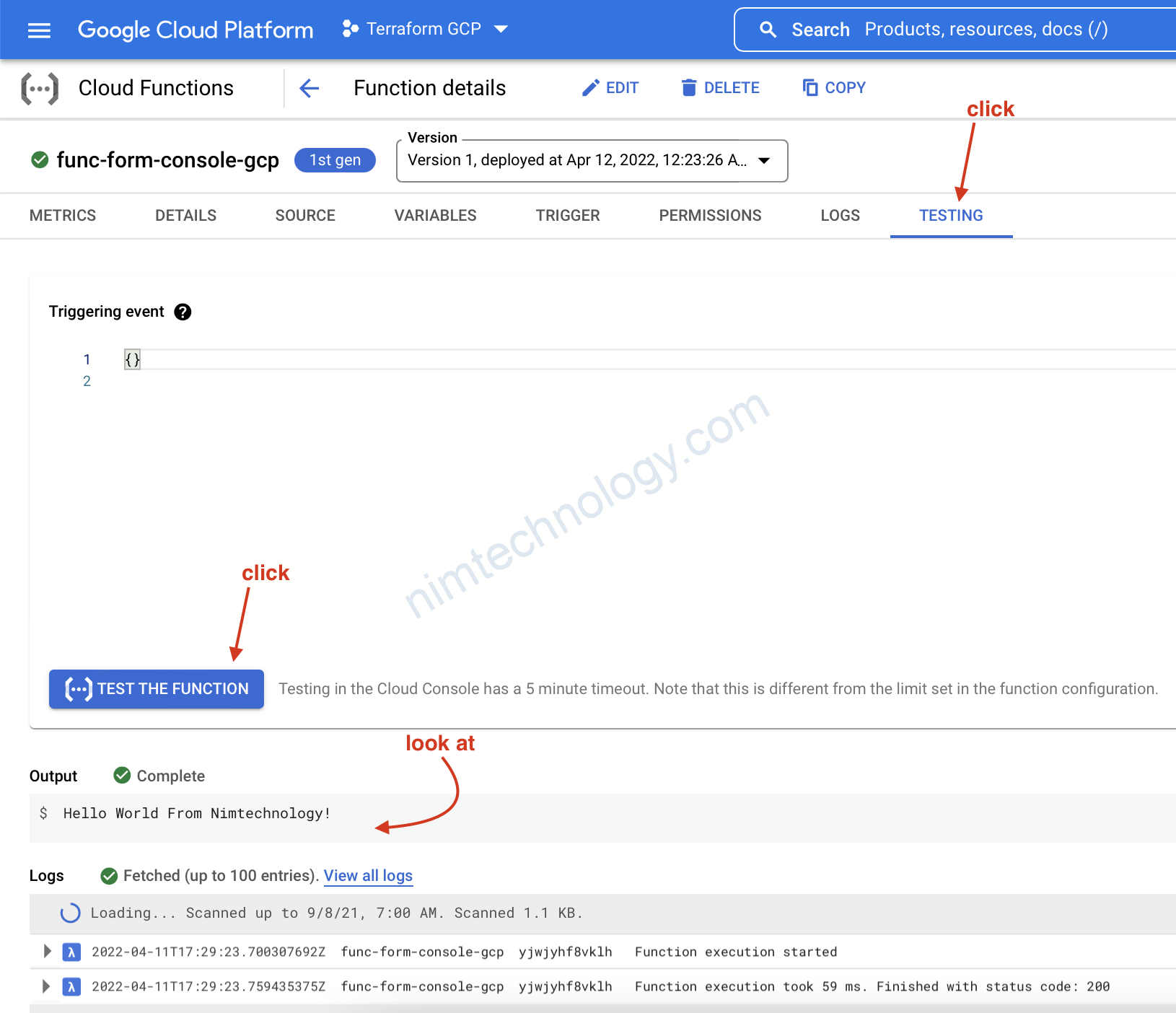
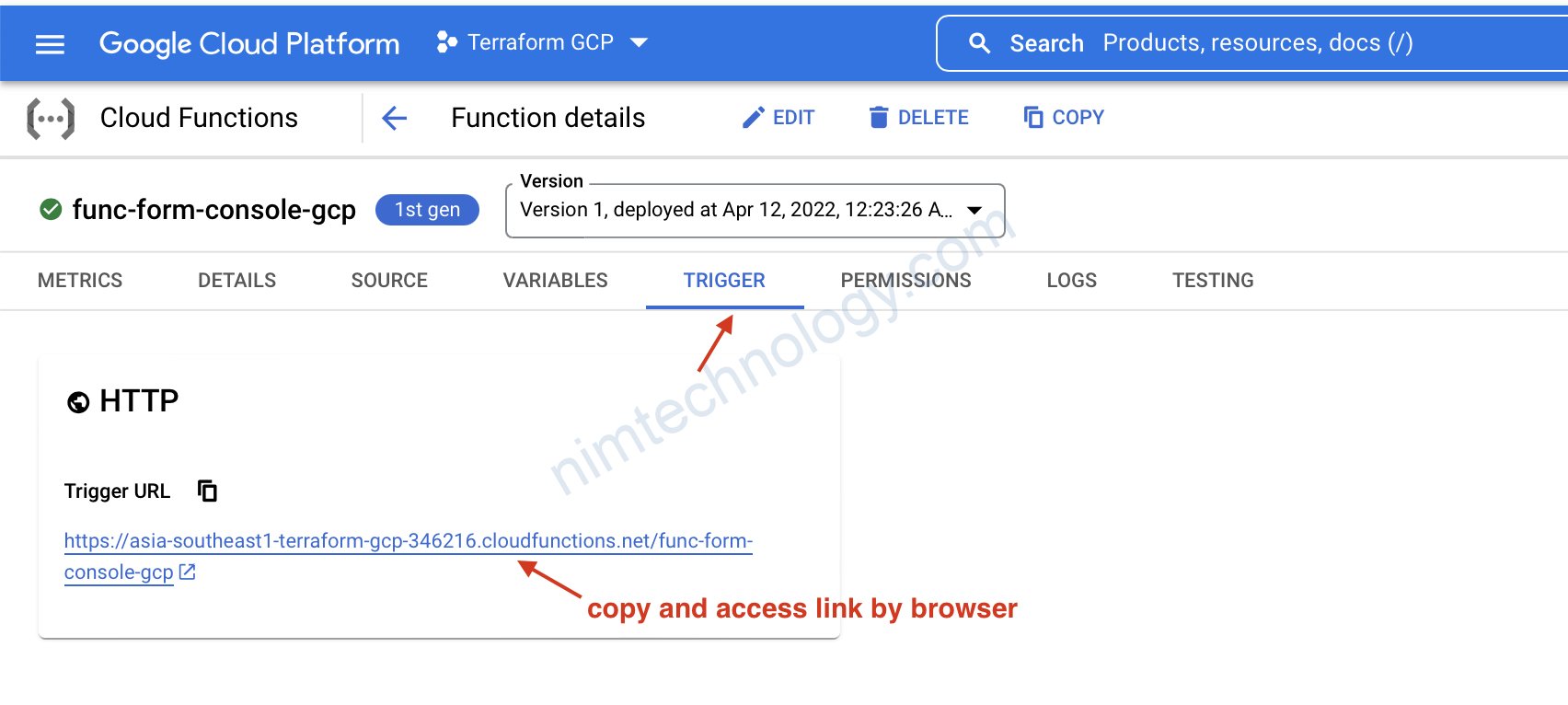
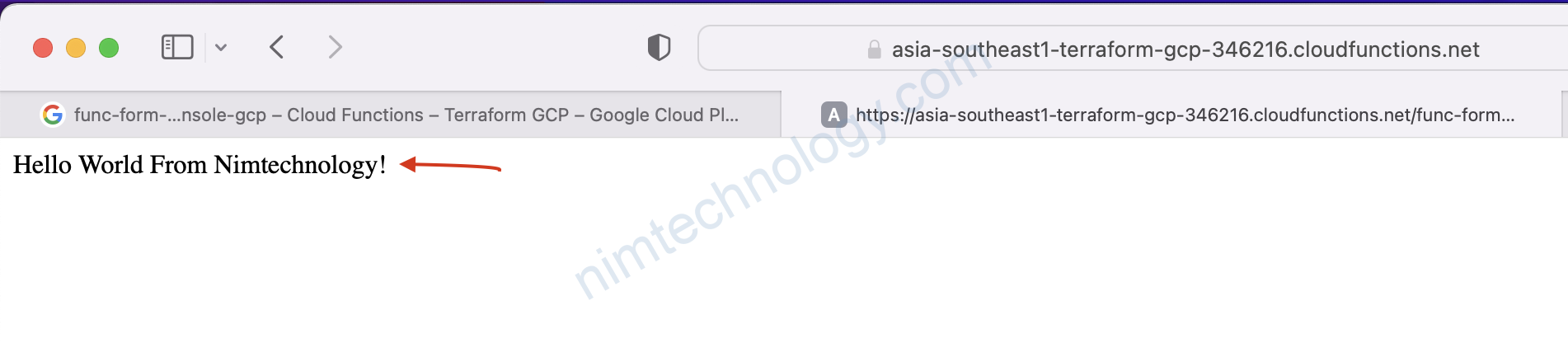
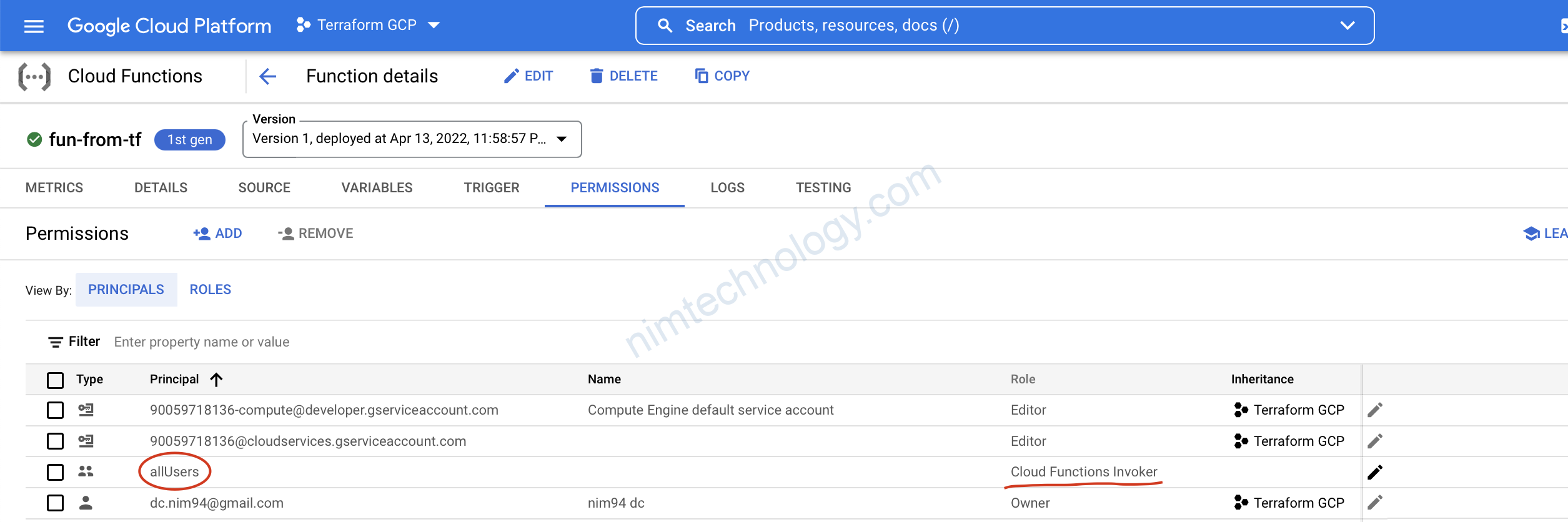
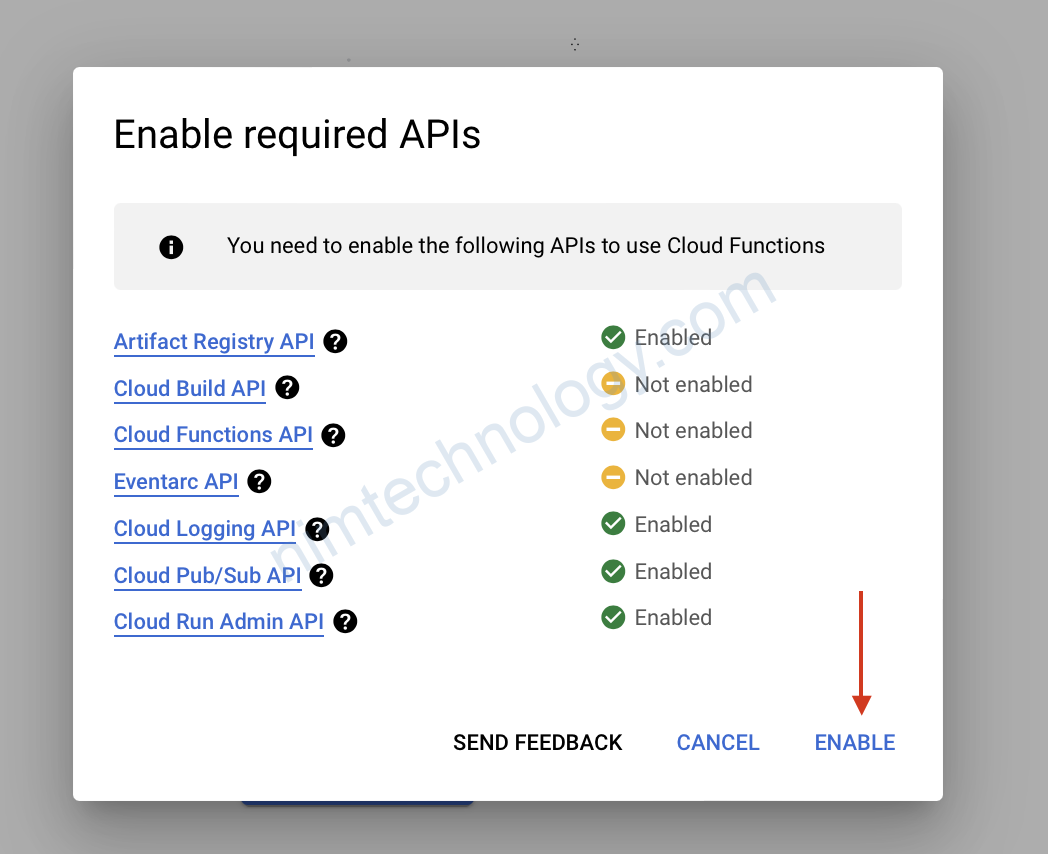
Chúng ta sẽ kiểm tra permissions
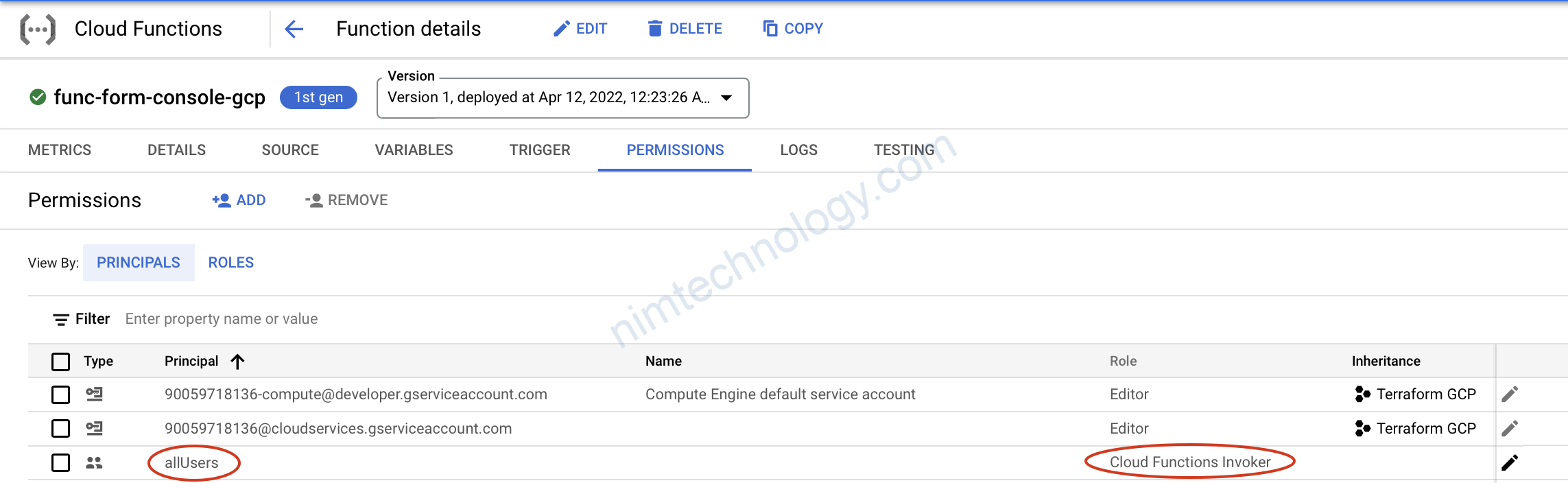
2) Cloud Function – Terraform
Sau đây mình cung cấp full code
#Create Bucket
#Upload index.zip
#deploy function
#policy binding
resource "google_storage_bucket" "fun_bucket" {
name = "fun_bucket_tf"
}
resource "google_storage_bucket_object" "srccode" {
name = "index.zip"
bucket = google_storage_bucket.fun_bucket.name
source = "index.zip"
}
resource "google_cloudfunctions_function" "fun_from_tf" {
name = "fun-from-tf"
runtime = "nodejs14"
description = "This is my first function from terraform script."
available_memory_mb = 128
source_archive_bucket = google_storage_bucket.fun_bucket.name
source_archive_object = google_storage_bucket_object.srccode.name
trigger_http = true
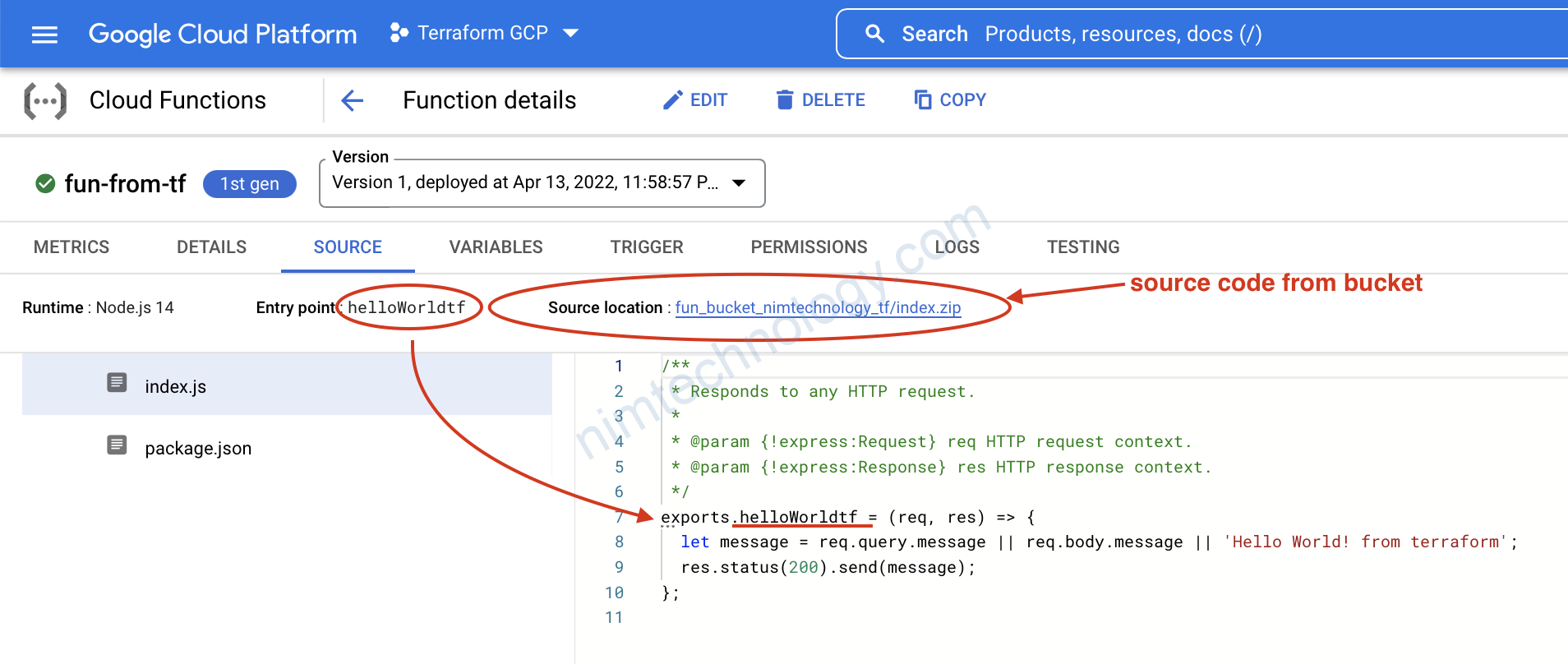
entry_point = "helloWorldtf"
}
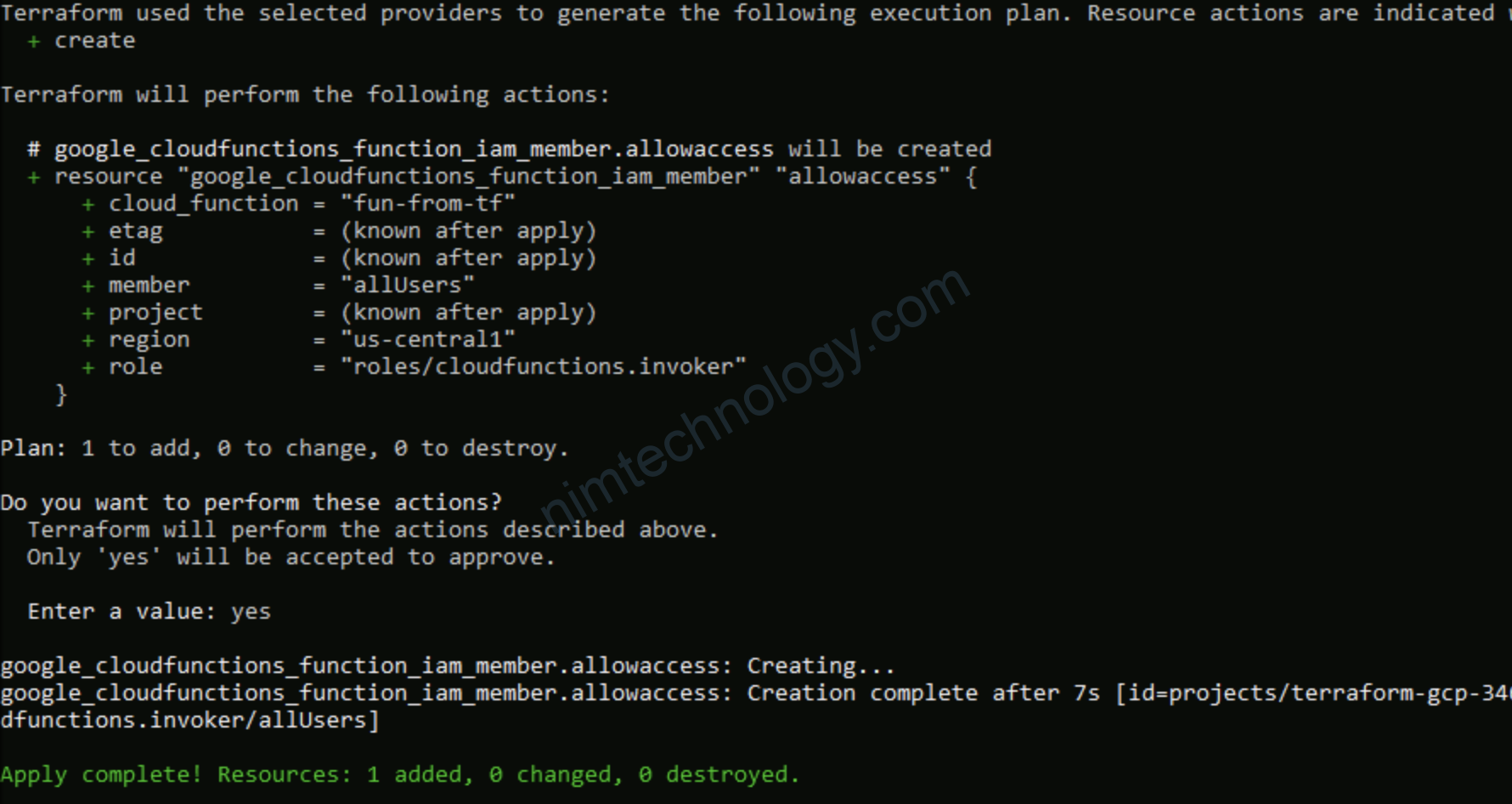
resource "google_cloudfunctions_function_iam_member" "allowaccess" {
region = google_cloudfunctions_function.fun_from_tf.region
cloud_function = google_cloudfunctions_function.fun_from_tf.name
role = "roles/cloudfunctions.invoker"
member = "allUsers"
}
2.1) Preparing
File index.js
/**
* Responds to any HTTP request.
*
* @param {!express:Request} req HTTP request context.
* @param {!express:Response} res HTTP response context.
*/
exports.helloWorldtf = (req, res) => {
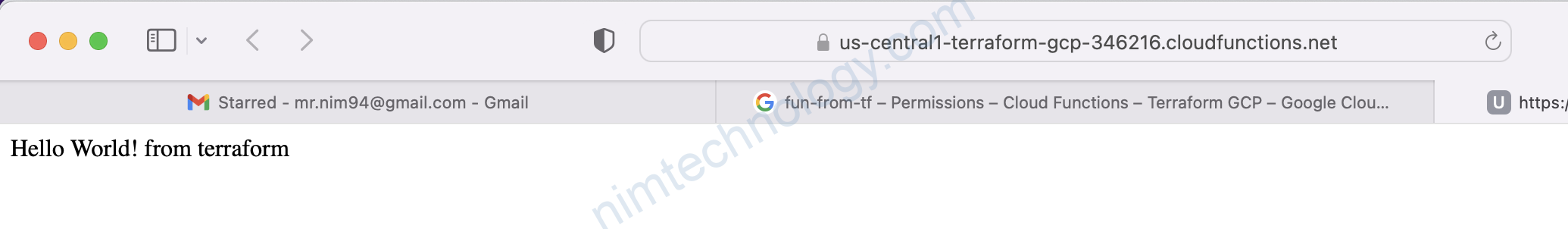
let message = req.query.message || req.body.message || 'Hello World! from terraform';
res.status(200).send(message);
};
Tiếp theo là file package.json
{
"name": "sample-http",
"version": "0.0.1"
}
Bạn sẽ cần nén nó lại dưới duôi .zip
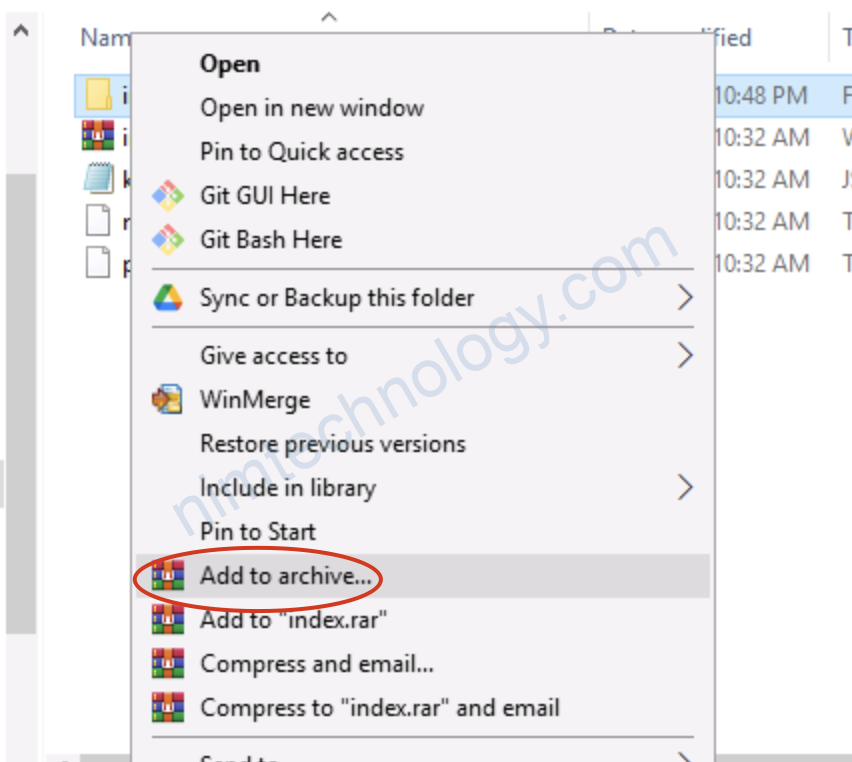
2.2) Create Bucket
Giờ file main.tf như dứoi:
resource "google_storage_bucket" "fun_bucket" {
name = "fun_bucket_nimtechnology_tf"
}
resource "google_storage_bucket_object" "srccode" {
name = "index.zip"
bucket = google_storage_bucket.fun_bucket.name
source = "index@local.zip"
}
source = "index@local.zip" : là file dưới local của bạnname = "index.zip": là name khi bạn đẩy lên bucket gcp
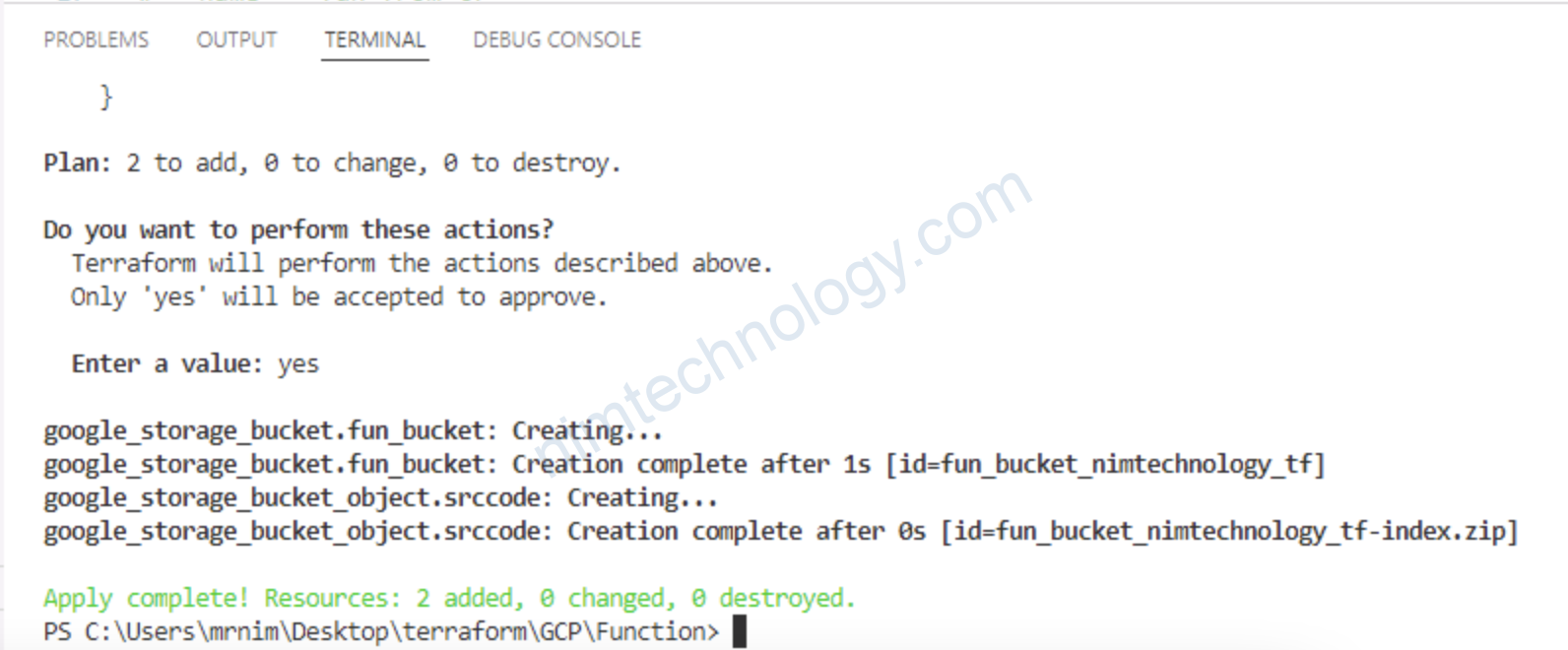
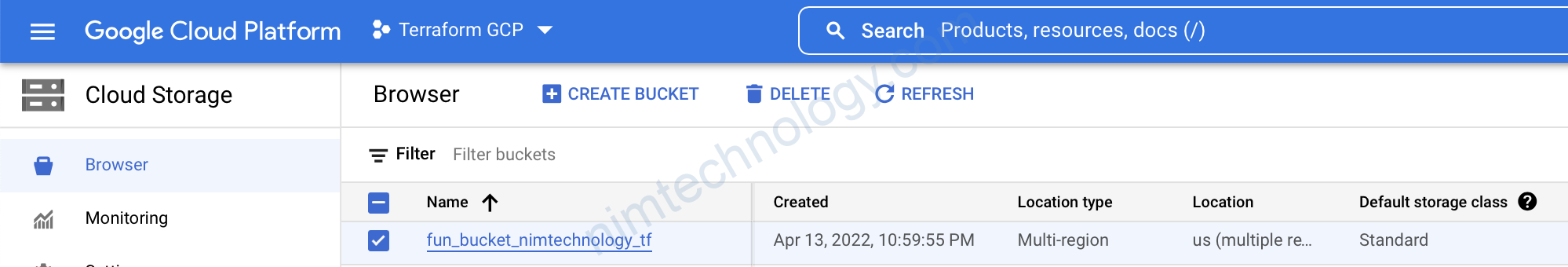
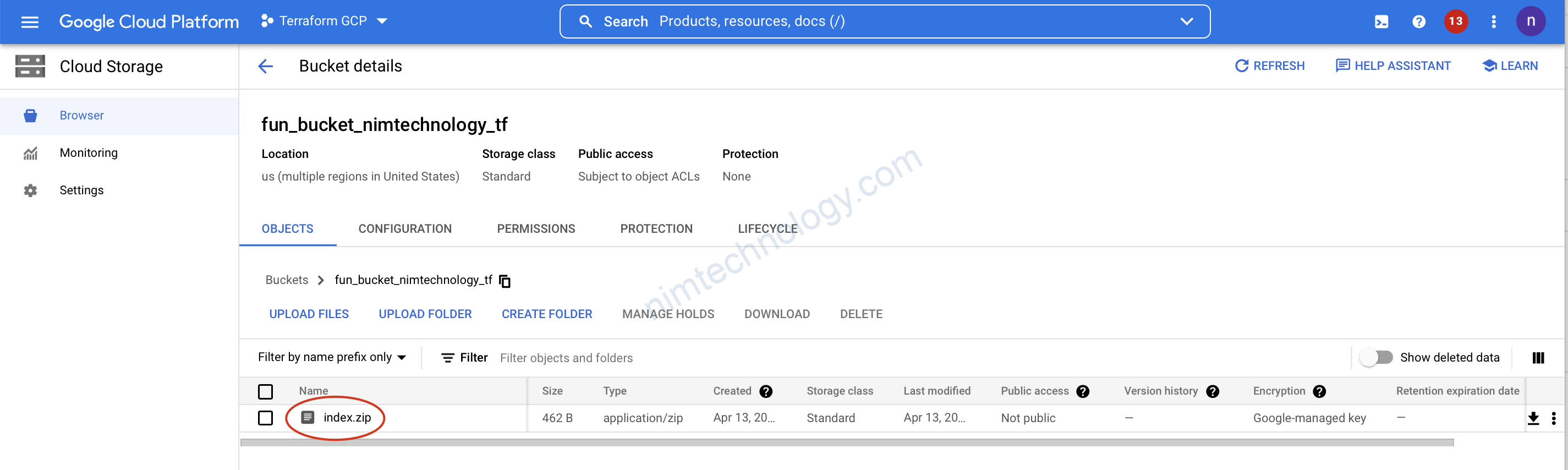
2.3) Deploy Function
Giờ chúng ta đã có file trên bucket rồi thì deploy function thôi.
resource "google_storage_bucket" "fun_bucket" {
name = "fun_bucket_nimtechnology_tf"
}
resource "google_storage_bucket_object" "srccode" {
name = "index.zip"
bucket = google_storage_bucket.fun_bucket.name
source = "index@local.zip"
}
resource "google_cloudfunctions_function" "fun_from_tf" {
name = "fun-from-tf"
runtime = "nodejs14"
description = "This is my first function from terraform script."
available_memory_mb = 128
source_archive_bucket = google_storage_bucket.fun_bucket.name
source_archive_object = google_storage_bucket_object.srccode.name
trigger_http = true
entry_point = "helloWorldtf"
}
Nhìn thế này các bạn cũng sẽ đoán đoán được chức năng của từng dòng.
Hiểu sâu ta lại lên terraform.
Giờ thì apply thôi!
Error: googleapi: Error 403: Permission ‘cloudfunctions.functions.create‘ denied on resource ‘projects/terraform-gcp-346216/locations/us-central1/functions/fun-from-tf’ (or resource may not exist)., forbidden
Bạn sẽ bị thiếu quyền giờ chúng ta vào role search
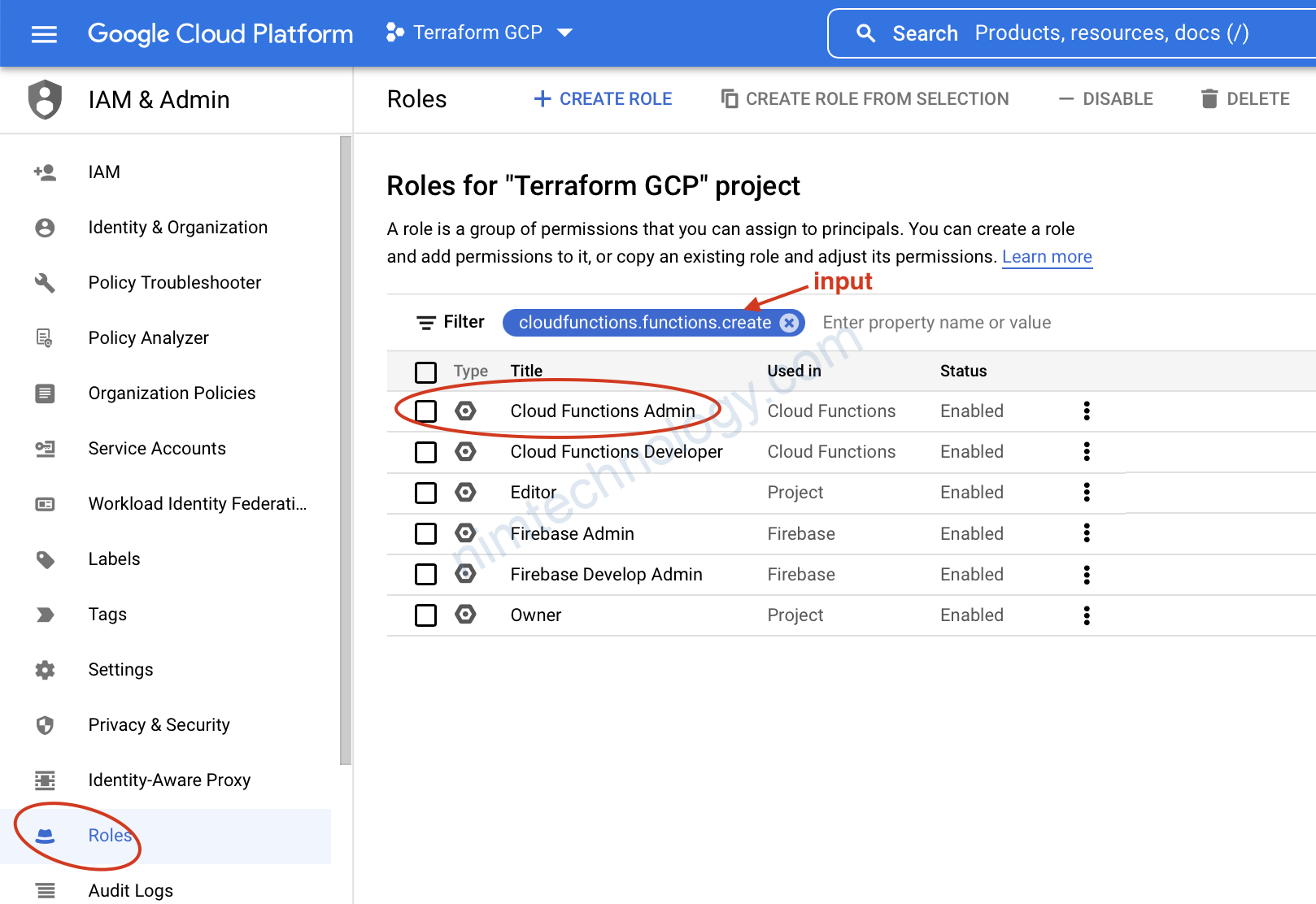
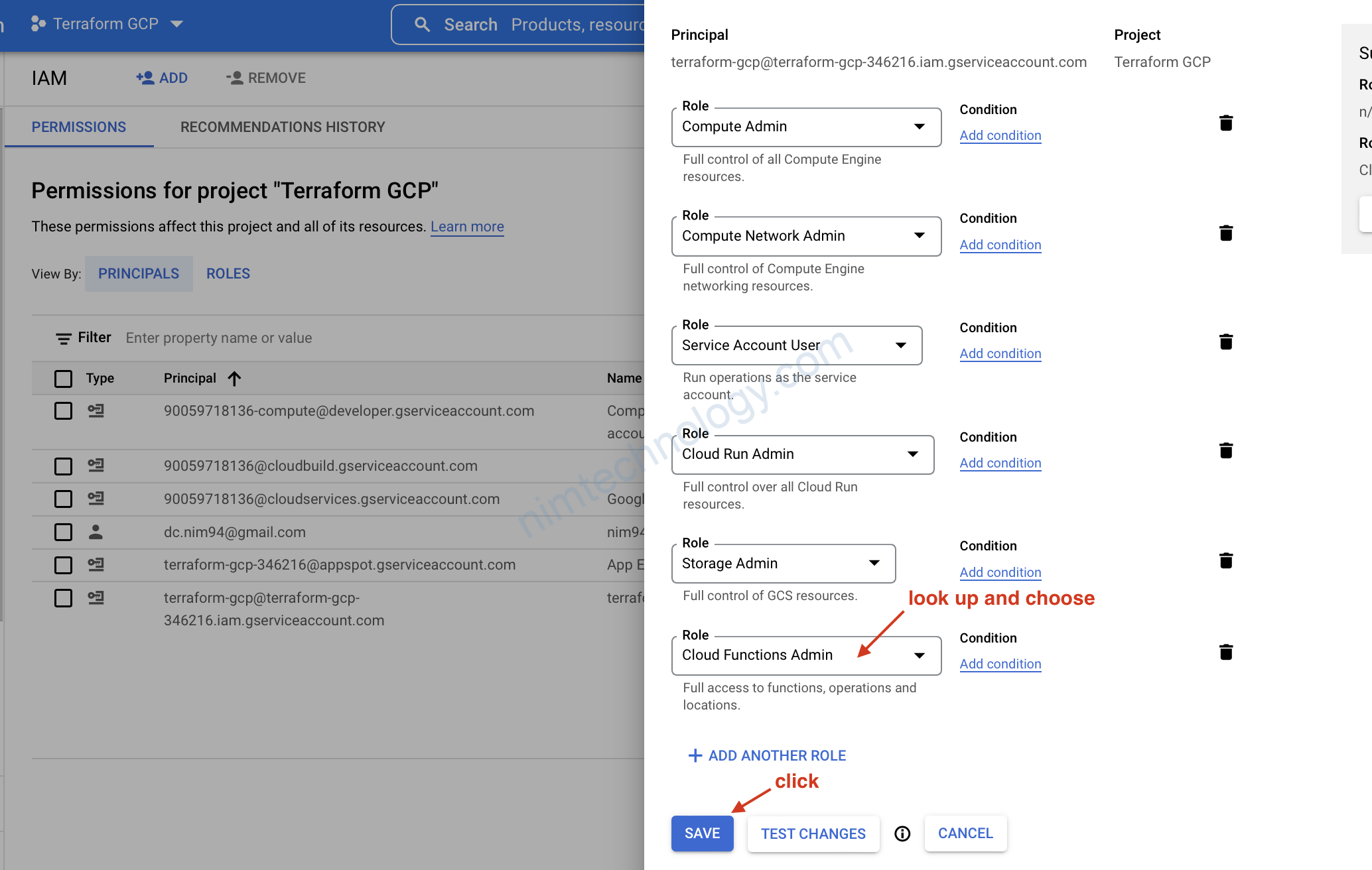
rồi chạy terraform apply lại
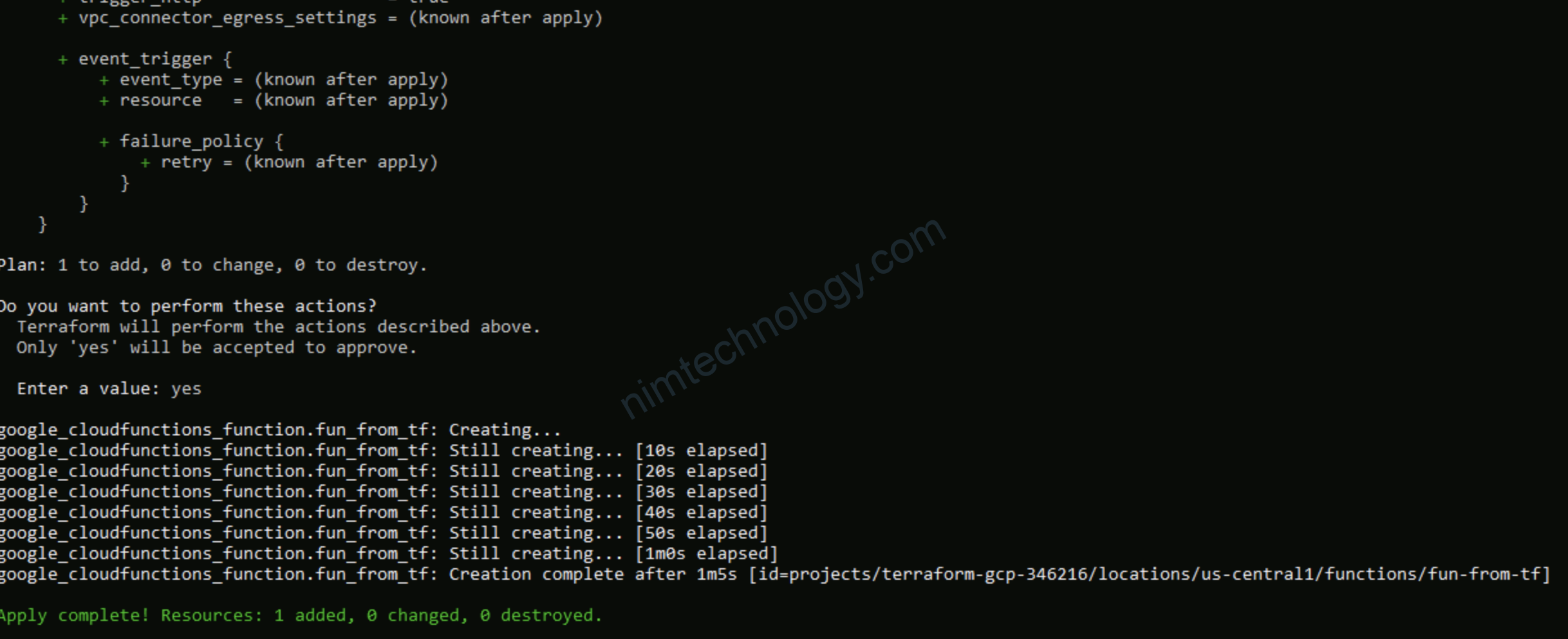
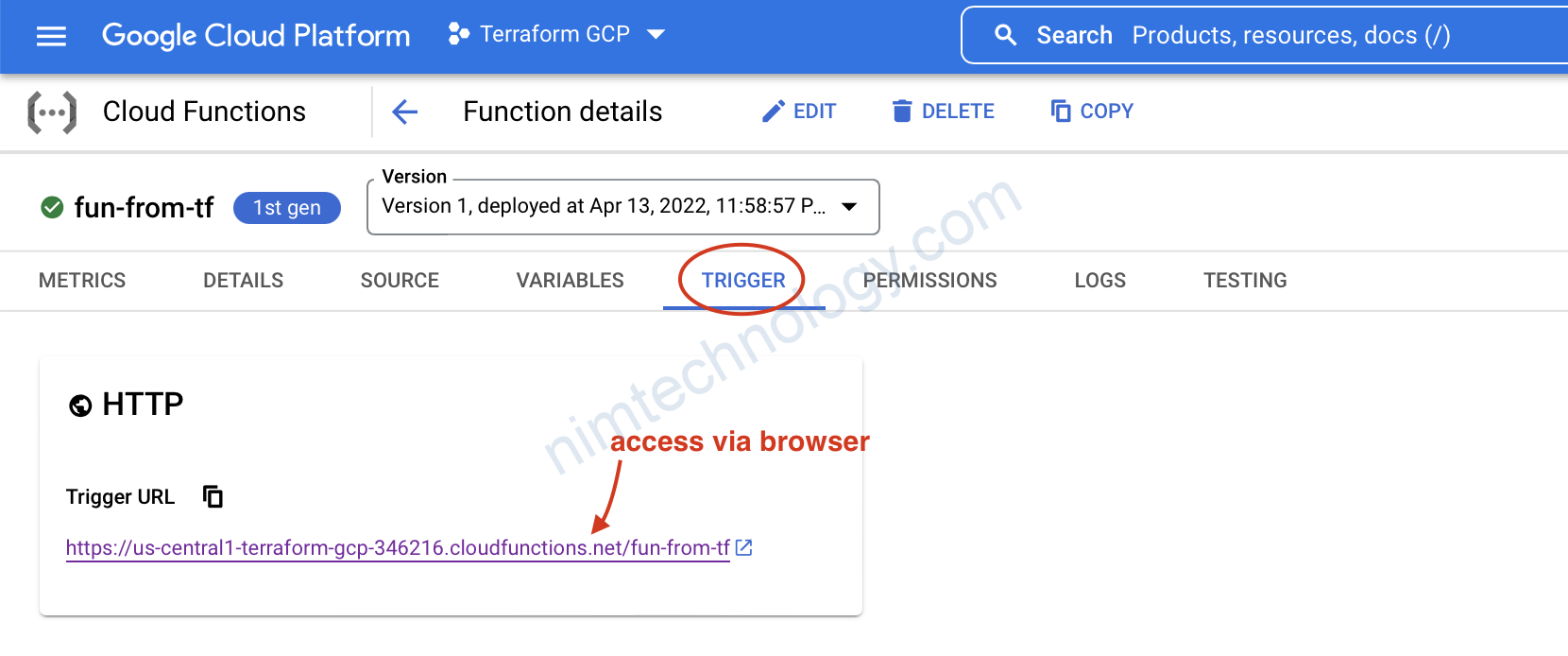
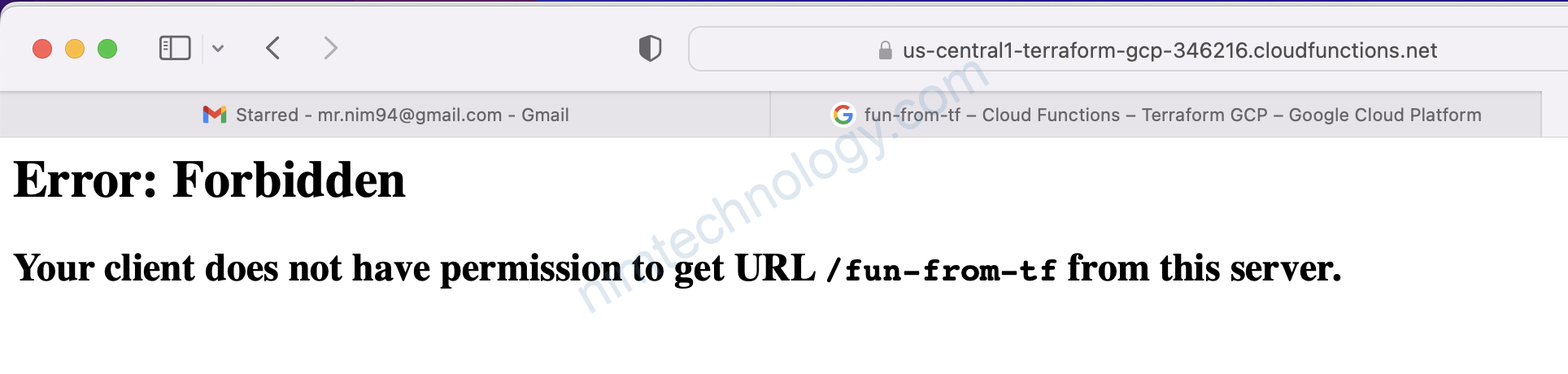
2.4) allow public access
resource "google_storage_bucket" "fun_bucket" {
name = "fun_bucket_nimtechnology_tf"
}
resource "google_storage_bucket_object" "srccode" {
name = "index.zip"
bucket = google_storage_bucket.fun_bucket.name
source = "index@local.zip"
}
resource "google_cloudfunctions_function" "fun_from_tf" {
name = "fun-from-tf"
runtime = "nodejs14"
description = "This is my first function from terraform script."
available_memory_mb = 128
source_archive_bucket = google_storage_bucket.fun_bucket.name
source_archive_object = google_storage_bucket_object.srccode.name
trigger_http = true
entry_point = "helloWorldtf"
}
resource "google_cloudfunctions_function_iam_member" "allowaccess" {
region = google_cloudfunctions_function.fun_from_tf.region
cloud_function = google_cloudfunctions_function.fun_from_tf.name
role = "roles/cloudfunctions.invoker"
member = "allUsers"
}
google_cloudfunctions_function_iam
Three different resources help you manage your IAM policy for Cloud Functions CloudFunction. Each of these resources serves a different use case:
google_cloudfunctions_function_iam_policy: Authoritative. Sets the IAM policy for the cloudfunction and replaces any existing policy already attached.google_cloudfunctions_function_iam_binding: Authoritative for a given role. Updates the IAM policy to grant a role to a list of members. Other roles within the IAM policy for the cloudfunction are preserved.google_cloudfunctions_function_iam_member: Non-authoritative. Updates the IAM policy to grant a role to a new member. Other members for the role for the cloudfunction are preserved.
Trước khi apply thì show permission để chúng ta cũng so sánh
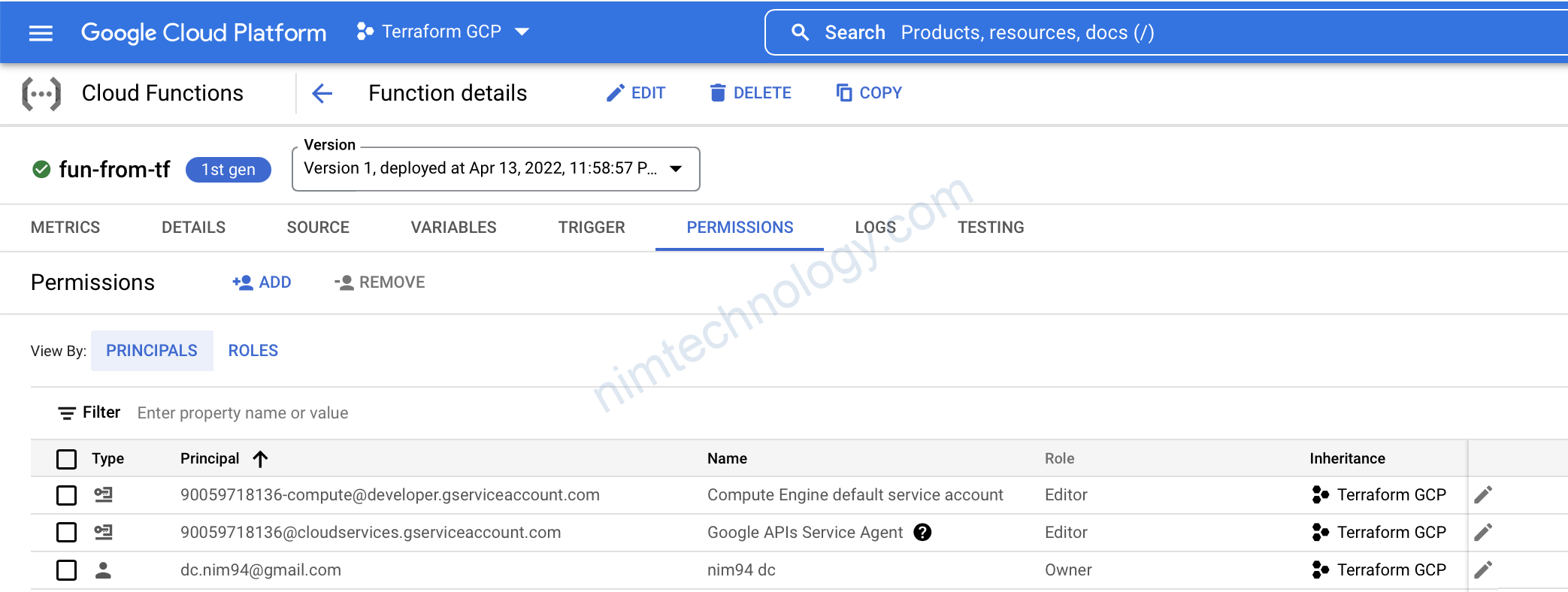
Sau khi apply