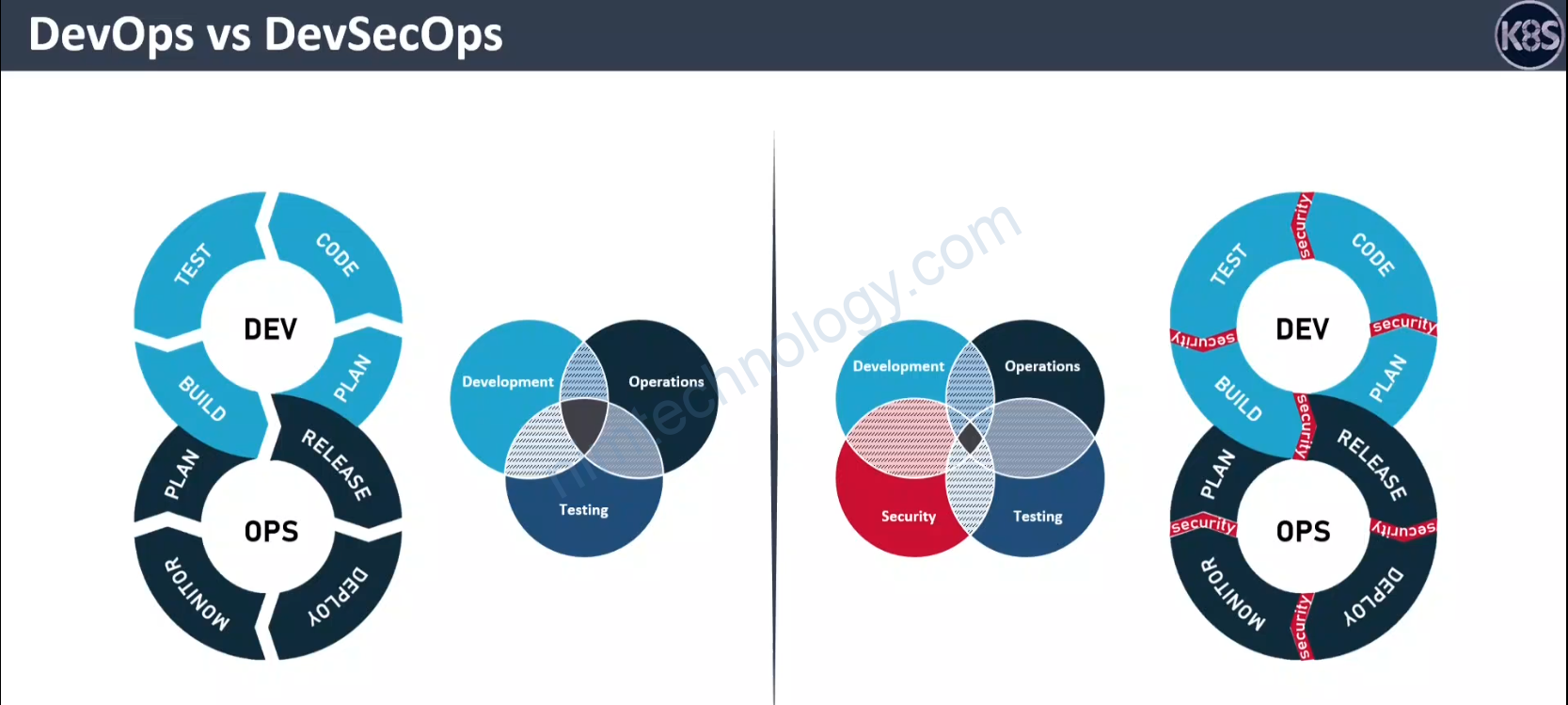
Chúng ta có 1 bài post.
https://www.theregister.com/2015/01/06/dev_blunder_shows_github_crawling_with_keyslurping_bots/
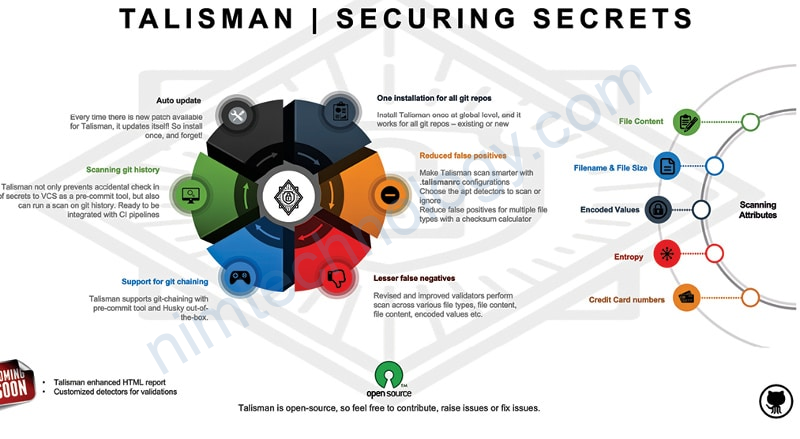
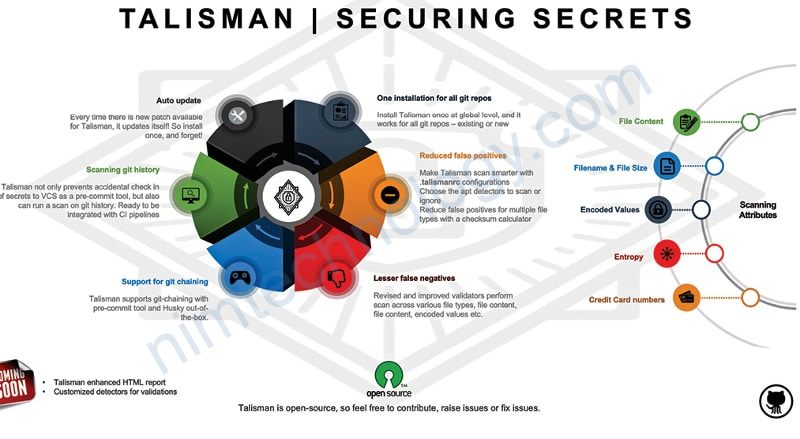
Git Hooks and Talisman Introduction




HandsOn – Talisman

thực hiện kiểm tra hook trong code dưới laptop.
ls -ltr .git/hooks/

Thực hiện cài đặt Talisman trên máy của bạn

Bạn thấy pre-push sẽ được thê trong hook của git

Bạn có thể setup scankhi commit.


Khi bạn thúc hiện commit thì talisman sẽ scan repo trước khi commit
root@controlplane kubernetes-devops-security on master [?] is 📦 v0.0.1 via ☕ v11.0.16 ➜ git add . root@controlplane kubernetes-devops-security on master [+] is 📦 v0.0.1 via ☕ v11.0.16 ➜ git commit -m "Hoc DevSecOps" Talisman Scan: 12 / 12 <------------------------------------------------------------------------------------------------------------------------------------------------------------------> 100.00% Talisman Report: +-----------------+------------------------------------------------------+----------+ | FILE | ERRORS | SEVERITY | +-----------------+------------------------------------------------------+----------+ | public/access | Expected file to not to contain | high | | | base64 encoded texts such as: | | | | base64encodedsecret=cGFzc3dvcmQtaXMtcXdlcnR5MTI... | | +-----------------+------------------------------------------------------+----------+ | public/access | Potential secret pattern : | low | | | base64encodedsecret=cGFzc3dvcmQtaXMtcXdlcnR5MTIzCg== | | | | | | +-----------------+------------------------------------------------------+----------+ | public/access | Potential secret pattern : | low | | | aws_access_key_id=VYEN23LCJGLTDPMSWQAL | | | | | | +-----------------+------------------------------------------------------+----------+ | public/access | Potential secret pattern : | high | | | aws_access_key_id= | | +-----------------+------------------------------------------------------+----------+ | public/info.txt | Potential secret pattern : | low | | | apikey=AizaSyCqhjgrPtr_La56sdUkjfav_laCqhjgrPtr_2s | | | | | | +-----------------+------------------------------------------------------+----------+ If you are absolutely sure that you want to ignore the above files from talisman detectors, consider pasting the following format in .talismanrc file in the project root fileignoreconfig: - filename: public/access checksum: d1ae8eb1f6393e04794a7b2b2eaf827e7d023465a60a1fbf0306957a8c0f59af - filename: public/info.txt checksum: 6243a12e75e189f4e89626324b2234cd4f63c25d3779212145e37c6f1e7a8138 version: "" Talisman done in 55.523949ms

root@controlplane kubernetes-devops-security on master [!+] is 📦 v0.0.1 via ☕ v11.0.16 ✖ git add . root@controlplane kubernetes-devops-security on master [+] is 📦 v0.0.1 via ☕ v11.0.16 ➜ git commit -m "Hoc DevSecOps v2" Talisman Scan: 12 / 12 <------------------------------------------------------------------------------------------------------------------------------------------------------------------> 100.00% Talisman Report: +-----------------+----------------------------------------------------+----------+ | FILE | ERRORS | SEVERITY | +-----------------+----------------------------------------------------+----------+ | public/info.txt | Potential secret pattern : | low | | | apikey=AizaSyCqhjgrPtr_La56sdUkjfav_laCqhjgrPtr_2s | | | | | | +-----------------+----------------------------------------------------+----------+ If you are absolutely sure that you want to ignore the above files from talisman detectors, consider pasting the following format in .talismanrc file in the project root fileignoreconfig: - filename: public/info.txt checksum: 6243a12e75e189f4e89626324b2234cd4f63c25d3779212145e37c6f1e7a8138 version: "" Talisman done in 15.157062ms


Chạy command:
https://praveen-alex-mathew.medium.com/running-talisman-cli-in-the-gitlab-ci-servers-29f15af7b1c7
https://www.digitalocean.com/community/tutorials/python-simplehttpserver-http-server
talisman --scan --ignoreHistoryRun talisman on Github Action.
https://github.com/carhartl/talisman-secrets-scan-action/blob/main/Dockerfile
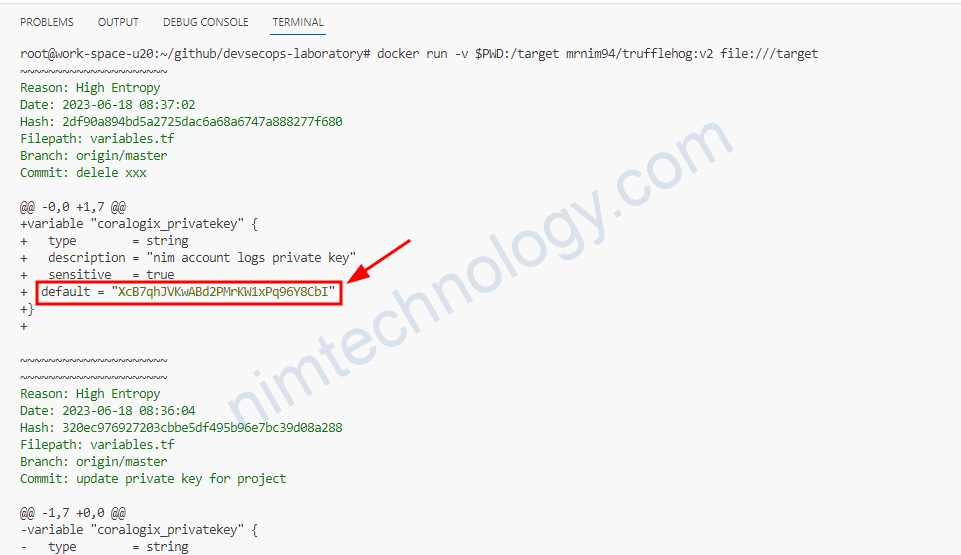
Run talisman on Docker
docker run -v ${PWD}/path:/mnt/data mrnim94/talisman:v1.31.0-release1 --scan